Azure AD System-Preferred Multifactor Authentication is Now Generally Available

Last year, Microsoft introduced the public preview of a system-preferred multifactor authentication (MFA) for Azure Active Directory (Azure AD). The company announced yesterday that the feature is now generally available for all commercial customers.
What is system-preferred MFA authentication?
With system-preferred authentication enabled, Azure AD evaluates all authentication methods registered for a user account, and selects the most secure option available for end users. As shown in the example below, the strongest authentication method is to approve a sign in request on Microsoft Authenticator. In this case, users won’t be able to select any other methods unless the app is unavailable.
“This system prompts the user to sign in with the most secure method they’ve registered and the method that’s enabled by admin policy. This will transition users from choosing a default method to use first to always using the most secure method available. If they can’t use the method they were prompted to use they can choose a different MFA method to sign in,” Microsoft explained.
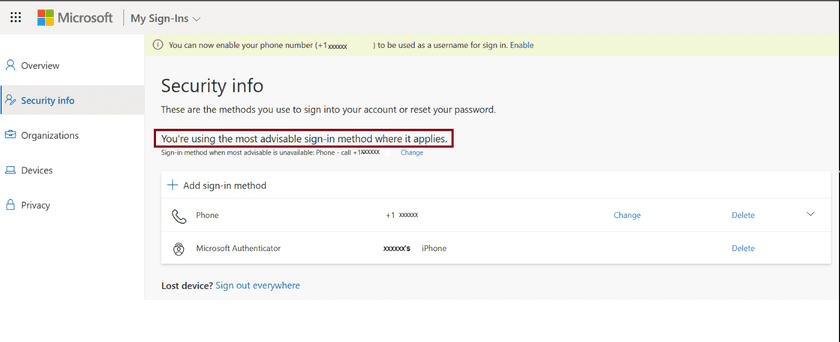
Microsoft explained that the system-preferred MFA feature dynamically chooses the most secure method for user authentication. The company updates the method based on the changes in the “security landscape.” The order of precedence of MFA methods is listed below:
- Temporary Access Pass
- Certificate-based authentication
- FIDO2 security key
- Microsoft Authenticator push notifications
- Time-based one-time password (TOTP)
- Telephony
Microsoft to enable system-preferred MFA by default in July
At launch, system-preferred MFA is enabled by default for all Azure AD customers. The company recommends IT admins to enable system-preferred multifactor authentication (MFA) via the Azure Portal or Graph APIs. However, it’s up to the IT Pros to disable the feature for end users in their tenants. Microsoft expects to enforce system-preferred authentication by default for all user accounts in July 2023.
Microsoft has also acknowledged a known issue with system-preferred multifactor authentication (MFA). Currently, the feature doesn’t provide support for FIDO2 security keys on mobile devices and certificate-based authentication (CBA). While Microsoft is working on a fix, it advises IT admins to create an excluded group to disable system-preferred MFA for these end users.



