Understanding Windows 10 Always On VPN
Virtual private networks (VPN) are a common way of allowing remote users to securely access resources behind a perimeter network. And as more employees are being asked to work from home, organizations need to provide effective but secure remote access.
Microsoft Windows and Windows Server support a variety of different VPN technologies. The most advanced are DirectAccess and Windows 10 Always On VPN. In this article, I look at the advantages of Always On VPN over DirectAccess, and outline the infrastructure required to deploy Always On VPN.
Windows 10 Always On VPN replaces Microsoft DirectAccess
Microsoft DirectAccess is a VPN-like technology that works seamlessly for end users. It makes sure that client computers are always connected to the corporate network. But unlike traditional VPNs, users don’t need to establish a connection to a server using a client.
DirectAccess first appeared in Windows Server 2008 R2 for Windows 7 and Windows 8 Enterprise SKUs. Microsoft hasn’t committed to extending support for DirectAccess beyond the lifecycle of Windows Server 2019. It says that Windows 10 ‘Always On VPN’ should be used as a replacement for DirectAccess.
Windows 10 Always On VPN
‘Always On VPN’ has all the functionality of DirectAccess but it is easier to implement, manage, and has improved security. Always On VPN supports features like conditional access and system health checks using Network Policy Server (NPS). There is integration with Windows Hello for Business and Azure Multifactor Authentication, and much more.
How does Windows 10 Always On VPN work?
Always On VPN is a Windows 10-only technology. It requires the Windows 10 Anniversary Update (version 1607) or later. But in contrast to DirectAccess, Always On VPN is supported in Pro, Enterprise, and other Windows 10 SKUs. Windows 10 devices don’t need to be joined to Windows Server Active Directory (AD) but to take full advantage of Always ON VPN’s advanced features, devices should be joined to Azure AD.
Infrastructure independent
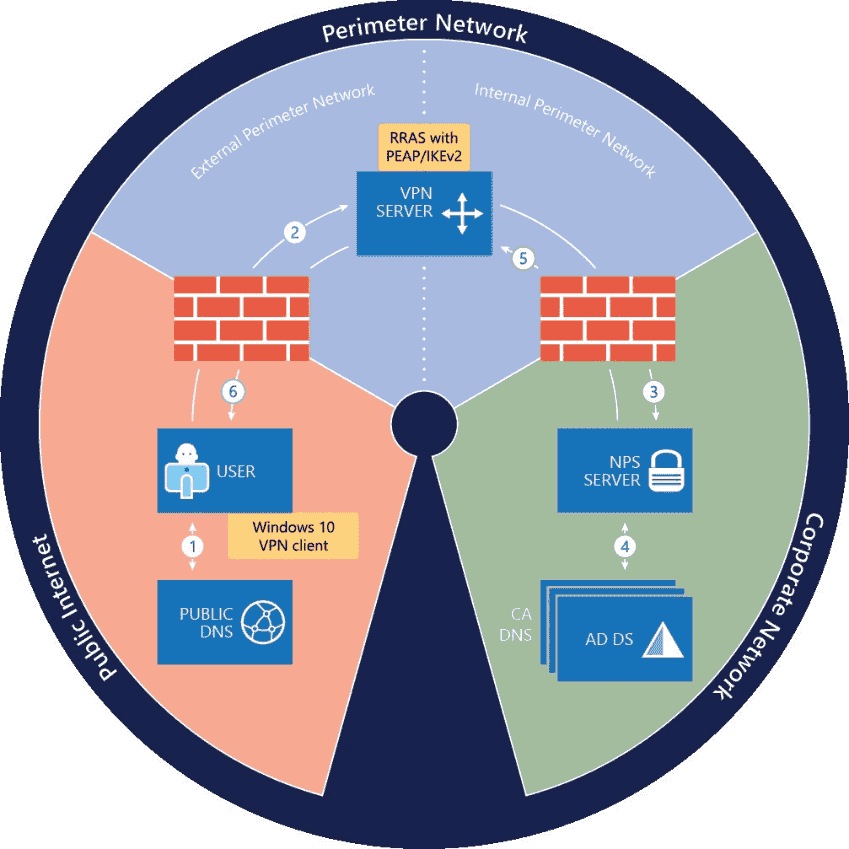
One of the great things about Always On VPN is that it doesn’t rely on a using Windows Server as a VPN device. Organizations can use Windows Server Routing and Remote Access (RRAS) or a third-party VPN solution. Authentication duties can be managed by Windows Server Network Policy Server (NPS) or a third-party RADIUS product.
The VPN device, whether it be Windows Server RRAS or a third-party product, needs to support IKEv2 and LAN routing. As the name suggests, Always On VPN is able to maintain a persistent connection between clients and the corporate network. IKEv2 can automatically restore connectivity if there is an interruption in network connectivity. But a disadvantage of IKEv2 is that it might be blocked by firewalls. VPN clients need outbound access on UDP ports 500 and 4500.
SSTP fallback
Always On VPN is designed to work with IKEv2. But Secure Socket Tunneling Protocol (SSTP) can be configured as a fallback protocol in cases where clients are unable to connect to the VPN device using IKEv2. SSTP transports Point-to-Point Protocol (PPP) through a secure channel using TCP port 433. This is the same port used for HTTPS, so it is always open outbound on firewalls.
But in practice, using SSTP as a fallback protocol with Always On VPN doesn’t work so well. SSTP isn’t as secure as IKEv2. And Always On VPN doesn’t support Device Tunnel when used with SSTP. Furthermore, the default behavior when VPN clients are configured to automatically choose a VPN protocol is to use SSTP.
Management
Always On VPN is designed to be managed with Mobile Device Management (MDM), specifically Microsoft Intune. But it is possible to use third-party MDM platforms or Microsoft Endpoint Configuration Manager, previously known as System Center Configuration Manager (SCCM). It isn’t possible to manage Always On VPN using Active Directory Group Policy.
Advanced features
There are some optional advanced features that you can use with Always On VPN.
- Traffic filtering
- App-triggered VPN
- Conditional access and device compliance
VPN Traffic Filters control which applications Windows 10 clients can access using Always On VPN. Routing policies are granular and allow organizations to control how line-of-business apps connect to the corporate network. IPv4 and IPv6 are both supported. There is no specific dependency on IPv6, which was a requirement for Microsoft DirectAccess. VPN Traffic Filters include app-based and traffic-based rules.
App-triggered VPN uses VPN profiles to trigger a connection only when certain applications, or types of application, start. Conditional access and device compliance can be deployed to require that devices managed by your organization meet certain requirements. Conditional access requires Azure Active Directory Premium.
There are many other improvements that come with Always On VPN. Including trusted network detection and device tunnel. Trusted network detection prevents VPN connectivity if the device is located on a trusted corporate network. Device Tunnel lets Windows 10 establish a VPN connection before user sign-in. User Tunnel and Device Tunnel are configured using independent VPN profiles and can be connected at the same time.
For a complete list of the improvements in Windows 10 Always On VPN, check out Microsoft’s website here.
Windows 10 Always On VPN is ideal for work from home
Always On VPN is a good option for organizations that want their employees to work from home. It is more secure than legacy VPN solutions, it doesn’t require users to manually ‘establish’ connections, it is easier to manage than DirectAccess, and it is more reliable on poor network connections. Organizations can also use Always On VPN with a third-party VPN device providing that it meets some basic requirements.
But if you want users to be able to work from anywhere, like cafes or hotel rooms, then the SSTP fallback option is less than ideal. Hopefully, Microsoft will address some of the issues with Always On VPN in future versions of Windows 10. But for now, before making a decision, think carefully about your goals and whether using two protocols with Always On VPN is going to work for your organization.