How to Improve Remote Worker Security Using Microsoft Intune
The worldwide health crisis had led many organizations to expand remote access to enable more employees to work from home. Remote access solutions are sometimes rushed out with limited opportunity to plan how to secure them properly.
In an ideal world, you’d make sure that clients are compliant with a set of minimum standards before connecting remotely to the corporate network. And ensure that clients are secure even when not directly connected to the intranet.
Windows 10 Always On VPN (virtual private network) can integrate with Azure Active Directory (AD) to check Windows for health compliance when a connection attempt is made. Azure AD-issued short-lived certificates are used to authenticate the VPN if the device meets compliance rules. When a certificate expires, the client checks Azure AD again for compliance before Azure issues a new certificate.
For more information on Windows 10 Always On VPN, check out Understanding Windows 10 Always On VPN on Petri.
Another approach, which can also be used with VPNs, is to check for compliance whenever devices are connected to the public Internet. To check Windows 10 compliance, you’ll need a Mobile Device Management (MDM) solution.
Microsoft Intune
Intune is Microsoft’s MDM solution. Organizations can purchase Intune licenses to manage users and devices. Intune licenses are also included with some Microsoft 365 plans, like Microsoft 365 Business Premium.
There are several ways that Windows 10 devices can be enrolled with Intune. If a Windows 10 device is joined to an Azure Active Directory, it can optionally be automatically enrolled with Intune.
For more information on how to enroll devices and assign Intune licenses, see Microsoft Intune: Windows 10 Device Enrollment on Petri.
Create an Intune compliance policy
Once your devices are enrolled with Intune, create a compliance policy to make sure devices meet certain security standards. To create a policy, log in to the Microsoft Endpoint Manager (MEM) admin center and following the instructions below.
The policy settings in the instructions below are given as an example. You can of course choose your own settings according to your organization’s security policy.
- Log in to the MEM admin center with an administrator account, or another account that has permission to create and assign policies, here.
- In this list of options on the left below FAVORITES, click Devices.
- In the Overview pane below Policy, click Compliance policies.
- Click + Create Policy.
- In the Create a policy pane, select Windows 10 and later from the Platform dropdown menu.
- Click Create.
- On the Windows 10 compliance policy screen, enter a name for the policy and then click Next.
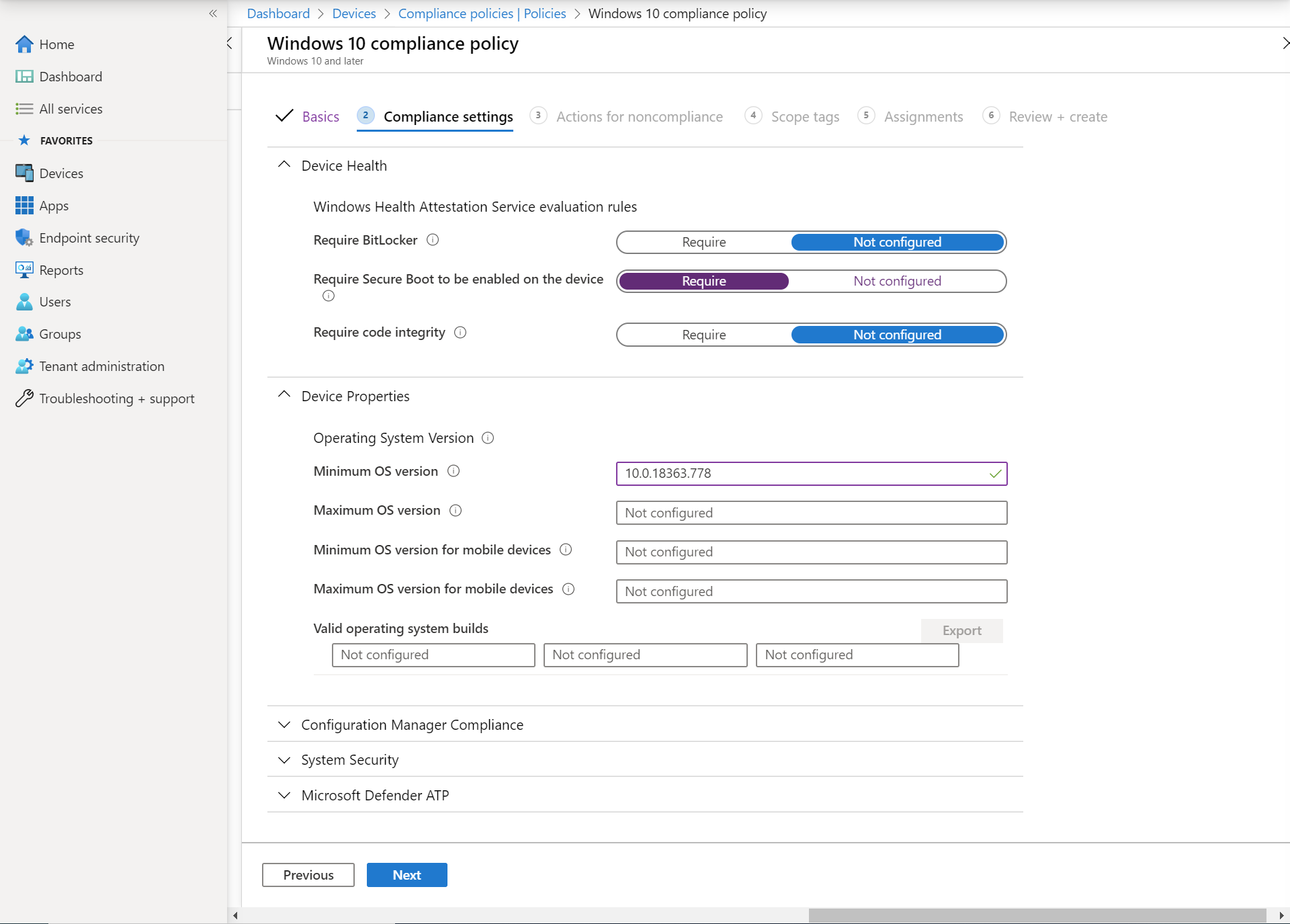
- On the Compliance settings tab, expand Device Health and select Require Secure Boot to be enabled on the device. Most devices manufactured in the past few years support Secure Boot.
- Expand Device Properties. In the Minimum OS version field, type 0.18363.778 as shown in the screenshot below. 10.0.18363.778 is Windows 10 version 1909 build 18363.778.
To get the Windows 10 version in the major.minor.build.revision format required by Intune, open a command prompt, type ver, and press ENTER.
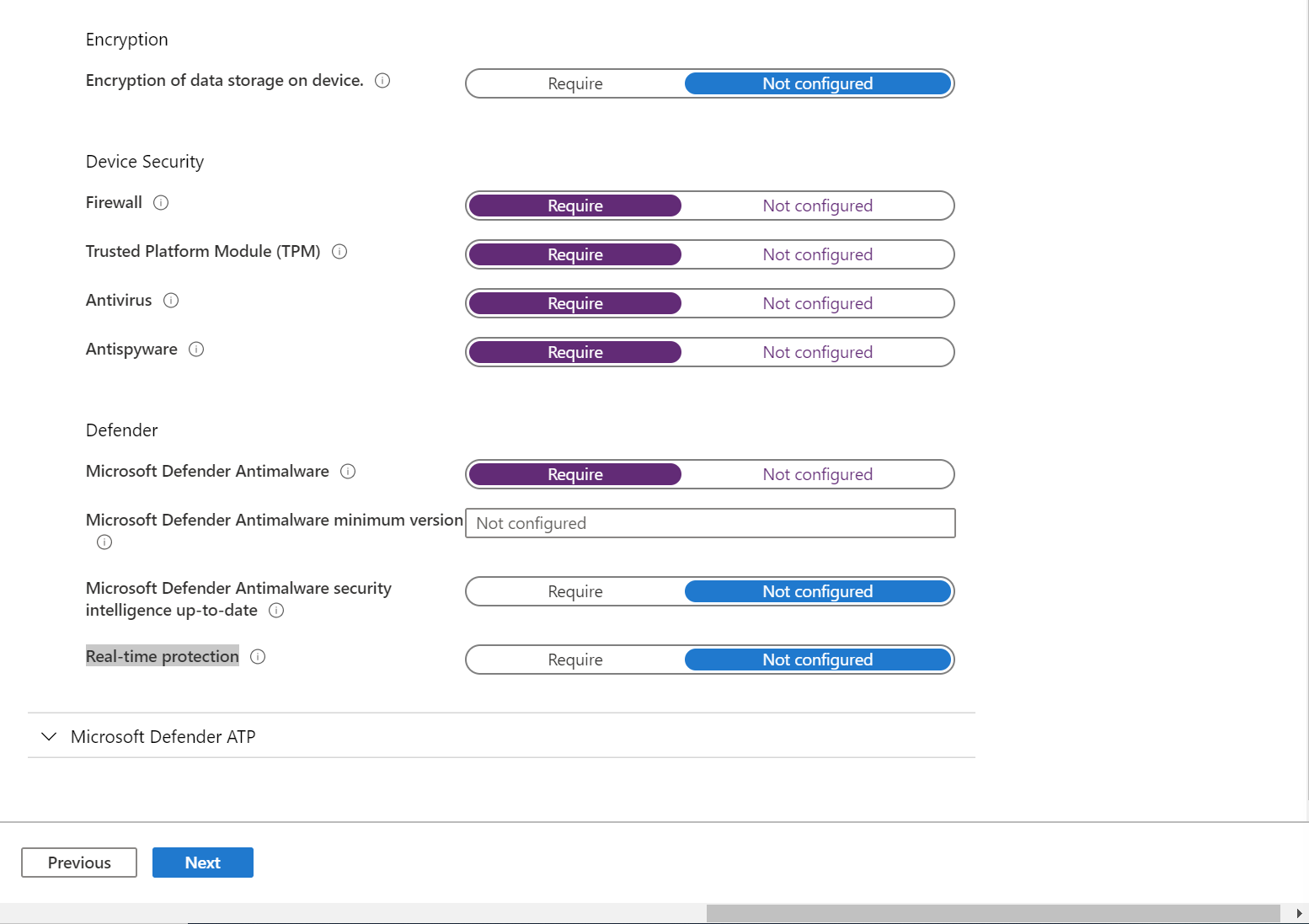
- Now expand System Security.
- Below Device Security, set Firewall, Antivirus, Trusted Platform Module (TPM), and Antispyware to Require.
- Below Defender, set Microsoft Defender Antimalware to Require.
- Now set Microsoft Defender Antimalware security intelligence up-to-date and Real-time protection to Require.
- Click Next to continue.
- On the Actions for noncompliance tab, select Retire the non-compliant device using the first dropdown menu under Mark device non-compliant. In the field to the right below Immediately, type 30. The minimum number for this field and action is 30 days.
The Remotely lock the noncompliant device isn’t supported for Windows 10 desktop devices. There’s an action to send an email to the user, and additional recipients. The Retire the noncompliant device action, removes all company data and the device is removed from Intune management.
- Click Next to continue.
- Click Next on the Scope tags
- On the Assignments tab, select All users from the dropdown menu to the right of Assign to under Included groups. This will apply the compliance policy to all users logging on to devices registered with Intune.
- Click Next.
- Review the policy details on the final tab and then click Create.
How to check Intune policy compliance status
Once the policy is created, any Windows 10 devices that fall out of compliance will be flagged as Not compliant. To check the status of devices:
- In Microsoft Endpoint Manager, click Dashboard in the list of options on the left.
- Make sure that Devices is selected on the dashboard.
- In the tabs across the top of the Devices screen, click Compliance status.
- Below Device compliance status, you can view the number of compliant and non-compliant devices.
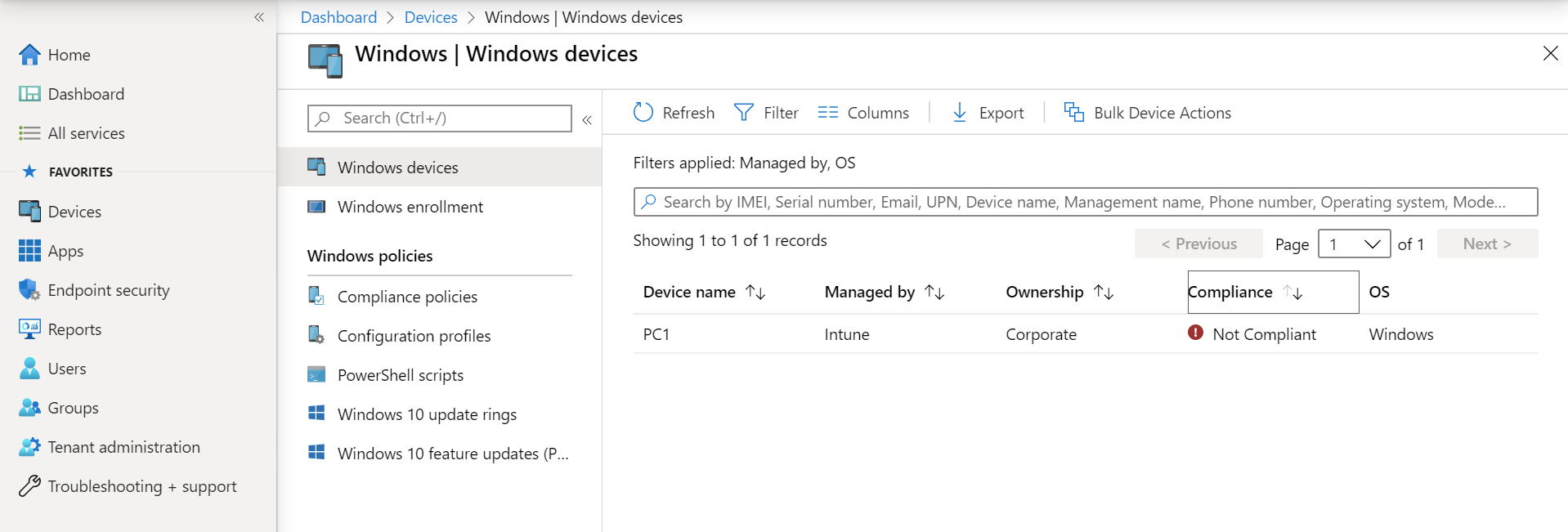
- To view exactly which Windows 10 devices are not compliant, below By platform click Windows.
- Now you will see a list of Windows devices enrolled with Intune. Click the Compliance column header to order the list by device compliance status.
Remember that when creating new policies, they are not applied immediately to devices. Each device must sync with Intune before new policies are applied.