How to Set Up Windows Server Rebootless (Hotpatching) Patching
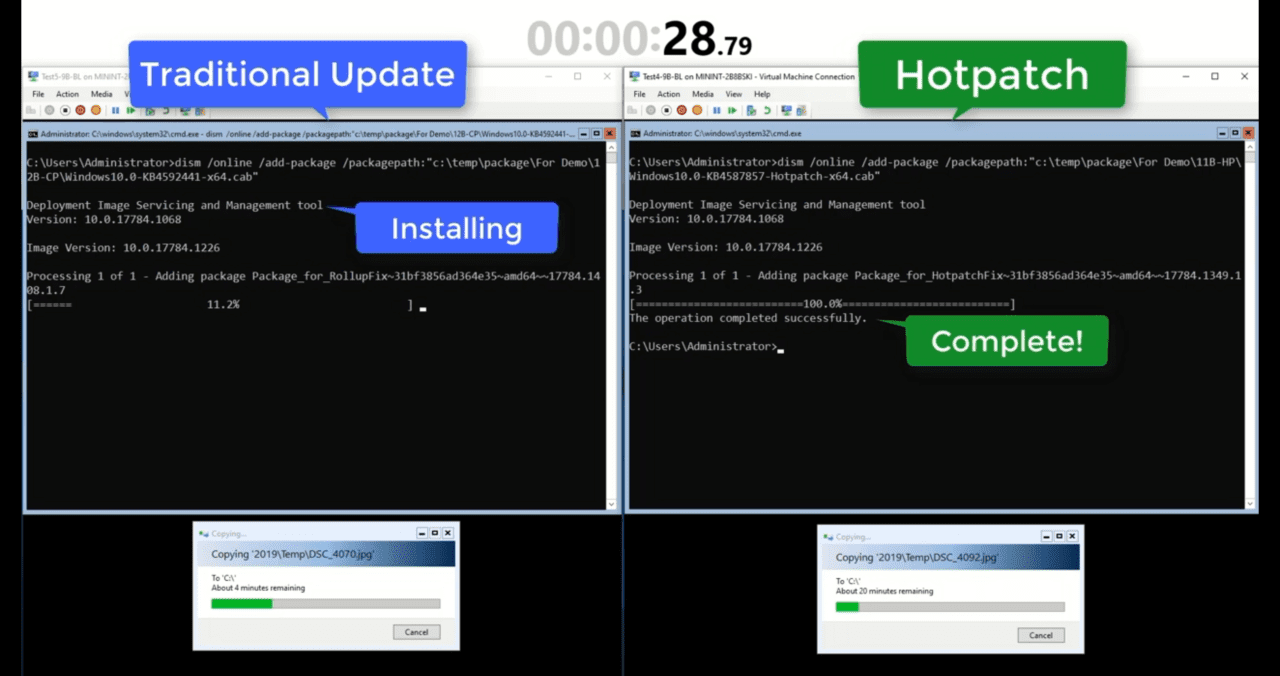
As part of the Automatic VM Guest Patching for Azure VMs preview announced at Ignite in March, Microsoft introduced Windows Server hotpatching. Hotpatching lets organizations apply security patches to Windows Server without rebooting. A feature that’s been part of other server platforms for years, hotpatching finally comes to Windows Server. But there are some caveats.
The first is that for the time being at least, hotpatching only works in Windows Server Azure Edition virtual machines (VMs). That means your server workloads must be running in the Azure cloud. Microsoft says that hotpatching brings the following benefits:
- Lower workload impact with less reboots
- Faster deployment of updates as the packages are smaller, install faster, and have easier patch orchestration with Azure Update Manager
- Better protection, as the Hotpatch update packages are scoped to Windows security updates that install faster without rebooting
I expect that Microsoft will use hotpatching as bait to lure more organizations to move Windows Server workloads to the cloud. But time will tell.
Baseline Windows Update Latest Cumulative Update
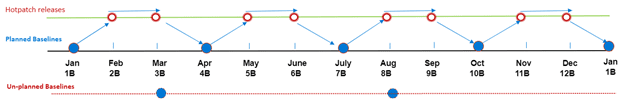
The second caveat is that you will still need to reboot Windows Server – at least sometimes. Before you can apply hotpatches to Windows Server, it must be running the latest baseline Windows Update Latest Cumulative Update (CU). Microsoft says that planned baseline updates will be released every three months. That means, at least once in three months, you will need to reboot Windows Server. Hotpatches will be released monthly on Patch Tuesday.
Unplanned baseline updates might be released when zero-day flaws need to be patched but can’t be fixed without a reboot. The image above shows how planned, unplanned, and hotpatch releases might pan out over a year.
Integration with Automatic VM Guest Patching
Now in preview in all regions, Automatic VM Guest Patching helps administrators with update management by safely patching VMs. Microsoft says Automatic VM Guest Patching brings the following benefits:
- Patches classified as Critical or Security are automatically downloaded and applied on the VM
- Patches are applied during off-peak hours in the VM’s time zone
- Patch orchestration is managed by Azure and patches are applied following availability-first principles
- Virtual machine health, as determined through platform health signals, is monitored to detect patching failures
- Works for all VM sizes
Remember that at the time of writing, Automatic VM Guest Patching is in preview and you shouldn’t enable it on Azure subscriptions that host production workloads. For more detailed information on Automatic VM Guest Patching, check out Microsoft’s website here.
Enroll your Azure subscription in the Automatic VM Guest Patching preview and enable hotpatching
The first step to enabling hotpaching for Windows Server in Azure is to opt in to the Automatic VM Guest Patching public preview. The easiest way to do that is in the Azure portal using Cloud Shell. If you’ve never used Cloud Shell before, check out Managing Azure Resources with Cloud Shell on Petri.
- Sign in to the Azure management portal.
- Click the cloud shell icon in the top right of the portal window.
- In shell at the bottom of the portal window, click the dropdown in the top left and switch from Bash to PowerShell.
- Run the following commands in the PowerShell window:
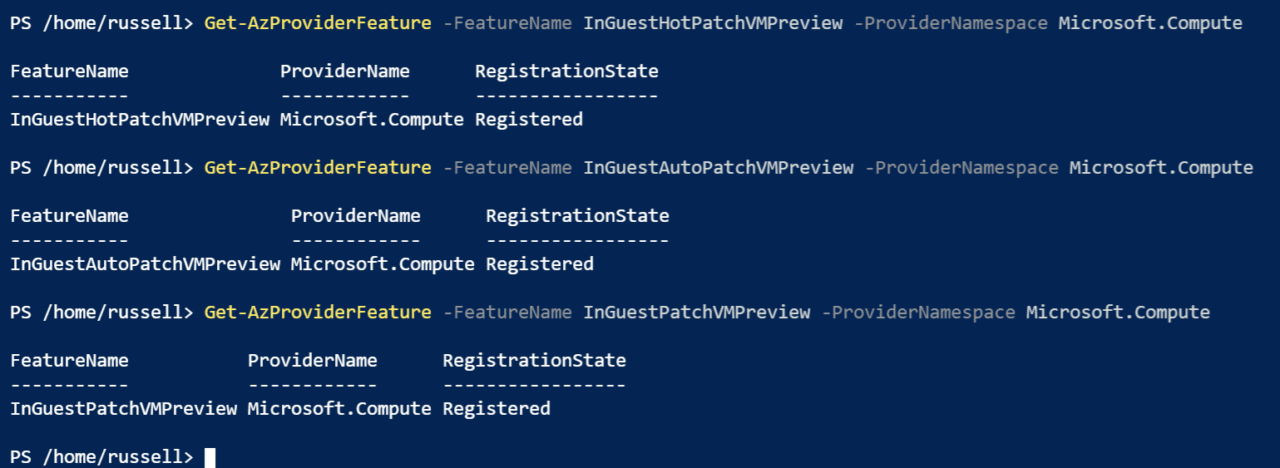
Register-AzProviderFeature -FeatureName InGuestHotPatchVMPreview -ProviderNamespace Microsoft.Compute Register-AzProviderFeature -FeatureName InGuestAutoPatchVMPreview -ProviderNamespace Microsoft.Compute Register-AzProviderFeature -FeatureName InGuestPatchVMPreview -ProviderNamespace Microsoft.Compute
It can take up to 15 minutes for service to be registered. You can check the status of each service using the following three commands:
Get-AzProviderFeature -FeatureName InGuestHotPatchVMPreview -ProviderNamespace Microsoft.Compute Get-AzProviderFeature -FeatureName InGuestAutoPatchVMPreview -ProviderNamespace Microsoft.Compute Get-AzProviderFeature -FeatureName InGuestPatchVMPreview -ProviderNamespace Microsoft.Compute
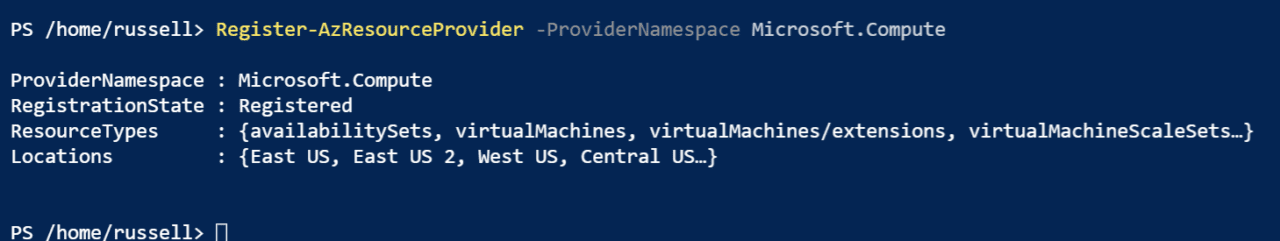
Once you are sure that each service status has changed to ‘Registered’, run the command below to propagate the change to the Compute resource provider:
Register-AzResourceProvider -ProviderNamespace Microsoft.Compute
Deploy a new Windows Server VM with hotpatching enabled
Hotpatching can’t be enabled on VMs that already exist. You will need to deploy a new VM to use hotpatching in Windows Server. And during the preview, you must use a special link to access to Azure management portal when you deploy a VM for hotpatching.
- Deploy a new VM in Azure using the following link.
- The link will take you straight to the Windows Server 2019 Datacenter: Azure Edition deployment page. You can either click Create to choose your own VM settings or Start with a pre-set configuration.
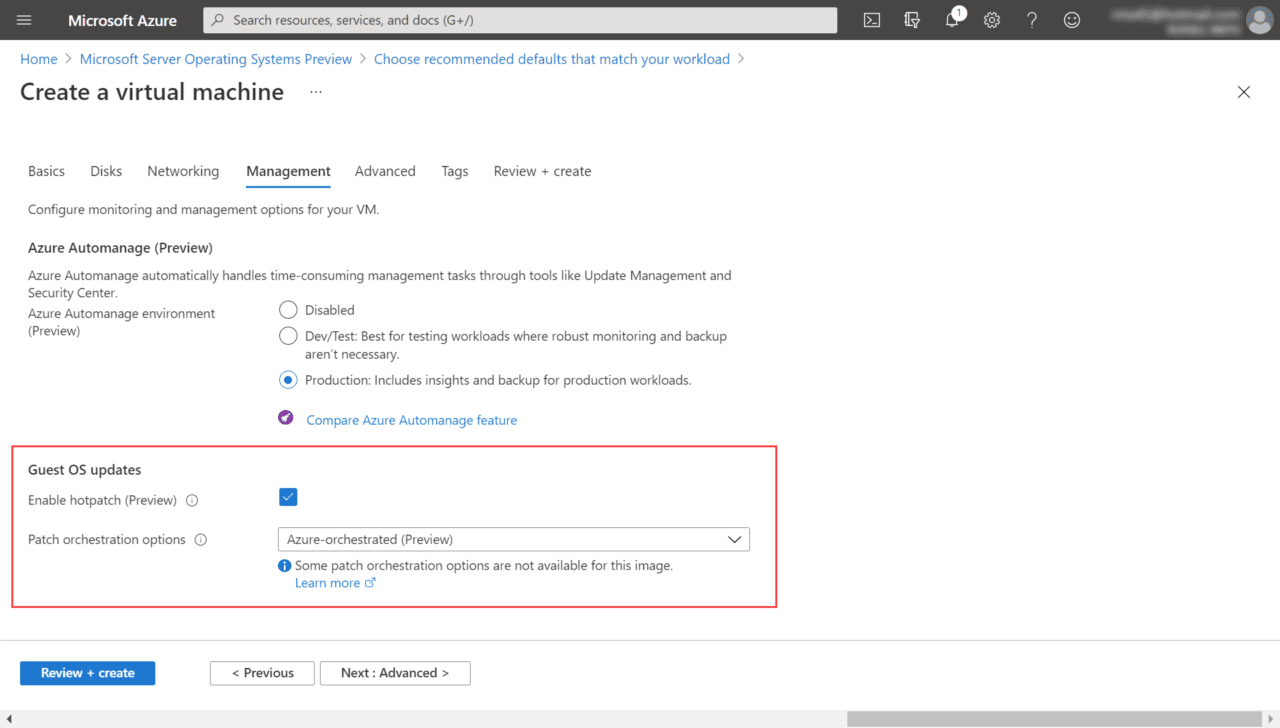
- Regardless of which option you choose, on the Management tab, make sure that under Guest OS updates, Enable hotpatch (Preview) is checked and Patch orchestration options is set to Azure-orchestrated (Preview).
- Complete the VM deployment.
For more information about how to deploy virtual machines in Azure, read Create a Virtual Machine in the Azure Cloud on Petri.
Checking VM update status
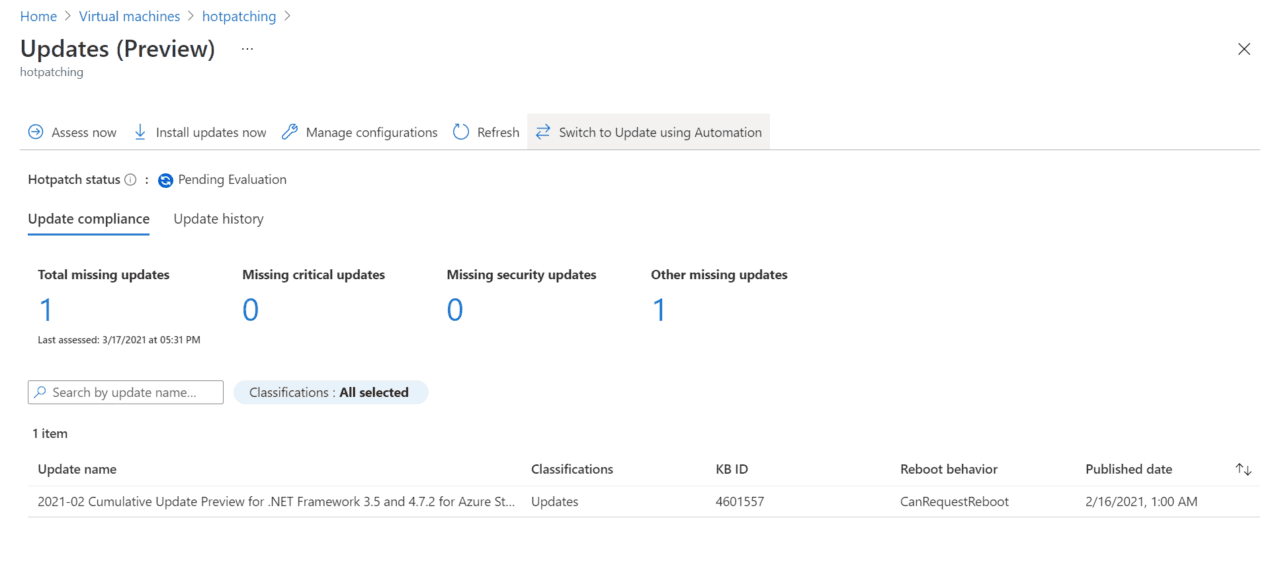
And that is it! Your new VM is now enrolled in Automatic VM Guest Patching. The VM will be assessed every few days and many times every month to make sure that it is up-to-date with the latest security patches. To check the patch status for your VM, use the Guest + host updates section for the VM in the Azure portal.
Hotpatching for Windows Server soon to be a reality
Hotpatching has been long coming to Windows Server. And even now, it’s quite limited in scope. But that seems to be a conscious decision on Microsoft’s part. Microsoft might make hotpatching available for on-premises Windows Server in the future, but I wouldn’t be surprised to see it limited to the Azure cloud.