August Patch Tuesday Updates Fix 121 Vulnerabilities and Improve Focus Assist

Microsoft has released yesterday the August 2022 Patch Tuesday updates for all supported versions of Windows. This time, the company fixed no less than 121 vulnerabilities in Windows, which is quite important for what is a usually quiet month
This month’s Patch Tuesday updates also bring improvements for the Focus Assist feature on Windows 11 and Windows 10. On Windows 11, Microsoft also added a new option for easily updating to the latest version of the OS at startup.
Critical vulnerabilities fixed in the August 2022 Patch Tuesday updates
Among the 121 Windows vulnerabilities Microsoft fixed this month, 17 of them rated critical and 102 of them rated important. Notably, two of these vulnerabilities are publicly known, and one of them is already being exploited in the wild.
Let’s have a look at some of the most important critical vulnerabilities Microsoft fixed this month:
- CVE-2022-34713: This Remote Code Execution (RCE) vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT) has been publicly disclosed and is already being exploited. The exploitation of the vulnerability requires that users open a specially crafted file.
- CVE-2022-30134: This Microsoft Exchange Server Elevation of Privilege vulnerability has also been publicly disclosed, but it’s not being exploited yet. According to Microsoft, Customers vulnerable to this issue would need to enable Extended Protection in order to prevent this attack, and you can find more details about that on the Exchange blog.
- CVE-2022-30133: This RCE vulnerability in the Windows Point-to-Point Protocol (PPP) could be exploited by an unauthenticated attacker sending a specially crafted connection request to a RAS server. Microsoft noted that this vulnerability can only be exploited by communicating via Port 1723. Organizations could protect themselves by blocking traffic through that port, though that could affect communications over their network.
- CVE-2022-35744: This is another RCE vulnerability in the Windows Point-to-Point Protocol (PPP). It can be exploited by an unauthenticated attacker sending a specially crafted connection request to a RAS server via the port 1723. Again, organizations can block traffic through that port to protect themselves before installing this update.
- CVE-2022-34691: This is an Active Directory Domain Services Elevation of Privilege vulnerability. It can be exploited by an authenticated attacker acquiring a certificate from Active Directory Certificate Services that would allow the elevation of privilege to the system.
- CVE-2022-35804: This SMB Client and Server RCE vulnerability can allow an attacker to execute code on the target system. Organizations can protect themselves by blocking the TCP port 445 at the enterprise perimeter firewall, or by securing SMB traffic in Windows Server.
Table 1 – August 2022 Patch Tuesday vulnerabilities
| Product | Impact | Max Severity | Article | Download | Details |
| Windows Server 2019 (Server Core installation) | Elevation of Privilege | Important | 5016623 | Security Update | CVE-2022-35771 |
| Windows Server 2019 | Elevation of Privilege | Important | 5016623 | Security Update | CVE-2022-35771 |
| Windows 10 Version 1809 for ARM64-based Systems | Elevation of Privilege | Important | 5016623 | Security Update | CVE-2022-35771 |
| Windows 10 Version 1809 for x64-based Systems | Elevation of Privilege | Important | 5016623 | Security Update | CVE-2022-35771 |
| Windows 10 Version 1809 for 32-bit Systems | Elevation of Privilege | Important | 5016623 | Security Update | CVE-2022-35771 |
| Microsoft Office 2013 Service Pack 1 (32-bit editions) | Remote Code Execution | Important | 4462142 | Security Update | CVE-2022-34717 |
| Microsoft Office 2013 Service Pack 1 (64-bit editions) | Remote Code Execution | Important | 4462142 | Security Update | CVE-2022-34717 |
| Microsoft Office 2013 RT Service Pack 1 | Remote Code Execution | Important | 4462142 | Security Update | CVE-2022-34717 |
| Microsoft Office 2016 (32-bit edition) | Remote Code Execution | Important | 4462148 | Security Update | CVE-2022-34717 |
| Windows Server 2016 (Server Core installation) | Elevation of Privilege | Important | 5016622 | Security Update | CVE-2022-35768 |
| Windows Server 2016 | Elevation of Privilege | Important | 5016622 | Security Update | CVE-2022-35768 |
| Windows 10 Version 1607 for x64-based Systems | Elevation of Privilege | Important | 5016622 | Security Update | CVE-2022-35768 |
| Windows 10 Version 1607 for 32-bit Systems | Elevation of Privilege | Important | 5016622 | Security Update | CVE-2022-35768 |
| Windows 10 for x64-based Systems | Elevation of Privilege | Important | 5016639 | Security Update | CVE-2022-35768 |
| Windows 10 for 32-bit Systems | Elevation of Privilege | Important | 5016639 | Security Update | CVE-2022-35768 |
| Windows 10 Version 21H2 for x64-based Systems | Elevation of Privilege | Important | 5016616 | Security Update | CVE-2022-35768 |
| Windows 10 Version 21H2 for ARM64-based Systems | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows 10 Version 21H2 for 32-bit Systems | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows 11 for ARM64-based Systems | Remote Code Execution | Critical | 5016629 | Security Update | CVE-2022-35766 |
| Windows 11 for x64-based Systems | Remote Code Execution | Critical | 5016629 | Security Update | CVE-2022-35766 |
| Windows Server, version 20H2 (Server Core Installation) | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows 10 Version 20H2 for ARM64-based Systems | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows 10 Version 20H2 for 32-bit Systems | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows 10 Version 20H2 for x64-based Systems | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows Server 2022 (Server Core installation) | Remote Code Execution | Critical | 5016627 | Security Update | CVE-2022-35766 |
| Windows Server 2022 | Remote Code Execution | Critical | 5016627 | Security Update | CVE-2022-35766 |
| Windows 10 Version 21H1 for 32-bit Systems | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows 10 Version 21H1 for ARM64-based Systems | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows 10 Version 21H1 for x64-based Systems | Remote Code Execution | Critical | 5016616 | Security Update | CVE-2022-35766 |
| Windows 8.1 for 32-bit systems | Elevation of Privilege | Important | 5016681 | Monthly Rollup | CVE-2022-35760 |
| Windows 8.1 for 32-bit systems | Elevation of Privilege | Important | 5016683 | Security Only | CVE-2022-35760 |
| Windows 8.1 for x64-based systems | Elevation of Privilege | Important | 5016681 | Monthly Rollup | CVE-2022-35754 |
| Windows 8.1 for x64-based systems | Elevation of Privilege | Important | 5016683 | Security Only | CVE-2022-35754 |
| Microsoft Office 2016 (64-bit edition) | Remote Code Execution | Important | 4462148 | Security Update | CVE-2022-34717 |
| Microsoft 365 Apps for Enterprise for 32-bit Systems | Remote Code Execution | Important | Click to Run | Security Update | CVE-2022-34717 |
| Microsoft Office LTSC 2021 for 32-bit editions | Remote Code Execution | Important | Click to Run | Security Update | CVE-2022-34717 |
| Microsoft Office LTSC 2021 for 64-bit editions | Remote Code Execution | Important | Click to Run | Security Update | CVE-2022-34717 |
| Microsoft 365 Apps for Enterprise for 64-bit Systems | Remote Code Execution | Important | Click to Run | Security Update | CVE-2022-34717 |
| Microsoft Office 2019 for 64-bit editions | Remote Code Execution | Important | Click to Run | Security Update | CVE-2022-34717 |
| Microsoft Office 2019 for 32-bit editions | Remote Code Execution | Important | Click to Run | Security Update | CVE-2022-34717 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5016681 | Monthly Rollup | CVE-2022-35795 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5016683 | Security Only | CVE-2022-35795 |
| Windows RT 8.1 | Elevation of Privilege | Important | 5016618 | IE Cumulative | CVE-2022-35768 |
| Windows 7 for x64-based Systems Service Pack 1 | Elevation of Privilege | Important | 5016676 | Monthly Rollup | CVE-2022-35768 |
| Windows 7 for x64-based Systems Service Pack 1 | Elevation of Privilege | Important | 5016679 | Security Only | CVE-2022-35768 |
| Windows 7 for 32-bit Systems Service Pack 1 | Elevation of Privilege | Important | 5016676 | Monthly Rollup | CVE-2022-35768 |
| Windows 7 for 32-bit Systems Service Pack 1 | Elevation of Privilege | Important | 5016679 | Security Only | CVE-2022-35768 |
| Azure Site Recovery VMWare to Azure | Remote Code Execution | Important | Security Update | CVE-2022-35772 | |
| Windows Server 2019 | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows 10 Version 1809 for ARM64-based Systems | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows 10 Version 1809 for x64-based Systems | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows 10 Version 1809 for 32-bit Systems | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Azure Real Time Operating System GUIX Studio | Remote Code Execution | Important | More Information | Security Update | CVE-2022-35779 |
| Windows Server 2012 R2 | Elevation of Privilege | Important | 5016681 | Monthly Rollup | CVE-2022-35795 |
| Windows Server 2012 R2 | Elevation of Privilege | Important | 5016683 | Security Only | CVE-2022-35795 |
| Windows Server 2012 (Server Core installation) | Elevation of Privilege | Important | 5016672 | Monthly Rollup | CVE-2022-35795 |
| Windows Server 2012 (Server Core installation) | Elevation of Privilege | Important | 5016684 | Security Only | CVE-2022-35795 |
| Windows Server 2012 | Elevation of Privilege | Important | 5016672 | Monthly Rollup | CVE-2022-35795 |
| Windows Server 2012 | Elevation of Privilege | Important | 5016684 | Security Only | CVE-2022-35795 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) | Elevation of Privilege | Important | 5016676 | Monthly Rollup | CVE-2022-35795 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) | Elevation of Privilege | Important | 5016679 | Security Only | CVE-2022-35795 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 | Elevation of Privilege | Important | 5016676 | Monthly Rollup | CVE-2022-35795 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 | Elevation of Privilege | Important | 5016679 | Security Only | CVE-2022-35795 |
| Windows Server 2008 for x64-based Systems Service Pack 2 | Elevation of Privilege | Important | 5016669 | Monthly Rollup | CVE-2022-35768 |
| Windows Server 2008 for x64-based Systems Service Pack 2 | Elevation of Privilege | Important | 5016686 | Security Only | CVE-2022-35768 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) | Elevation of Privilege | Important | 5016669 | Monthly Rollup | CVE-2022-35768 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) | Elevation of Privilege | Important | 5016686 | Security Only | CVE-2022-35768 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 | Elevation of Privilege | Important | 5016669 | Monthly Rollup | CVE-2022-35768 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 | Elevation of Privilege | Important | 5016686 | Security Only | CVE-2022-35768 |
| Microsoft Visual Studio 2015 Update 3 | Remote Code Execution | Important | 5016316 | Security Update | CVE-2022-35777 |
| Microsoft Visual Studio 2013 Update 5 | Remote Code Execution | Important | 5016315 | Security Update | CVE-2022-35777 |
| Microsoft Visual Studio 2012 Update 5 | Remote Code Execution | Important | 5016314 | Security Update | CVE-2022-35777 |
| Microsoft Visual Studio 2022 version 17.0 | Remote Code Execution | Important | Release Notes | Security Update | CVE-2022-35777 |
| Microsoft Visual Studio 2019 version 16.11 (includes 16.0 – 16.10) | Remote Code Execution | Important | Release Notes | Security Update | CVE-2022-35777 |
| Microsoft Visual Studio 2019 version 16.9 (includes 16.0 – 16.8) | Remote Code Execution | Important | Release Notes | Security Update | CVE-2022-35777 |
| Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) | Elevation of Privilege | Important | 5016669 | Monthly Rollup | CVE-2022-35793 |
| Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) | Elevation of Privilege | Important | 5016686 | Security Only | CVE-2022-35793 |
| Microsoft Visual Studio 2017 version 15.9 (includes 15.0 – 15.8) | Remote Code Execution | Important | Release Notes | Security Update | CVE-2022-35777 |
| Microsoft Visual Studio 2022 version 17.2 | Remote Code Execution | Important | Release Notes | Security Update | CVE-2022-35826 |
| Windows Server 2016 (Server Core installation) | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows Server 2019 (Server Core installation) | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows Server 2016 | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows 10 Version 1607 for x64-based Systems | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows 10 Version 1607 for 32-bit Systems | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows 10 for x64-based Systems | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows 10 for 32-bit Systems | Elevation of Privilege | Important | 5012170 | Security Update | CVE-2022-35820 |
| Windows 10 Version 21H1 for x64-based Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34303 |
| Microsoft Exchange Server 2016 Cumulative Update 22 | Information Disclosure | Important | 5015322 | Security Update | CVE-2022-34692 |
| Microsoft Exchange Server 2019 Cumulative Update 11 | Information Disclosure | Important | 5015322 | Security Update | CVE-2022-34692 |
| Azure Sphere | Information Disclosure | Important | Release Notes | Security Update | CVE-2022-35821 |
| Microsoft Exchange Server 2019 Cumulative Update 12 | Information Disclosure | Important | 5015322 | Security Update | CVE-2022-34692 |
| Microsoft Exchange Server 2016 Cumulative Update 23 | Information Disclosure | Important | 5015322 | Security Update | CVE-2022-34692 |
| Microsoft Outlook 2013 RT Service Pack 1 | Denial of Service | Important | 5001990 | Security Update | CVE-2022-35742 |
| Microsoft Outlook 2013 Service Pack 1 (64-bit editions) | Denial of Service | Important | 5001990 | Security Update | CVE-2022-35742 |
| Microsoft Outlook 2013 Service Pack 1 (32-bit editions) | Denial of Service | Important | 5001990 | Security Update | CVE-2022-35742 |
| Microsoft Outlook 2016 (64-bit edition) | Denial of Service | Important | 5002051 | Security Update | CVE-2022-35742 |
| Microsoft Outlook 2016 (32-bit edition) | Denial of Service | Important | 5002051 | Security Update | CVE-2022-35742 |
| .NET Core 3.1 | Spoofing | Important | 5016987 | Security Update | CVE-2022-34716 |
| .NET 6.0 | Spoofing | Important | 5016990 | Security Update | CVE-2022-34716 |
| System Center Operations Manager (SCOM) 2022 | Elevation of Privilege | Important | Github Repository | Security Update | CVE-2022-33640 |
| System Center Operations Manager (SCOM) 2016 | Elevation of Privilege | Important | Github Repository | Security Update | CVE-2022-33640 |
| System Center Operations Manager (SCOM) 2019 | Elevation of Privilege | Important | Github Repository | Security Update | CVE-2022-33640 |
| Azure Batch | Elevation of Privilege | Critical | Release Notes | Security Update | CVE-2022-33646 |
| Microsoft Office Online Server | Remote Code Execution | Important | 5002228 | Security Update | CVE-2022-33648 |
| Open Management Infrastructure | Elevation of Privilege | Important | Release Notes | Security Update | CVE-2022-33640 |
| Microsoft Excel 2013 Service Pack 1 (64-bit editions) | Security Feature Bypass | Important | 5002242 | Security Update | CVE-2022-33631 |
| Microsoft Excel 2013 Service Pack 1 (32-bit editions) | Security Feature Bypass | Important | 5002242 | Security Update | CVE-2022-33631 |
| Microsoft Excel 2013 RT Service Pack 1 | Security Feature Bypass | Important | 5002242 | Security Update | CVE-2022-33631 |
| Microsoft Excel 2016 (64-bit edition) | Security Feature Bypass | Important | 5002232 | Security Update | CVE-2022-33631 |
| Microsoft Excel 2016 (32-bit edition) | Security Feature Bypass | Important | 5002232 | Security Update | CVE-2022-33631 |
| Windows Server 2012 R2 (Server Core installation) | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows Server 2012 R2 | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows Server 2012 (Server Core installation) | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows Server 2012 | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows RT 8.1 | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 8.1 for x64-based systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 8.1 for 32-bit systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 10 Version 21H2 for x64-based Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 10 Version 21H2 for ARM64-based Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 10 Version 21H2 for 32-bit Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 10 Version 20H2 for ARM64-based Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 10 Version 20H2 for 32-bit Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 10 Version 20H2 for x64-based Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 10 Version 21H1 for 32-bit Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Windows 10 Version 21H1 for ARM64-based Systems | Security Feature Bypass | Important | 5012170 | Security Update | CVE-2022-34302 |
| Microsoft Exchange Server 2013 Cumulative Update 23 | Information Disclosure | Important | 5015321 | Security Update | CVE-2022-30134 |
Quality and experience updates
With this month’s Patch Tuesday updates, Microsoft has introduced more granular controls for Focus Assist, the Windows 10 and Windows 11 feature that hides all notifications when it’s turned on. After installing this month’s update, Windows 10 and Windows 11 users will get a new option to allow the OS to show important notifications when Focus Assist is on.
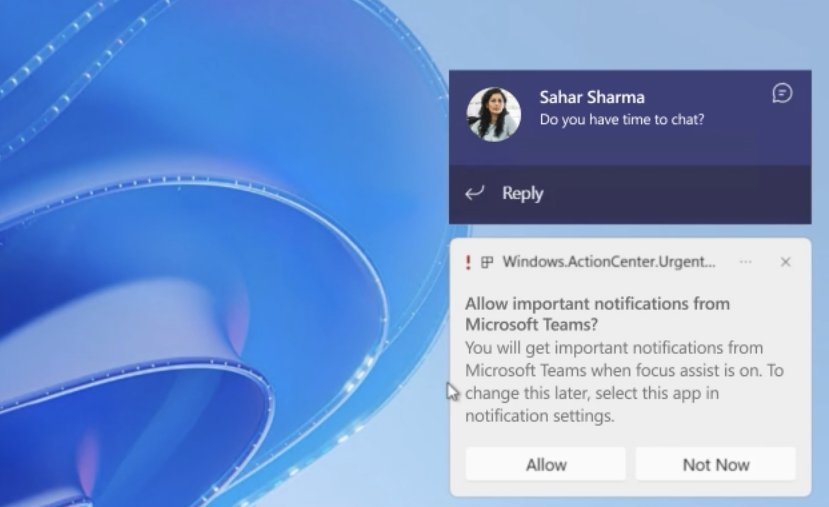
On Windows 11, Microsoft is also making it easy to update to a newer version of the OS at first startup. During the out-of-box experience, Windows 11 now offers the option to install a newer version of the OS (if available). If the user accepts, Windows 11 will update to the latest version of the OS right after the initial setup of the system is completed.
Lastly, Microsoft has addressed various bugs on Windows 11 this month. An issue causing File Explorer to stop working when users press the play and pause keys on their keyboard has been fixed. Microsoft has fixed a bug preventing some users to open troubleshooting tools on Windows 11.
Windows Update testing and best practices
Organizations looking to deploy this month’s patches should conduct thorough testing before deploying them widely on production systems. That said, applying the patches widely shouldn’t be delayed longer than necessary as hackers start to work out how to weaponize newly reported vulnerabilities.
A best practice is to make sure you have backed up systems before applying updates. Every month, users experience issues with Windows updates that lead to systems not booting, application and hardware compatibility issues, or even data loss in extreme cases.
There are backup tools built into Windows and Windows Server that you can use to restore systems in the event a patch causes a problem. The backup features in Windows can be used to restore an entire system, or files and folders on a granular basis.
If you have any problems with this month’s patches, please let us know in the comments below. Other readers might be able to share their experiences in how to roll back problematic updates or mitigate issues caused by patches that are important to have in place.



