Welcome back to our two-part series on how to enable secure LDAP (LDAPS) communications between client/server applications on Windows Server 2008/2012 domain controllers. In part one, I went over what you should know about LDAPS, your options, and prerequisites. After we understood the concepts of why, where and when we should be looking to use LDAPS, let’s move on to the actual configuration.
Enabling Secure LDAP: Configuring LDAPS
1. Create the right certificate template to issue
First, we need to make sure that your CA is allowed to issue the correct types of certificates. Remember, these must contain the Server Authentication OID 1.3.6.1.5.5.7.3.1.
I’ve described the steps you need to take in order to create such a template in my Creating a Digital Certificate Template for the purpose of Server Authentication in Windows Server 2008/R2/2012 article.
2. Request a certificate for server authentication
To request a certificate from your LDAPS server, do the following on each DC that requires LDAPS connections:
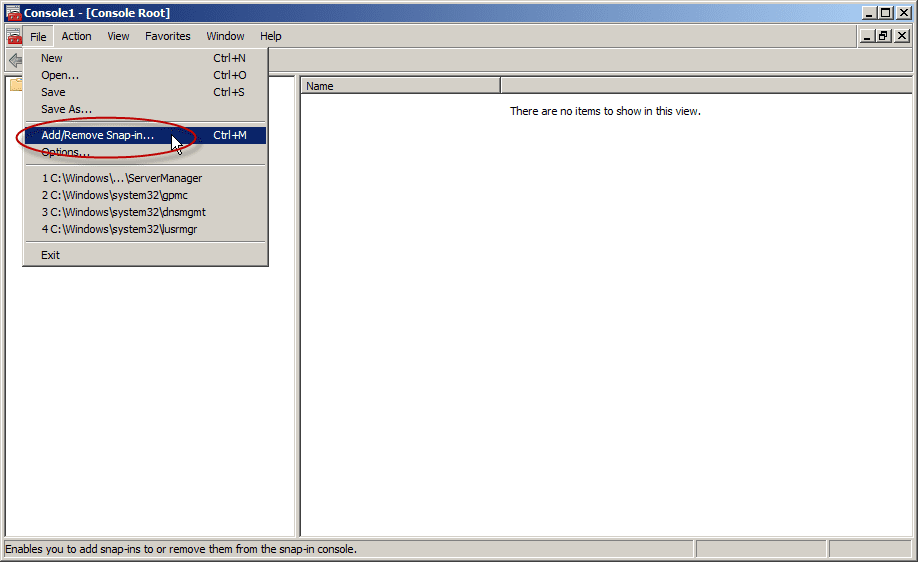
- In Start, type MMC, and then press Enter. If User Account Control prompts it, go ahead and ensure it displays the action you want. After that, select Yes.
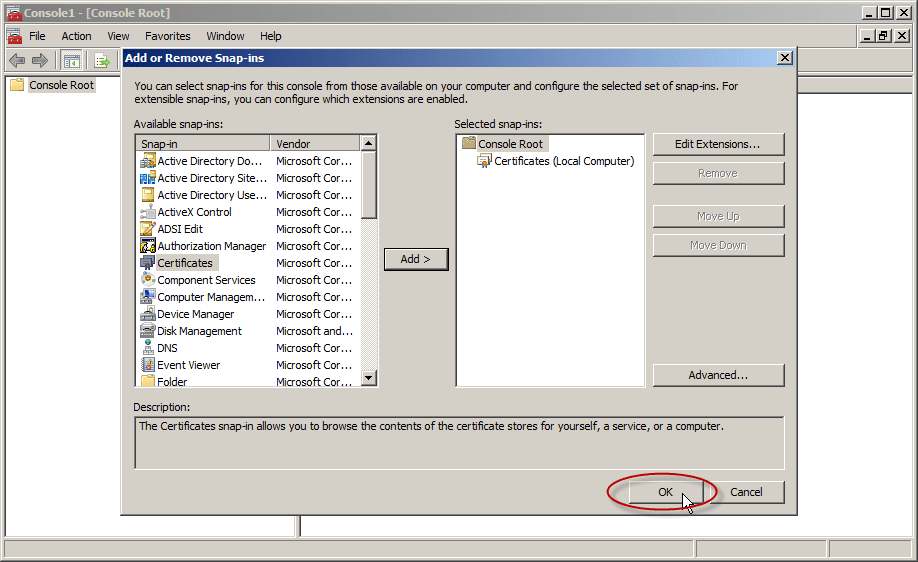
- In the MMC console that opens, click File and then click Add/Remove Snap-in.
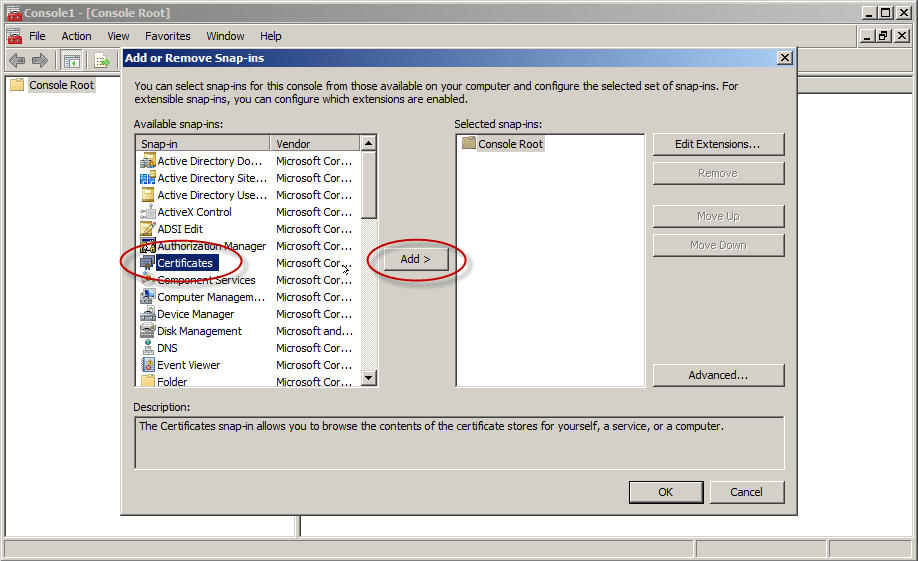
- Under Available Snap-ins, in Add or Remove Snap-ins, go ahead and select Certificates, and then click Add.
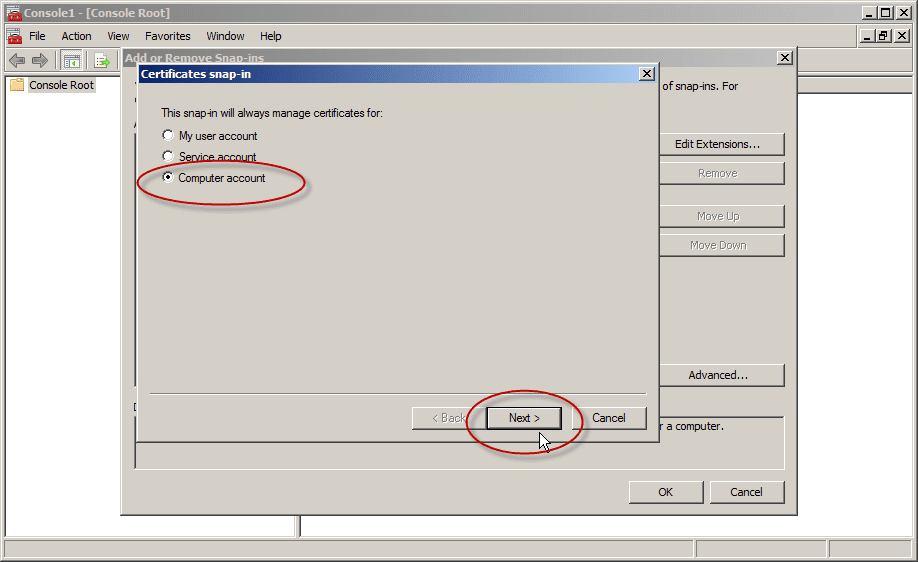
- In the Certificates snap-in, select Computer account and then click Next.
Note: If you plan to have more than one digital certificate for that DC, and if you are using Windows Server 2008/R2/2012, please read this following article BEFORE you proceed: The issue with Active Directory Domain Services (NTDS\Personal) certificate store
If you only plan to have one digital certificate on that DC, please proceed to the next step.
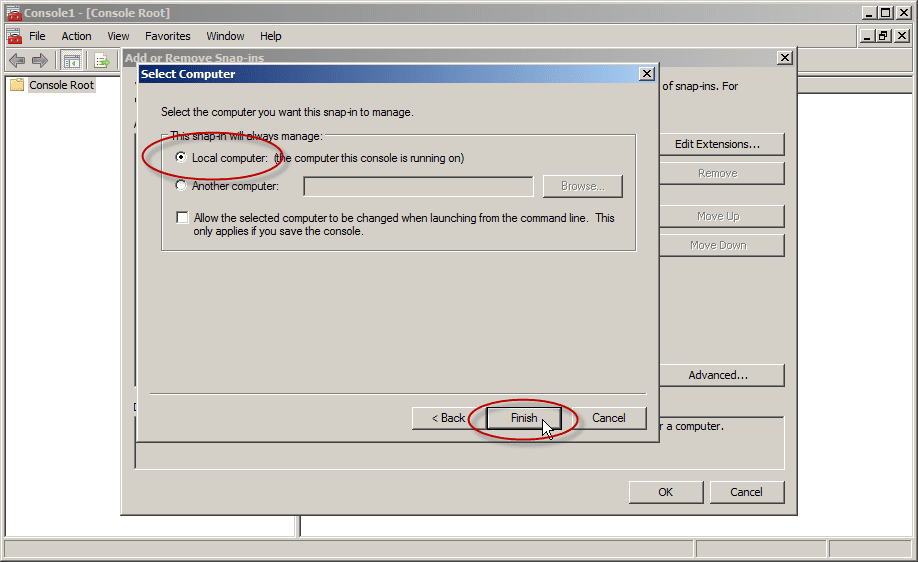
- In Select Computer, select Local. Once you have the correct computer selected, click OK and then click Finish.
- In Add or Remove Snap-ins, select OK.
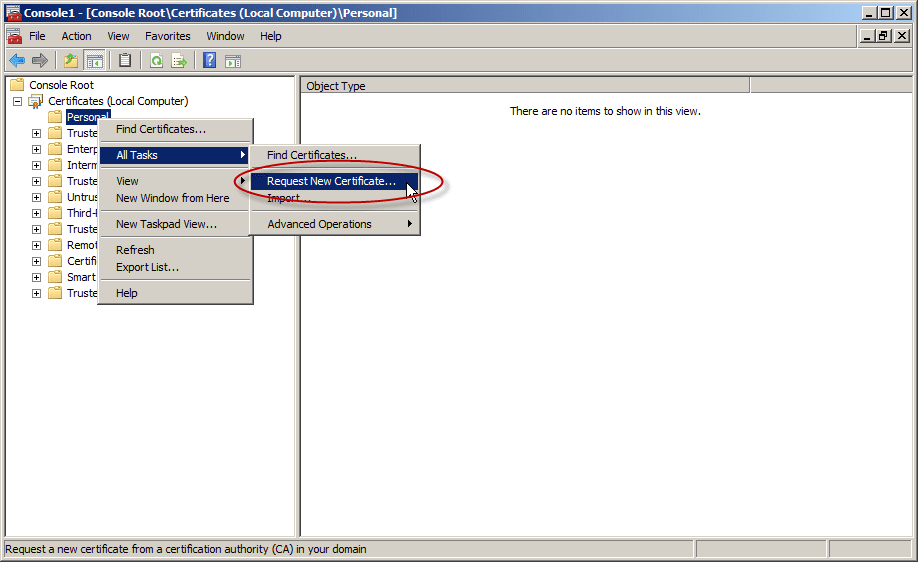
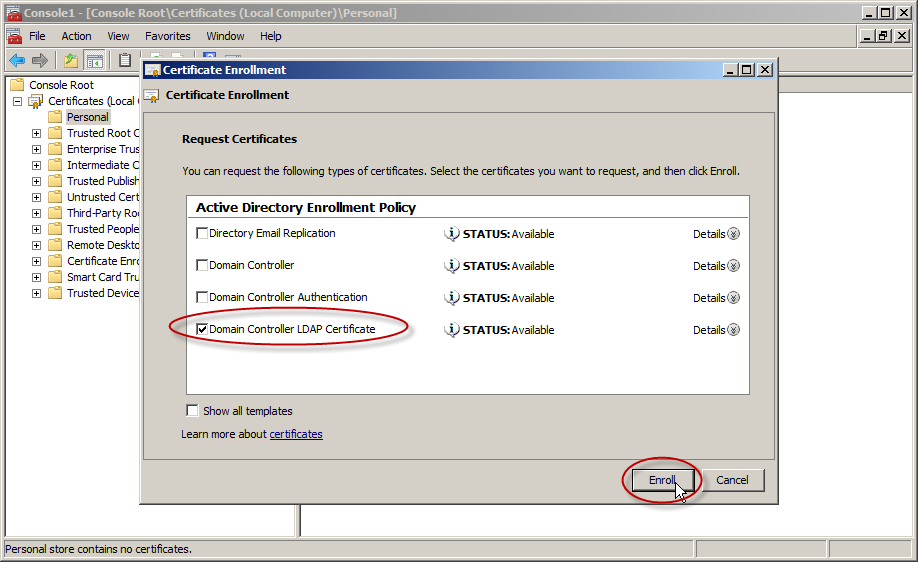
- In the console tree, expand Certificates (<computer>), right-click Certificates, click All Tasks, and then click Request New Certificate. Note: You cannot do this if you’re connected to a remote DC.
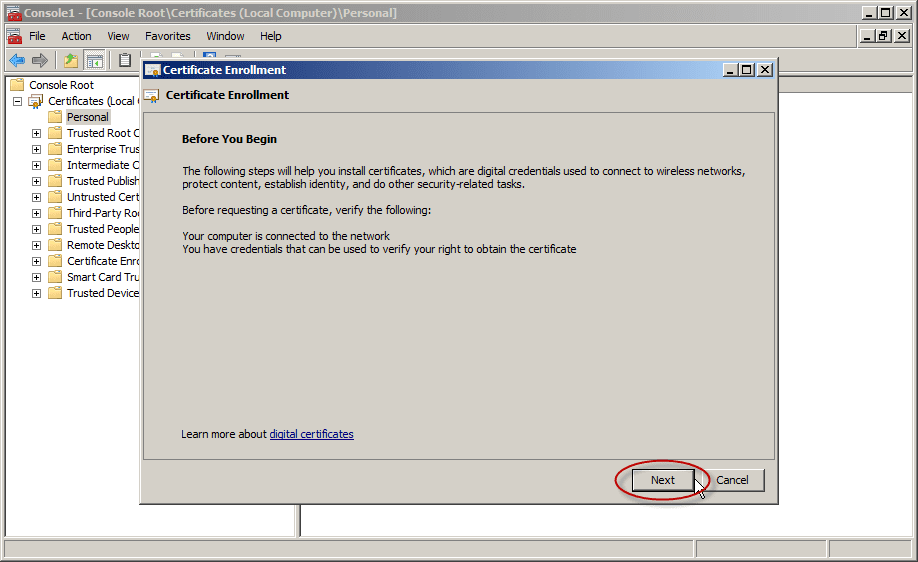
In Certificate Enrollment, click Next.
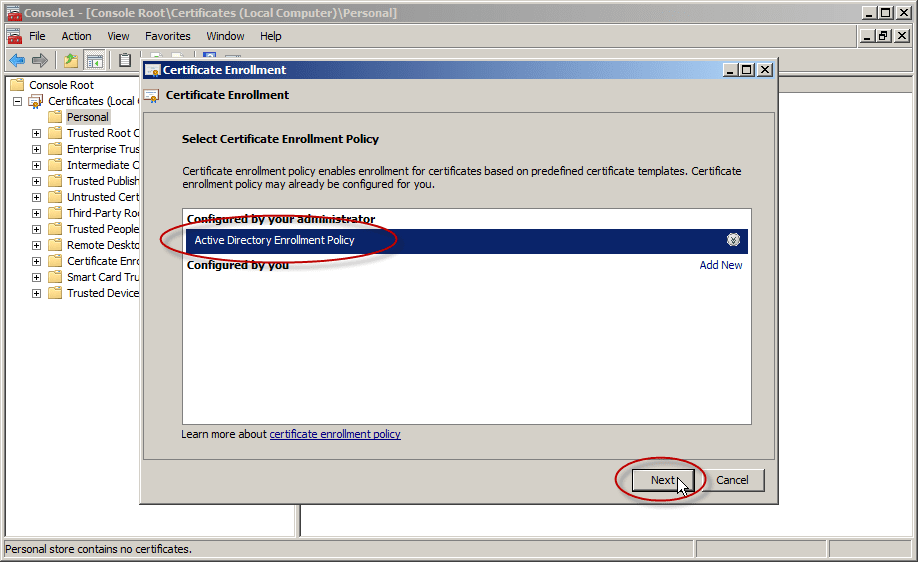
In the Select Certificate Enrollment Policy, choose Active Directory Enrollment Policy (default) and click Next.
- Select a certificate that allows for server authentication. You may want to use a custom certificate as described in Publishing a Certificate that Supports Server Authentication. Now go ahead and click Enroll.
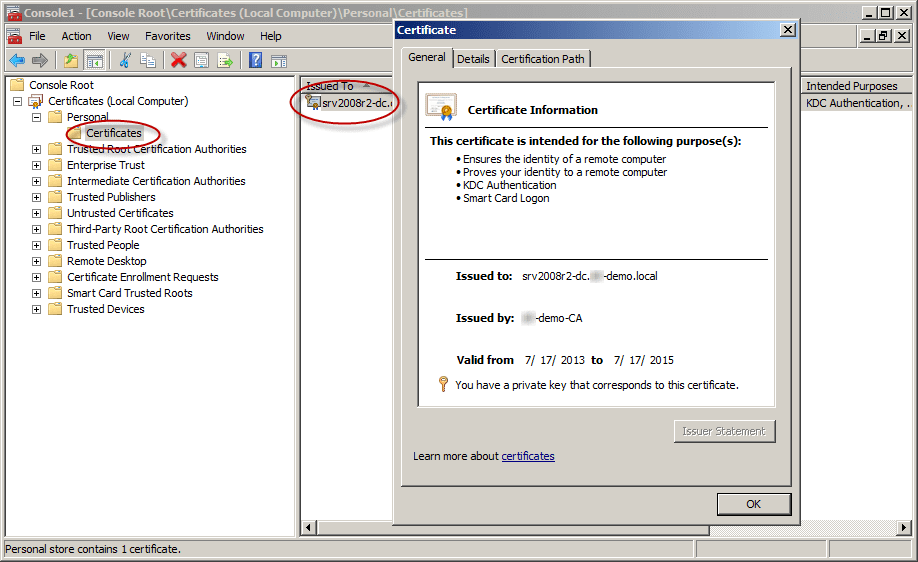
- The process may take a few seconds to complete. Click Finish in the Certificate Enrollment dialog box. Now you have a digital certificate for the first DC!
- To check your shiny new certificate, in the results pane double-click the certificate that you received to open Certificate properties.
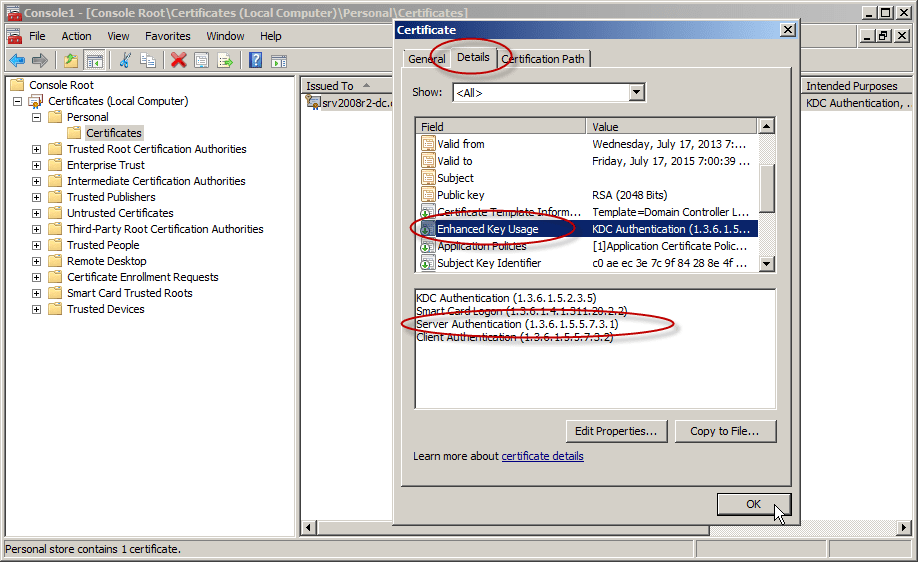
Click the Details tab. In the Field column, go ahead and select Enhanced Key Usage. You’ll want to confirm that the Server Authentication (1.3.6.1.5.5.7.3.1) is listed.
- Repeat this on all the DCs on which you need to enable LDAPS.
Test the LDAP over a TLS Connection
To test if LDAP over TLS works properly, use the ldp.exe tool.
Note: If ldp.exe is not available on your system, you will need to install the Active Directory Directory Services (AD-DS) management tools from the Windows Remote Server Administration Kit (RSAT):
Download Remote Server Administration Tools for Windows 7 with SP1Download Remote Server Administration Tools for Windows 8
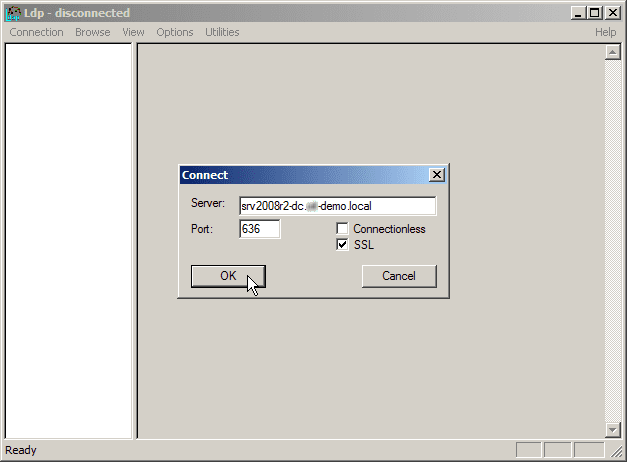
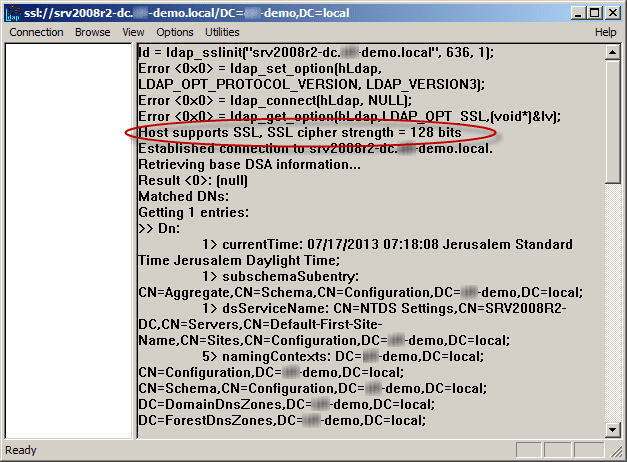
- Open a command prompt and type ldp. Click Enter. The LDP application window appears.
- Select Connection, then Connect. The Connect dialog box appears.
- In the Server text box, type the name of your AD server. For this example, type the fully qualified domain name (FQDN) of the DC, just as it appears in the Subject Alternative Name (SAN) of the Digital Certificate.
- In the Port text box, type 636.
- Check the box for SSL.
- Click OK. Now, without the above procedure you will not be able to connect.
After the procedure, note that “Host supports SSL, SSL cipher strength = 128 bits”.
Note: If you try to connect to the right DC but do not use the same FQDN as was listed inside the issued certificate (for example, using the IP address instead), you will not be able to connect using LDAPS.
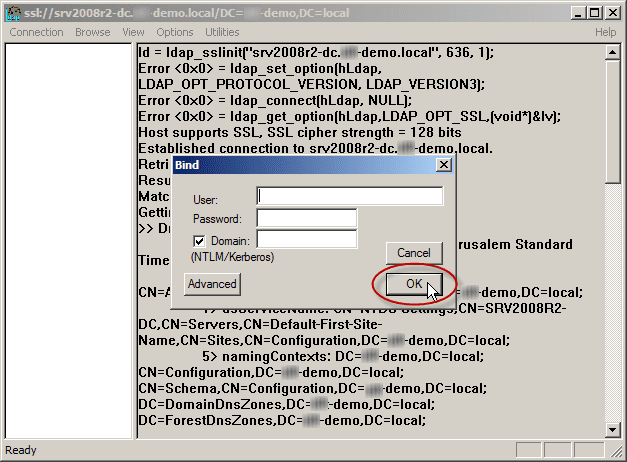
- Select the Connection menu, click Bind, and then click OK.
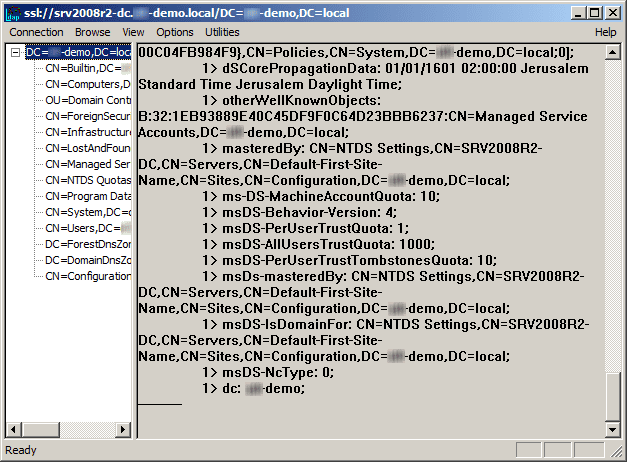
The command output should display the user name and domain name that you used for binding, if LDAPS is configured properly. You can start browsing through the AD tree.
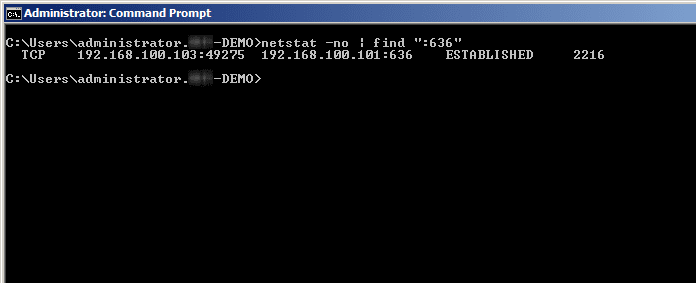
If you use the command: netstat -no | find “:636”, you will find the connection to the DC.
Enjoy.