Free Active Directory Tool for Preventing Insider Misuse
Sponsored IT content provided by SolarWinds
The 2015 Verizon Data Breach Investigations Report states that 20.6 percent of data breaches are due to insider misuse incidents. Additionally, the report found that 55 percent of insider misuse is caused from abuse of privileges and permissions, which the report calls a ‘defining characteristic of the internal actor breach.’ This trend is prominent across industries and the ‘internal actors’ who breach this code also come from various departments according to the report.
Organizations are now realizing the need to safeguard confidential company data so that it does not fall into the wrong hands. Before you start thinking about applying the highest security measures in your organization, one of the easiest ways to prevent insider misuse is making sure appropriate user and group access rights are prescribed for a specific file folder or shared drive.
Applying the proper user and group access rights is a critical step for preventing insider misuse because it enables IT pros and the organization to see who has access to different information. This approach also tells you why certain users have permissions to some folders or files, and really allows you to take a step back to re-assess and prevent insider threats. One of the ways you can easily do this is by automating it with a free tool, such as SolarWinds’ Permissions Analyzer for Active Directory.
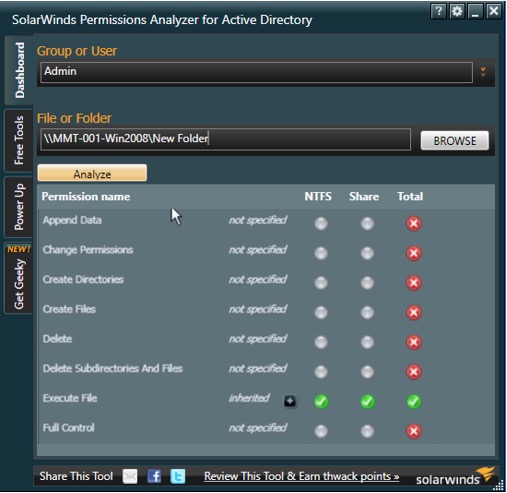
This free tool gives you complete visibility into effective permissions and access rights. Not only are you taking a step in the right direction by preventing insider misuse, but you are also eliminating much of the manual activity that’s typically required. With this tool, you are also able to readily present to the IT organization on which user has what access rights. The permissions analyzer for Active Directory tool helps enables you to:
- get a complete hierarchical view of the effective permissions and access rights for a specific file folder (NTFS) or share drive
- easily see what permissions a user has for an object and why (group membership or direct permissions)
- browse permissions by group or individual user
- analyze user permissions based on group membership combined with specific permissions
Do all this in minutes using a simple desktop tool.
Optimizing Active Directory goes beyond simply limiting users from accessing files and folders. There are other challenges that an IT pro faces in an Active Directory environment, such as domain controller issues, replication failure, user account lockouts, and identifying user activity issues. You can overcome these challenges by continuously monitoring the performance and availability of Active Directory servers, and being able to automatically respond to malicious user activity and stop threats before security is compromised. Start gaining visibility to troubleshoot LDAP client sessions, context switches, DNS server service, file replication, directory services, service outages, and many more.




