What Is WSUS Dual Scan?
Windows Server Update Services (WSUS) is a Windows Server role that organizations use to manage and centralize distribution of updates. But the added flexibility of WSUS brings a layer of complexity which can sometimes cause problems, especially when combined with Windows Update.
Before I talk more about WSUS, it’s worth looking at Windows 10 and Windows Update for Business (WUfB). Microsoft says that WUfB is the future as it doesn’t require administrators to approve every update and relies on peer-to-peer technology to distribute updates between devices on a local area network (LAN). This fits in with Microsoft’s vision for delivering Windows 10 as a service.
For more details on WUfB, see Understanding Windows Update for Business and What Has Changed in Windows Update for Business on Petri.
But because many organizations also have Win32 in-house or third-party business apps, WUfB as it stands now can’t update that software. To address this issue, Microsoft introduced Dual Scan for the Windows Update (WU) client in Windows 10 version 1607. Dual Scan behavior is enabled automatically if the following Group Policies or Mobile Device Management (MDM) options are set:
- Specify intranet Microsoft update service location (i.e. WSUS)
- Either of the policies belonging to Windows Update for Business:
- Select when Feature Updates are received
- Select when Quality Updates are received
When Dual Scan is enabled, the WU client scans WSUS and WU, but it only downloads Windows patches from Microsoft’s update servers (Windows Update), effectively ignoring updates on WSUS servers in the ‘Windows’ product family.
Disable Dual Scan Policy Setting
Windows 10 users can manually click Check for updates in the Settings app, or the Check online for updates from Microsoft Update link, and a feature update could be applied to the device even if it wasn’t approved by IT. To prevent this happening, administrators often set the WUfB deferral policy to block feature updates installing as soon as they are released to Microsoft’s update servers. But setting the policy enables Dual Scan, and in the process, organizations lose control over the ability to approve quality updates via WSUS.
To address this situation, Microsoft added a new policy setting that can be enabled to stop Dual Scan being used if WUfB deferral policies are set in a WSUS environment.
Do not allow update deferral policies to cause scans against Windows Update
This setting allows organizations to configure WUfB and delay installation of feature updates while making sure the devices won’t scan Windows Update for quality updates.
Update Management Options
Confused yet? I don’t blame you. There are several approaches you can take to managing Windows Update.
Dual Scan
The Dual Scan option takes Windows updates from WU, and everything non-Windows from WSUS. Enabling the policy that I described above would break Dual Scan operation.
Classic WSUS
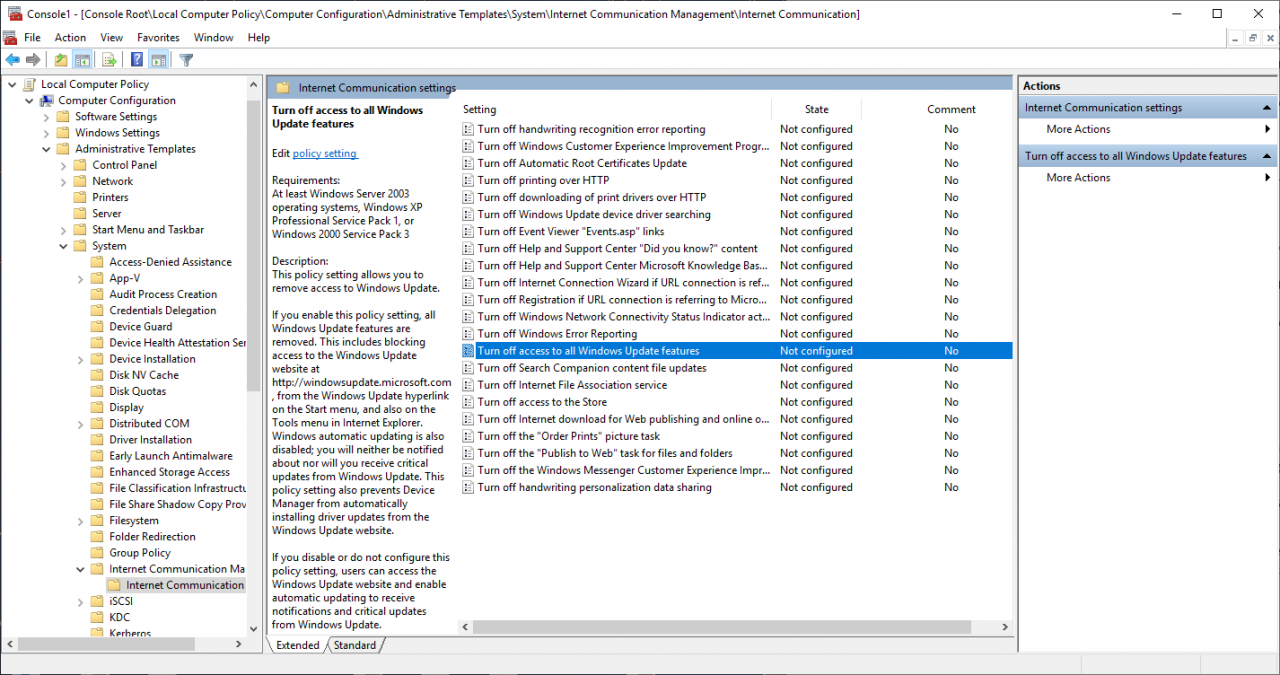
All updates come from WSUS and access to WU is blocked. Enabling the policy above wouldn’t have any effect in this scenario. To enable WSUS updates only, make sure that all Windows Update for Business options are set to Not Configured and that the Turn off access to all Windows Update features policy under System > Internet Communication Management > Internet Communication settings is Enabled.
Updates from Windows Update Only
Again, if you receive updates only from Windows Update, enabling the policy above won’t have any effect.
Windows Updates from WSUS, Feature Updates From WU
Here you approve quality updates using WSUS and leave users to perform ad hoc scans to get feature updates from Windows Update. Enabling the policy above will disable Dual Scan and your deferral policies will take affect when scanning against Windows Update. WSUS ignores all deferral polices.
If you’d like more detailed information on the policy settings available to control Windows updates and the Microsoft Store, there’s a good explanation here on TechNet. But as you can see from the information above, it’s important to understand when Dual Scan is enabled and that it might mean Windows 10 clients unexpectedly receive feature updates even when they haven’t been approved in WSUS.



