
Microsoft has discovered that a Chinese government hacking group dubbed Volt Typhoon is targeting critical infrastructure environments in the United States. The campaign is designed to steal network credentials and sensitive data to disrupt critical communications with the Asia Pacific region.
According to Microsoft, the Volt Typhoon group has been actively targeting companies in Guam and other parts of the United States for at least two years. The campaign affected various industries such as manufacturing, construction, communications, government, maritime, education, information technology, utility, and transportation.
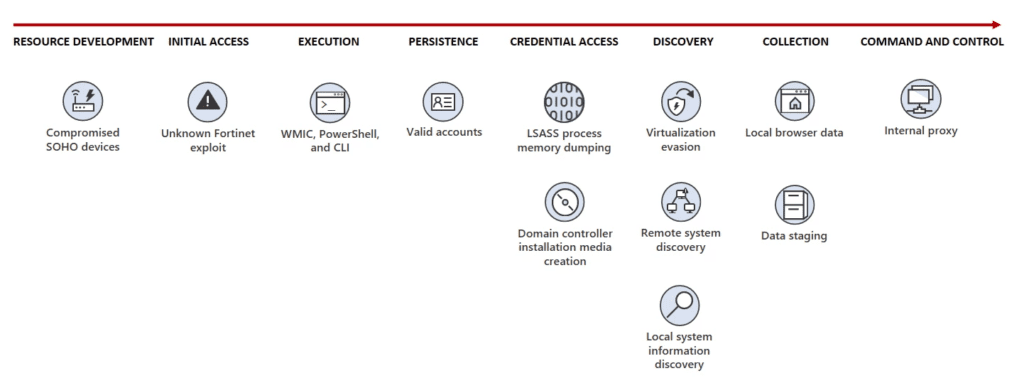
The Chinese hackers use the “living off the land” technique to manually control tools already installed on the victim’s computers. Additionally, the threat actors use home and small office network equipment (such as firewalls, routers, and VPN hardware) to hide their communications with infected devices.
“Volt Typhoon achieves initial access to targeted organizations through internet-facing Fortinet FortiGuard devices,” the Microsoft Threat Intelligence team explained. “The threat actor attempts to leverage any privileges afforded by the Fortinet device, extracts credentials to an Active Directory account used by the device, and then attempts to authenticate to other devices on the network with those credentials.”
How to protect organizations against Volt Typhoon attacks
Microsoft detailed indicators of compromise that could help IT admins identify whether their enterprise network is infected by Volt Typhoon attacks. The company urges customers to close or change the credentials of all compromised user accounts. It’s also recommended to monitor the activity of these accounts to prevent further damage.
Microsoft noted that organizations should enforce strong multi-factor authentication (MFA) policies to mitigate security risks. Moreover, IT admins can configure attack surface reduction rules to prevent credential spoofing, process creation, and execution of malicious scripts. Microsoft Defender for Endpoint customers can run endpoint detection and response (EDR) capabilities in block mode to defend against security threats.



