Microsoft Defender for Identity Adds New Sensor to Detect Certificate Abuse

Key Takeaways:
- Microsoft Defender for Identity has introduced a new AD CS sensor to enhance the detection of suspicious certificates.
- Microsoft says IT admins can access alerts and recommendations through the Secure Score dashboard.
- The new sensor is designed to identify instances where threat actors attempt to relay NTLM authentication to AD CS servers.
Microsoft Defender for Identity has added a cutting-edge addition to its toolkit – a new sensor now deployable on Active Directory Certificate Services (AD CS) servers. The sensor augments the existing capabilities, significantly enhancing the detection mechanisms for identifying questionable certificates within enterprise environments.
Active Directory Certificate Services (AD CS) is a Windows Server role that allows organizations to issue digital certificates. These certificates are used to authenticate users and devices as well as ensure the integrity of data in Entra ID (formerly Azure Active Directory) environments. This capability should be particularly useful for various tasks, including securing websites with HTTPS and encrypting email communications.
Microsoft explained that the new sensor enables IT admins to view alerts and recommendations through the Secure Score dashboard. Moreover, it helps to detect when threat actors relay NTLM authentication to AD CS for impersonation purposes.
Additionally, Microsoft Defender for Identity now makes it easier to track audit configuration changes. It helps to prevent attempts from hackers to disable the logs to perform malicious actions. The AD CS sensor also detects and triggers alerts about the suspicious deletion of certificate requests.
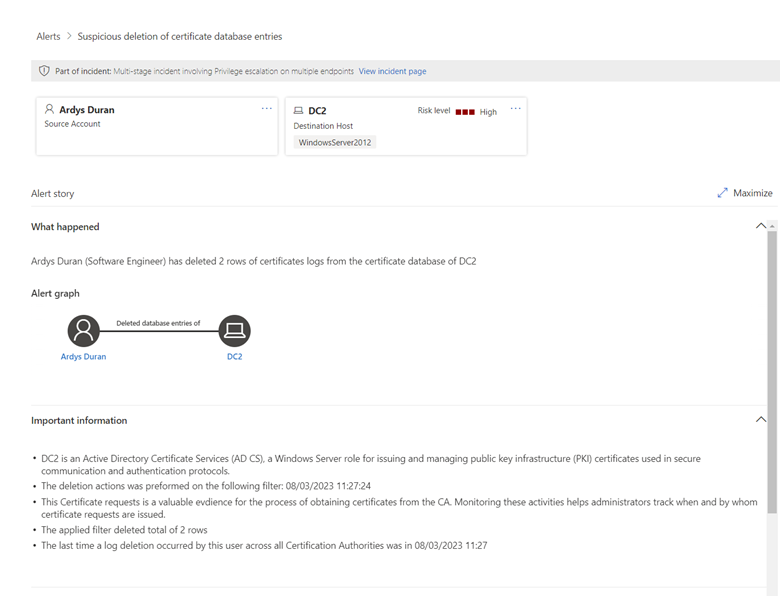
Microsoft Defender for Identity to detect suspicious ADCS modifications
Microsoft plans to add a new feature that will let IT Pros detect suspicious modifications to the AD CS settings. “This event suggests that a change was made to the access control list (ACL) of the certification authority itself. This allows attackers to perform certificate authority level operations that potentially can lead to domain takeover,” Microsoft noted.
Microsoft has also detailed several security recommendations coming to the Secure Score dashboard. These include the ability to edit misconfigured enrollment agent certificate templates and certificate templates ACL/owner. Microsoft will also let IT admins edit overly permissive certificate templates with privileged EKU. We invite you to check out this support page to learn more about the new AD CS sensor.


