Microsoft Defender for Endpoint Gets New Feature to Block Compromised Unmanaged Devices

Microsoft Defender for Endpoint has released a new Contain feature that lets organizations isolate compromised unmanaged Windows devices from the network. The new capability will help IT admins to prevent attackers from carrying out malicious activities like lateral movement or data exfiltration.
Once a device is contained, Microsoft Defender for Endpoint will block its communications with all other Windows PCs. “This action can help prevent neighboring devices from becoming compromised while the security operations analyst locates, identifies, and remediates the threat on the compromised device,” Microsoft noted.
Microsoft indicated that the Contain feature is similar to the existing device isolation option available in Microsoft Defender for Endpoint. However, it works with unmanaged devices that haven’t been onboarded yet.
How to use the Contain feature to block a compromised unmanaged device
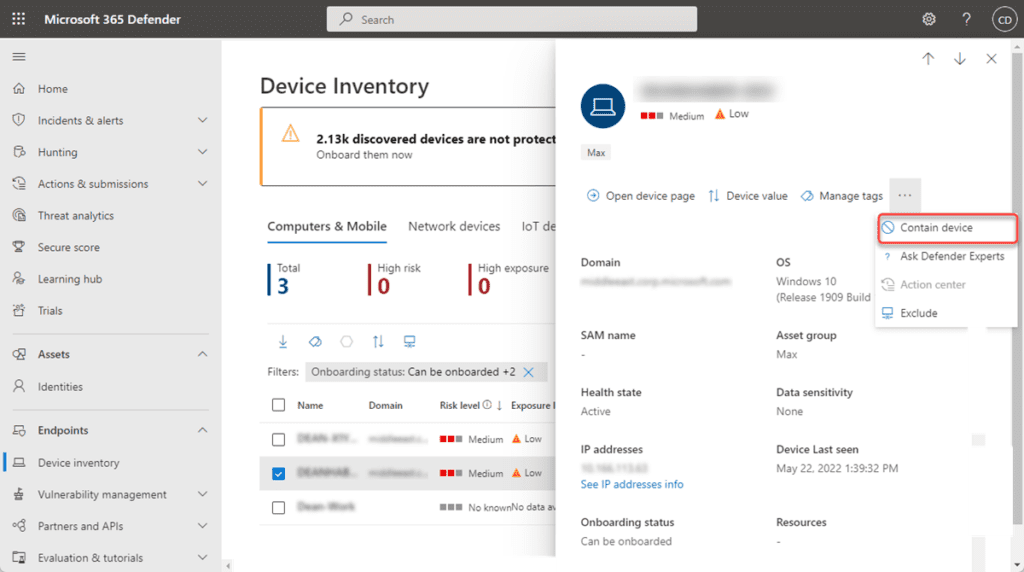
- Sign in to the Microsoft 365 Defender portal, head to the Device inventory page, and then choose the device to contain.
- Click the Actions menu available in the device flyout and select the Contain device option from the list.
- The contain device popup will appear on the screen, type the details in the comment box, and hit the Confirm button.
Once clicked, all devices enrolled in the Microsoft Defender for Endpoint can take up to 5 minutes to stop communications to and from the contained device. The blocking will continue even if the compromised device tries to change its IP address.
Meanwhile, IT admins will be able to unblock the specific device by selecting it from the Device inventory or heading to the device page. Finally, open the action menu and select the “Release from containment” option to restore the device’s communication with the network.
Microsoft notes that the new Contain feature in Microsoft Defender for Endpoint is currently only available for PCs running Windows 10 (or newer) or Windows Server 2019 (or newer) OS. The company has promised to bring support for additional platforms in future versions.


