Last week, Microsoft started rolling out an update to block all Office VBA macros obtained from the internet by default to prevent phishing attacks. Now, the threat actors are using container files and other tactics to distribute malicious payloads.
A macro is an automated input sequence that enables users to automate frequently used tasks in Microsoft Office. It’s one of the popular ways used by hackers and scammers to steal sensitive data and distribute ransomware. The new default behavior aims to protect enterprise systems by preventing users from opening malicious files with a single click.
Here’s how threat actors are adapting to a post macro world
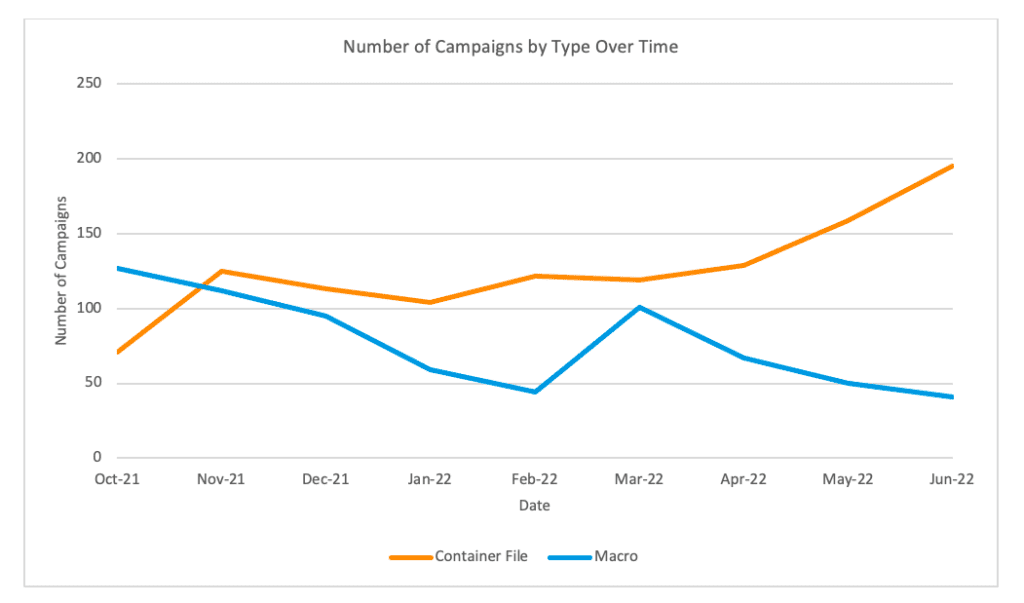
According to the security firm Proofpoint, researchers have found that the VBA macro-based attacks decreased by 66 percent between October 2021 and June 2022. However, the hackers are increasingly using other file formats (such as RAR, ISO, and ZIP) to send macro-enabled documents to a potential victim through emails. The number of malware campaigns abusing container files increased by around 175 percent over the same period.
“When downloaded, the ISO, RAR, etc. files will have the MOTW attribute because they were downloaded from the internet, but the document inside, such as a macro-enabled spreadsheet, will not. When the document is extracted, the user will still have to enable macros for the malicious code to automatically execute, but the file system will not identify the document as coming from the web,” the Proofpoint Threat Research Team explained.
Additionally, threat actors could use container files to deliver payloads with additional content like DLLs, LNKs, and executable (.exe) files. These harmful files make it easier for malware operators to remotely execute malicious code on a computer.
Proofpoint researchers noted that organizations will notice a dramatic increase in XLL file-based malware campaigns. The XLL file extension is an Excel Add-in that provides access to third-party tools and functions. However, ISO, RAR, and LNK files are still the most widely used attack vectors in enterprise environments.



