Microsoft Entra ID Gets Conditional Access Overview Dashboard and Templates

Key takeaways:
- Microsoft’s new Conditional Access overview dashboard lets IT Pros get a comprehensive view of their Conditional Access posture.
- It helps administrators track unprotected sign-ins, non-compliant/unmanaged devices, and malicious sign-in alerts.
- The Conditional Access templates make it easier for IT admins to deploy policies aligned with Microsoft recommendations.
In today’s constantly evolving digital landscape, finding the perfect harmony between strong security measures and seamless access for a hybrid workforce can prove to be quite a daunting task. To simplify this challenge, Microsoft has introduced a new Conditional Access overview dashboard, designed to assist Entra ID customers in effortlessly navigating this intricate terrain.
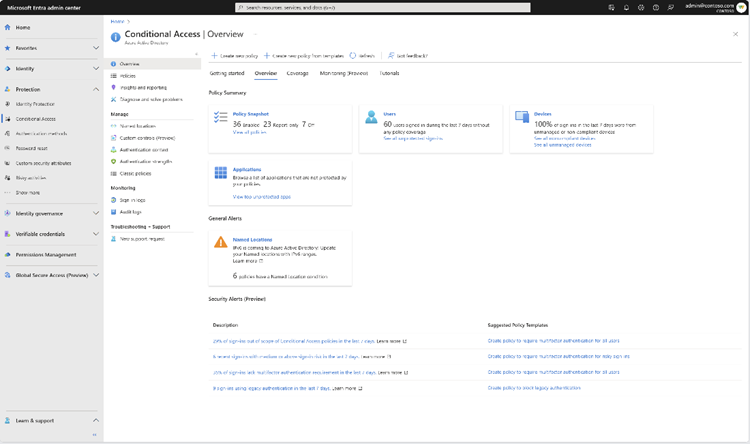
The Conditional Access overview is a built-in dashboard that allows organizations to gain detailed insights about their Conditional Access posture. It’s the default landing page that lets administrators create new policies with Conditional Access templates. The Conditional Access overview dashboard helps to track unprotected sign-ins, non-compliant/unmanaged devices, and malicious sign-in alerts.
“As an administrator, it provides a concise summary of your policies, identifies any gaps in your policy coverage, and provides valuable insights based on sign-in activity within your tenant. This feature enables you to swiftly pinpoint areas where you can enhance the enforcement of Zero Trust principles, ultimately bolstering your defense mechanisms,” Microsoft explained.
Conditional Access templates are designed to make it easier for IT admins to deploy new policies aligned with Microsoft recommendations. The templates help to ensure that the policies provide maximum protection for corporate assets as well as promote optimal and secure access for hybrid teams.
Microsoft says that customers can select from 16 predefined Conditional Access templates that are organized into different categories. These include zero trust, secure foundation, emerging threats, protect administrators, and remote work.
Getting started with Conditional Access templates
To get started with templates, head over to the Microsoft Entra admin center and select Protection > Conditional Access, and use the templates to create new policies. Then, click the “Show more” option to view all policy templates in each category.
Microsoft introduced a new continuous access evaluation (CAE) setting in public preview for Entra ID Conditional Access. It enables IT admins to strictly enforce location policies for network access in their organizations. The feature lets CAE-enabled applications (such as Microsoft Teams, Exchange Online, SharePoint, and Microsoft Graph) to quickly invalidate tokens that violate IP-based location policies.


