
Earlier this week, the Lapsus$ hacking group claimed that it had stolen 70GB of data from Globant, a Luxembourg-based IT and software development firm. Globant confirmed yesterday that the hackers did manage to breach its network and access some of its corporate customers’ source code without authorization.
“According to our current analysis, the information that was accessed was limited to certain source code and project-related documentation for a very limited number of clients. To date, we have not found any evidence that other areas of our infrastructure systems or those of our clients were affected. We are taking strict measures to prevent further incidents,” Globant explained yesterday.
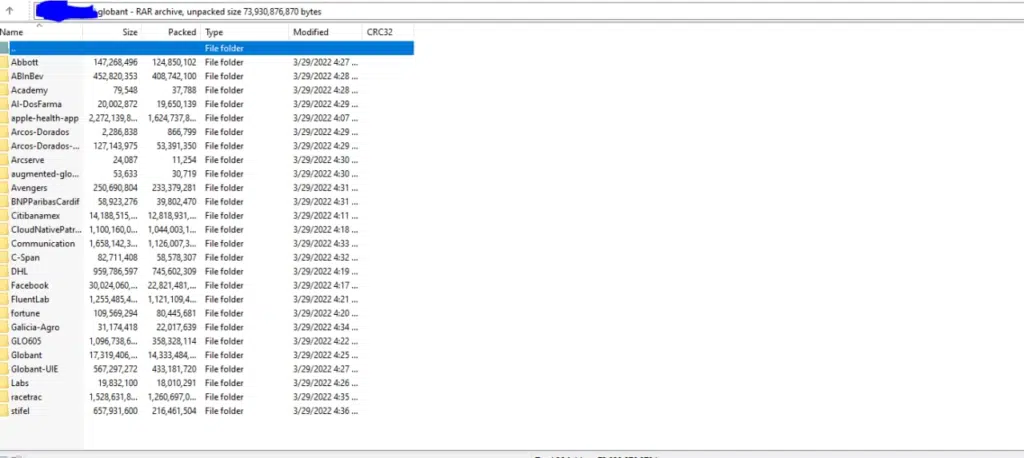
In a Telegram post, Lapsus$ shared a screenshot showing folders containing the source code of several companies presumed to be Globant clients. The list includes C-Span, Citibank, Abbott, and Facebook. In addition to the source code, the hacker group also shared a list of login credentials (with weak passwords) for some of Globant’s servers, including GitHub, Jira, Confluence, and Crucible.
The screenshots of the hacked data were shared by Malware research group VX-Underground on Twitter yesterday.
The London police arrested seven teenagers over Lapsus$ hacks
The Lapsus$ group has recently made the headlines for hacking some big technology companies, including Microsoft, Samsung, Nvidia, Okta, and Ubisoft. Lapsus$ hackers utilize several unsophisticated methods to target their victims. These techniques include SIM-swapping, social engineering, deploying password stealers, and bypassing multifactor-authentication systems.
The latest breach comes a few days after the London police arrested seven suspected members (aged between 16 to 21) of the Lapsus$ group. However, these hacking suspects were later released by the authorities. The FBI recently asked the public for help tracking the Lapsus$ members involved in the breach of US-based companies.
Microsoft recommends organizations to implement secure Multifactor authentication mechanisms to prevent cyber attacks from this hacker group. Meanwhile, the firm also advises customers to monitor their security posture and signs of intrusion in their security networks.


