How to Lock Down a Remote PowerShell with a Constrained Endpoint
- Blog
- PowerShell
- Post
How can I use constrained endpoints to lock down remote PowerShell access?
When considering whether to allow PowerShell to run on servers, security has been a concern for some system administrators. Despite its powerful and wide-reaching feature set, PowerShell was designed with security in mind from the bottom up, and it is the most secure means of managing Windows Server. In this article, I’m going to show you how to configure a constrained endpoint on Windows Server 2012 to make sure users can only perform a limited set of tasks when connecting to PowerShell remotely.
PowerShell remoting is enabled in Windows Server 2012 out-of-the-box, and by default only users with local administrator privileges can connect to the default endpoint. An endpoint is a set of configuration parameters that determine what permissions and features are available to users connecting to PowerShell across the network. Luckily, it’s possible to create your own custom endpoints. For instance, you might like to create an endpoint that allows helpdesk users to connect remotely to a server without local administrator permissions, and to restrict users to performing a limited set of tasks.
Create a New Endpoint
Login to your server with an account that has local administrator permissions and follow the instructions:
- Right-click the blue PowerShell icon on the desktop taskbar and select Run as Administrator from the menu.
- In the PowerShell console, type Get-PSSessionConfiguration and press Enter. This will show you all the existing endpoints on the server. You’ll see the microsoft.powershell endpoint requires users to be a member of the built-in Administrators or Remote Management Users group.
- To create a new endpoint for your helpdesk, type Register-PSSessionConfiguration -Name “Helpdesk” in the PowerShell window and press Enter. Type Y and press Enter to confirm the action.
- Type Y and press Enter again to confirm restarting the WinRM service.
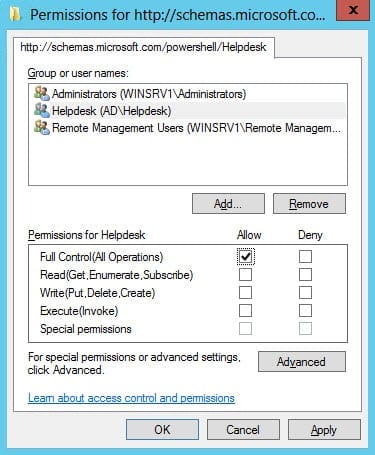
- Now we need to set permissions on the new endpoint. Type Set-PSSessionConfiguration –Name Helpdesk –ShowSecurityDescriptorUI and press Enter. Type Y and press Enter to confirm the action.
- A new window will appear allowing you to set permissions using the GUI. In this case I’m going to give an AD group called Helpdesk full access to the new endpoint. Click OK in the permissions dialog when you’re done.
- Type Y and press Enter again to confirm restarting the WinRM service.
- Type Get-PSSessionConfiguration and press Enter again, and you’ll see your new endpoint listed.
PowerShell is security transparent, so when users who are only a member of the Helpdesk group connect to the endpoint, they will only be able to perform tasks which their Windows permissions permit.
Connect to the new endpoint
To make a connection to the new endpoint, open PowerShell on a remote computer and type Enter-PSSession -ComputerName <servername> -ConfigurationName Helpdesk and press Enter, replacing <servername> with the name of the remote server where the new endpoint was created.