How to Enable PowerShell Logging
- Blog
- PowerShell
- Post
What are some ways I can enable PowerShell logging?
PowerShell is a sophisticated management tool that can revolutionize the way you manage Windows Server. But with the power and capabilities that PowerShell has to offer also come risks. PowerShell logging is turned off by default, but there are two easy ways to enable logging so that you can get some insight into what commands are being executed and collect information for security forensics.
Enable logging from the command line
PowerShell logging is enabled per module. In this example I’ll show you how to enable logging for Active Directory cmdlets.
- Log on to Windows Server 2012 with local administrative privileges.
- Open a PowerShell window using the icon on the desktop Taskbar.
- Type Import-Module ActiveDirectory and press Enter.
- Type (Get-Module ActiveDirectory).LogPipelineExecutionDetails = $true and press Enter. To disable logging for the Active Directory module, you would simply exchange $true for $false.
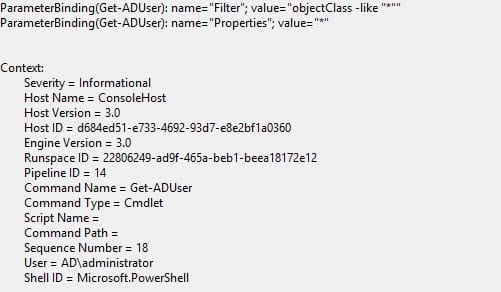
Now run an Active Directory cmdlet such as get-aduser –filter * -property *, and press Enter.
Once the cmdlet has returned a complete set of results, open Event Viewer from the Tools menu in Server Manager and expand Applications and Services Log, Microsoft, Windows, and PowerShell, then select the Operational log. You should see an event similar to that shown below, giving details of the command run, any specified parameters, and the user who executed the command.
Enable logging in Group Policy
If you want to enable logging on more than one server, it may be more convenient to use Group Policy to push out the necessary settings. In the Group Policy Management Editor, you can find the configuration settings for PowerShell under Computer Configuration, Policies, Administrative Templates, Windows Components, and Windows Powershell.
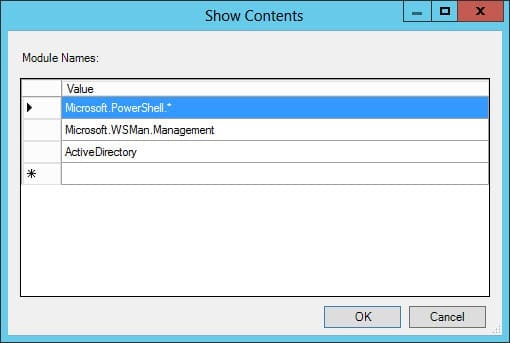
The Group Policy Object (GPO) setting you need is called Turn on Module Logging. You can see in the figure below that I’ve enabled logging for the core modules as suggested (Microsoft.PowerShell.* and Microsoft.WSMan.Management), and specifically for the Active Directory module. Enabling logging for the core modules gives more detail in the event log when running the get-aduser cmdlet, such as to which AD objects the command binds. Once you’ve configured the policy setting and made sure the GPO is linked to an OU, you should reboot the affected server(s).