Controlled Folder Access in Windows 10 FCU
In this Ask the Admin, I’ll explain how Controlled Folder Access can help protect users against ransomware.
Ransomware has been in the headlines a lot this year. WannaCry has been the most notable example, exploiting vulnerabilities in Windows that Microsoft had already patched. Automatic updates in Windows 10 left Microsoft’s latest version of Windows largely unaffected. Despite Windows 10’s resilience to WannaCry, Microsoft has added several features to Windows Defender in the Windows 10 Fall Creators Update to bolster security.
Windows Defender Exploit Guard replaces the Enhanced Mitigation Experience Toolkit (EMET) in Windows 10. Controlled Folder Access (CFA) is part of Exploit Guard and helps users and organizations protect folders, such as Documents, from malicious apps. CFA is disabled by default. However, users can enable it and receive better protection with the default settings. The protected folders list includes the Documents, Videos, Music, Favorites, and Pictures folders for all users. You can add your own folders to the list but the default folders cannot be removed. Most importantly, network shares can also be protected, although the use of wildcards is not supported.
Enable Controlled Folder Access
I enabled Controlled Folder Access on my main PC with the default settings. To enable CFA, open the Windows Defender Security Center, click Virus and threat protection and then Virus and threat protection settings. Scroll down the list of settings and set Controlled folder access to On.
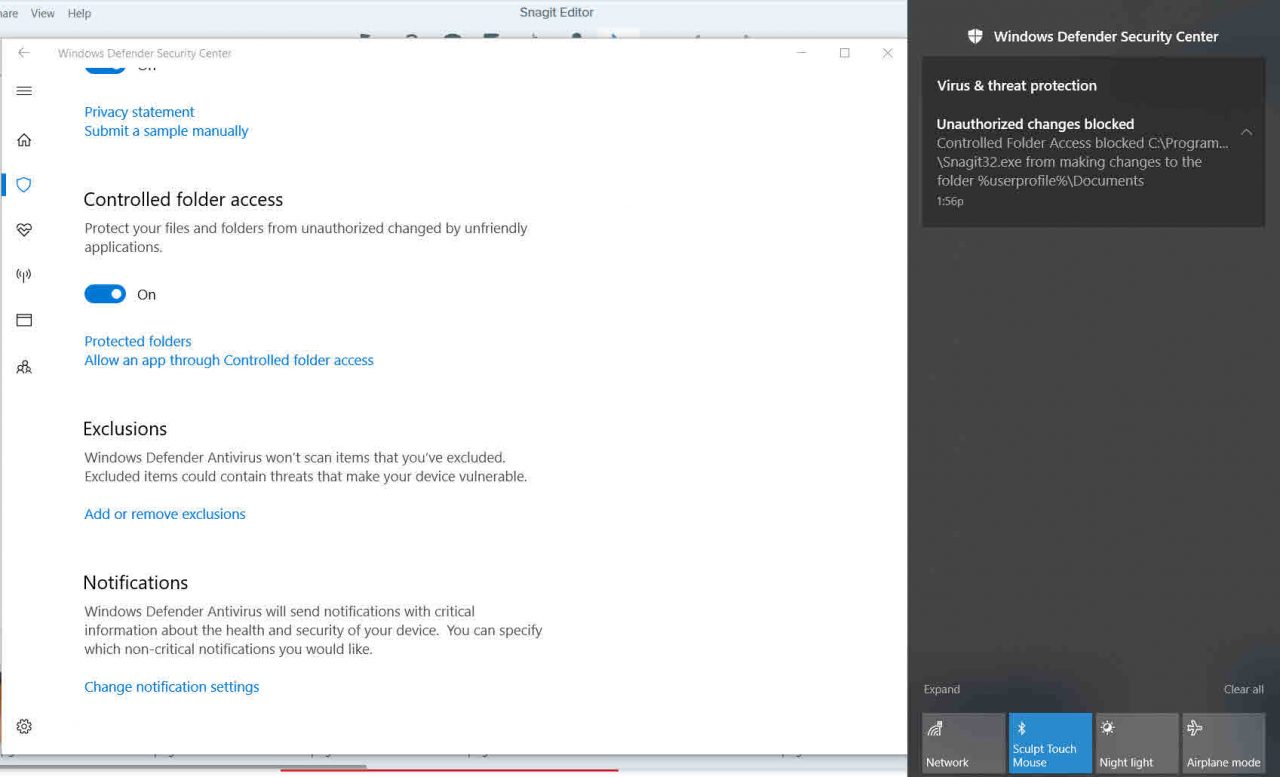
I received a warning immediately that a Snagit Editor had been blocked from making changes in my Documents folder. That wasn’t necessarily a good sign because if CFA has too many false positives, users will complain or turn off CFA. The Snagit works as it did before CFA was enabled but I still get warnings when trying to save images. So, I added it to the list of programs that are allowed through CFA.
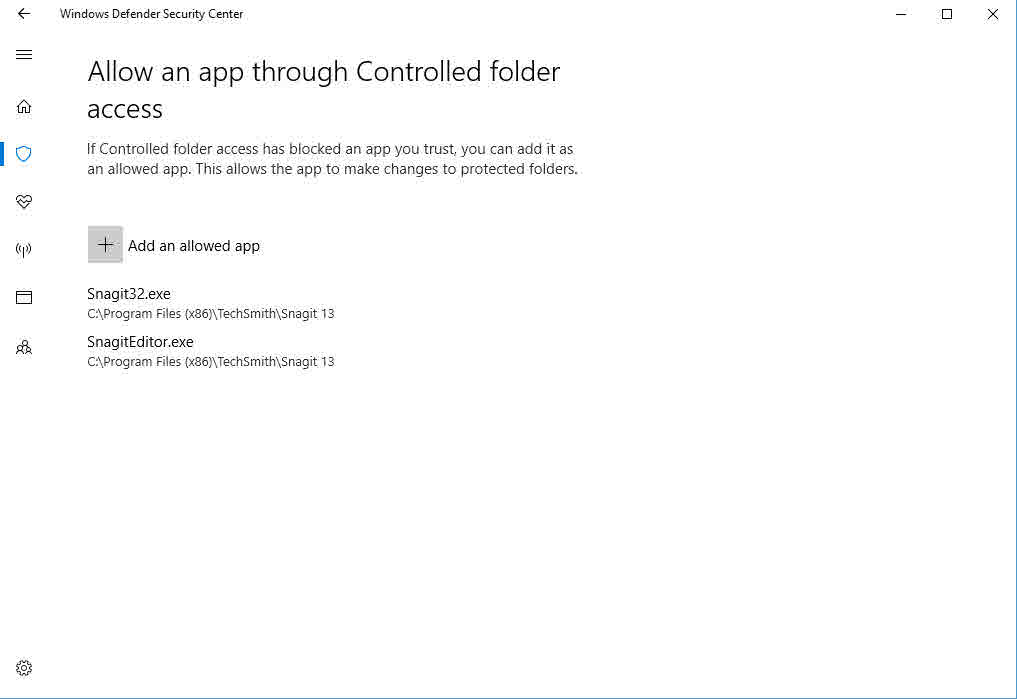
If an app you have installed doesn’t play nice with CFA, you can add it to a list of apps that are allowed through CFA. Microsoft doesn’t say exactly how CFA determines whether an app is trustworthy but CFA relies on the Windows Defender real-time antivirus scanning engine. If you are using a third-party antivirus solution, you won’t be able to use CFA. It’s also worth noting that users must have administrative permissions to enable CFA, make any changes to the protected folders list, and allow apps through CFA.
The good news is that CFA can be configured by system administrators using Group Policy. The settings for CFA can be found under Administrative Templates > Windows Components > Windows Defender Antivirus > Windows Defender Exploit Guard > Controlled folder access. CFA can also be configured using PowerShell, using the Set-MpPreference and Add-MpPreference cmdlets, and configuration service providers (CSPs) for Mobile Device Management (MDM).
Gimmick or Effective Security Defense?
Like any protection technology, CFA can be effective as part of a defense-in-depth strategy. For example, CFA’s ability to protect will be weakened if users have administrative rights on their devices. The Exploit Guard CFA File Creator tool is part the Exploit Guard Evaluation Package, which is a free download from Microsoft. You can use the tool to test the effectiveness of CFA. Some independent testing also shows that CFA was effective at defending protected folders against Locky, ransomware contained in a Microsoft Word document that has malicious macros. For more information on protecting against malicious macros, see Managing Macro Security in Office 2016 on Petri.
Controlled Folder Access is worth evaluating because it is very easy to configure and could help protect valuable data against ransomware. You should test it in your environment to determine whether any apps need to be allowed through CFA. At the end of the day, nothing is more important than a properly tested disaster recovery plan so that you can restore data should your defenses fail.
For more information on evaluating and configuring Controlled Folder Access, see Microsoft’s website here.




