I’ve always liked to write a summary of what I thought the big takeaways were from every RSA Conference, partly as a way to collect my own thoughts, but primarily to give readers who couldn’t attend the conference a way to distill some of wisdom from the collective brain-trust of thousands of smart security professionals at the conference. I did the same last year in an article about the top security trends from RSA Conference 2013, and it’s always interesting to see what has changed over the last 12 months. So what were the hottest topics on the lips of IT security professionals at RSA Conference 2014? Read on for my take on what we should all be paying more attention to.
1. Snowden, the NSA, RSA Security, and TrustyCON
The biggest topic that everyone was talking about at RSA was the allegation — made by Reuters journalist Joseph Menn in December 2013 — that RSA Security had worked out a deal with the U.S. National Security Agency (NSA) to continue producing products based on their BSafe product, which the Reuters story claims used a flawed (and NSA-supplied) encryption algorithm. The news led to several security experts boycotting RSA, while others started up a rival security conference dubbed TrustyCon.
RSA Security Chairman Art Ciovello partially addressed the issue in his RSA Conference keynote, where he admitted that RSA worked with the NSA, but denied they had done anything wrong, telling attendees that “..has RSA done work with the NSA? Yes. But the fact has been a matter of public record for nearly a decade.” The rest of Coviello’s keynote focused on the need for more global standards concerning cyber security, and encouraged attendees to support the adoption of global cyber security principles.
While there’s no doubt there needs to be more international cooperation with cybersecurity, Coviello’s keynote was also a prime example of crisis PR messaging: The keynote was preceded by William Shatner beaming onto stage and belting out a security-oriented rendition of “Lucy in the Sky with Diamonds,” which put attendees in a jovial mood before Coviello walked on stage. And Coviello’s speech alternated between claiming that RSA Security was taken advantage of by the NSA, and embracing quotes and images from the late John F. Kennedy about the need for global computer security agreements and standards.
I’ll acknowledge that the NSA performs a vital role in helping keep the United States (and its allies and citizens) safe from cyberattack, but it’s also clear that the world is entering a brave new world of cyber warfare — from STUXNET to Snowden and beyond — where an “anything goes” mentality seems to apply. Former U.S. Government official Richard Clarke indirectly criticized both RSA Security and NSA during his keynote at the Cloud Security Alliance summit, saying that “…the US Government has to get out of the business of fu@$ing around with encryption standards.” For more on Clarke’s speech, check out John Fontana’s summary of the Coviello keynote over at his ZDNet Identity Matters blog.
William Shatner opens RSA Conference 2014 by singing an infosec-themed ‘Lucy in the Sky with Diamonds.’ (Source: YouTube)
2 . The Importance of Identity
With the advent and widespread adoption of cloud-based resources and mobile devices, the need for confirming someone’s real identity when they aren’t physically next to the resources they’re trying to access is an ongoing focus of attention for IT security experts and vendors. So how can a cloud provider really make sure that someone accessing data stored in their cloud is really who they say they are? Digital identities can be forged, and social engineering attacks can result in attackers effectively masquerading as senior executives who have access to everything. All of this has resulted in the continuing growth and development in Identity and Access Management (IAM) and Identity as a Service (IDaaS) practices and adoption, and the trends will likely continue. For more on identity trends, Sean Deuby over at Windows IT Pro has a nice summary of the latest developments in IT identity that is worth a read.
3. The IT Security Skills Shortage
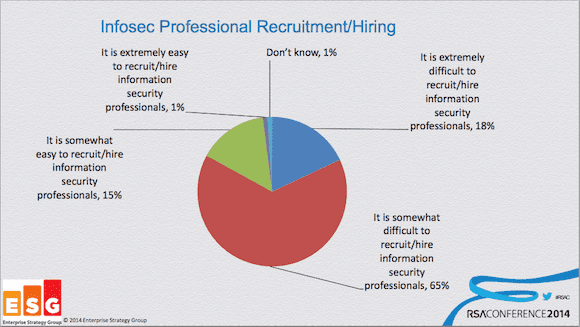
The IT security skills shortage visualized at RSA Conference 2014. (Image: John Oltsik/ESG)
A consistent theme that carried over from last year’s RSA conference is the ongoing shortage in IT security skills among IT professionals, and a gap between open positions for security positions and the applicants applying for them. Jon Oltsik, a senior principal analyst at the Enterprise Strategy Group (ESG), held a conference session that summed up the current security professional deficit in its headline: “The security staff and skills shortage is worse than you think.” Ostik referenced an ESG survey where IT hiring managers reveal that they’re finding it extremely (18%) or somewhat (65%) difficult to hire information security professionals. In an effort to turn things around, Ostik encouraged CISOs and IT manager to improve the work experience for information security professionals by automating mundane security tasks, implementing corporate security policies and getting support for those policies from senior management. Download a PDF of Oltsik’s RSA Conference presentation slides for more info.
4. Assume the Worst Case Scenario
With news of cyberattacks and corporate breaches now an almost daily occurrence, part of the new reality for information security professionals is to assume that just about every part of their IT environment has been (or soon will be) at risk. “Companies still have problems securing data once it leaves the security perimeter,” says Adrian Sanabria, a senior security analyst at 451 Research. “[You] almost need to assume that everything you have is compromised…even if you find a magic security solution, maybe you’ve already been hacked [before you obtained that solution].” Sanabria’s comments are sobering, but accurate: The best any security professional can do is to raise the bar of difficulty for attackers high enough to discourage all but the most determined attempts to breach IT security. Building on a base of solid security principles — such as keeping OSes patched and updated to the latest version, using firewalls, having clear and usable security policies that IT staff and employees all follow — you can make it more difficult for most attackers to gain access. Yet it’s also clear than given enough time, resources, and expertise, even the most hardened security environments can be compromised.
5. Cryptolocker Malware
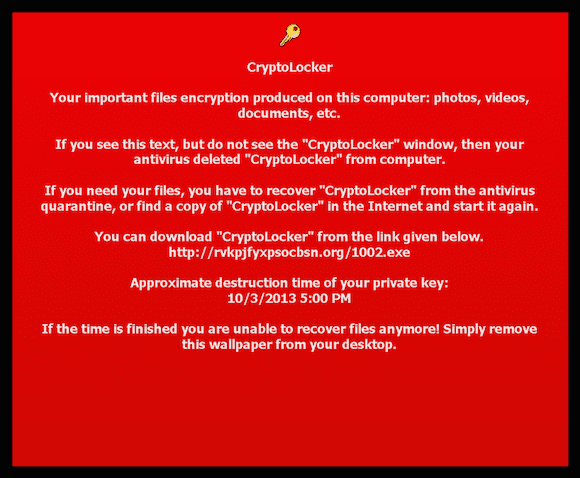
A message generated by Cryptolocker malware after encrypting files on a target computer. (Source: Andrew Brandt/Blue Coat Systems)
Another constant is that cyber criminals continue to relentlessly improve, refine, and evolve their attacks to stay one step ahead of existing IT security approaches. One such attack that is getting a lot of attention is Cryptolocker, a type of cyberattack that experts have dubbed “ransomware.” I spoke with Andrew Brandt from Blue Coat Systems at RSA, and he explained how Cryptolocker works. “It’s essentially extortion in the ‘give us the ransom or your data gets it’ variety.”
Brandt explained how it works: Using an email that is created to look like it comes from an official source — like from UPS, FedEx, or other well-known brand or government agency — users click on a link that either downloads the Cryptolocker malware directly, or sends the user to a website that then downloads the file. Once Cryptolocker is installed, it proceeds to encrypt all of the data on the hard drive of the local PC, then displays a message — possibly in the form of a Windows desktop image or pop-up windows — that tells the user that all of the data on their drive has been encrypted and is inaccessible, and the only way to unlock the data is to pay the attackers a fairly significant amount (like $300) to unlock the encrypted content and gain access. If the user refuses to pay by the stated deadline, Cryptolocker deletes the encryption key and permanently prevents users from accessing their data. “There isn’t a guarantee that once the payment is received you’ll actually get access to your files,” Brandt says. “So it’s not a good idea to pay them, as the payment will reward them and convince them to continue using similar tactics.”
6. Apple Insecurity
Anyone remember that infamous Mac vs PC ad that lampooned Windows PCs for all of their security ills? The weekend before RSA Conference 2014 revealed that Apple isn’t immune to security problems, as news that Apple’s OS X operating system had some severe (and heretofore unpatched) vulnerabilities broke just before the conference. Another vulnerability was revealed to me by Yair Amit, the CTO of new security startup Skycure. Amit explained that iOS devices could be vulnerable to malicious profiles – which Sycure initially discovered in 2013 — that Amit now says are available in new variant that is more difficult to detect. “[This new form of malicious profiles] is also completely invisible to the user and [mobile device management] (MDM) after the victim installs them.”
A Skycure video showing the iOS ‘invisible profiles’ vulnerability, which has since been patched in iOS 7.1. (Source: Yair Amit/Skycure)
Once this invisible profile has been created, Amit explained that a user on the same Wi-Fi network could gain access to the target device to change settings, mess with device configuration, and generally cause mischief. Yair explained that Apple fixed the “invisible profile” vulnerability in the recently-released iOS 7.1 update, but it’s a potent reminder that even the most supposedly secure desktop and mobile OSes likely have vulnerabilities that hackers are always trying to get access to.
7. Data Visualization Everywhere
Another trend this year at RSA was the proliferation of data and network analysis tools and services, particularly on the visualization front. “One of the [biggest trends I noticed] was that in almost every single row of the expo hall, there were at least two companies offering network visualization software,” said Josh Stone, Director of Product Management for TraceSecurity. “If you’re looking for something to turn your network traffic into a time-series graphs, you could find it there.”
8. Cloud and Mobile Security
As expected, security for cloud-based IT services and mobile device security continued as popular topics this year, and I’d expect that trend to continue. IT departments are increasingly being asked to manage and secure devices as part of their bring your own device (BYOD) security strategy, and the same goes for cloud-based solutions as well. On the BYOD front, Grayson Milbourne, the directory of security intelligence at Webroot, told me that just having basic BYOD security policies in place is a great first step. “Having a consistent policy that details what happens when an employee device is lost is important,” Milbourne says. “Steps such as wiping data from the device, making sure device data is routinely and securely backed up, enabling two-factor authentication, and educating employees about all of these things is important.”
RSA Conference 2014 Resources
If you couldn’t attend RSA Conference 2014 in person, many sessions and presentations are now online — and free to access — at the conference downloads page. You can also check out our other coverage of the show, including our list of security companies to watch, news about Microsoft’s EMET 5.0 security tool, and our RSA Conference 2014 T-shirt gallery. So what are you worries about most when it comes to keeping your IT environment secure? Drop me an email with your thoughts, or tell me what you think via my Twitter or Google+ pages, which are linked below.
- Follow Jeff James on Twitter (@jeffjames3) and Google+ (add Jeff to your circles)
- Follow the Petri IT Knowledgebase on Twitter (@petri_co_il)
- Follow us on Facebook and Google+ as well!