
Last week, the application service provider F5 disclosed a new security vulnerability that allows threat actors with network access to execute commands on its BIG-IP networking devices. The critical security flaw, tracked as CVE-2022-1388, carries a CVSS score of 9.8 out of 10.
According to the security advisory, the vulnerability exists in the representational state transfer (REST) interface for the iControl framework. The authentication component is used for communication between customers and F5 BIG-IP systems. This flaw could allow remote attackers to bypass authentication and run arbitrary commands on the targeted devices.
“This vulnerability may allow an unauthenticated attacker with network access to the BIG-IP system through the management port and/or self IP addresses to execute arbitrary system commands, create or delete files, or disable services. There is no data plane exposure; this is a control plane issue only,” F5 explained.
F5 has confirmed that the security flaw impacts various BIG-IP product versions. The list includes 1.0 to 16.1.2, 1.0 to 15.1.5, 1.0 to 14.1.4, 1.0 to 13.1.4, 1.0 to 12.1.6, and 6.1 to 11.6.5. Since F5 BIG-IP devices are typically used in enterprise environments, this RCE vulnerability could be abused to create/delete files or disable servers.
Fortunately, F5 has already released new security updates to address the vulnerability in versions v17.0.0, v16.1.2.2, v15.1.5.1, v14.1.4.6, and v13.1.5. However, the company is advising customers running older versions (11.x and 12.x) to upgrade to a newer firmware version immediately.
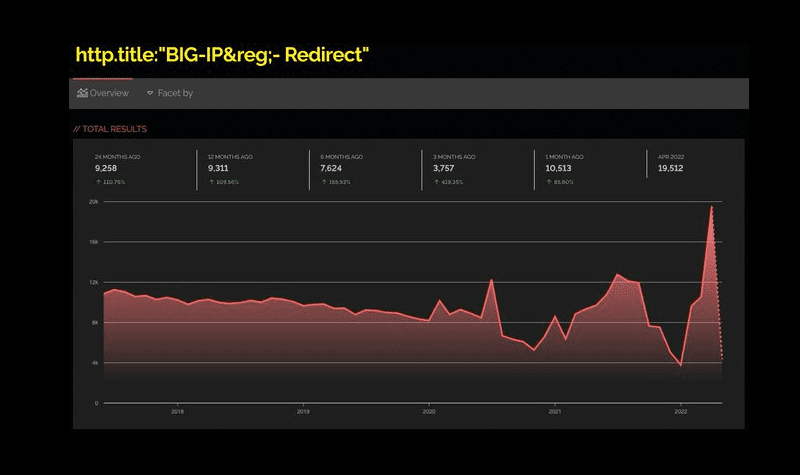
In a recent tweet, cybersecurity researcher Nate Warfield revealed that around 16,000 BIG-IP devices are currently exposed to the internet worldwide. It is important to note that the majority of these devices can be found in the United States, Australia, India, and China.
Attackers are reportedly exploiting the critical F5 BIG-IP RCE flaw
Accordion to security researcher Kevin Beaumont, the CVE-2022-1388 flaw is currently being exploited in the wild. Meanwhile, researchers have also developed a proof-of-concept (PoC) code for this security vulnerability.
F5 has provided some temporary workarounds to help customers who can’t apply the latest security patches on their BIG-IP devices immediately. The company recommends that IT Admins should “block iControl REST access through the self IP address, restrict iControl REST access through the management interface and modify the BIG-IP httpd configuration.”



