Disabling Access to Removable Storage in Windows 7, Windows Server 2008 R2, and Later
How can I disable access to removable storage in Windows 7 and later?
Starting in Windows 7 and Server 2008 R2, Microsoft added some additional controls to make it easier to block access to removable storage, including USB sticks and DVD ROM drives. In this article, I’ll show you how to apply a policy to quickly block all removable storage.
Convenience Vs. Security
Removable media, especially in the form of USB sticks, is especially useful for quickly transferring files from one device to another when there is no network available. As with many convenient technologies, the ease of use can often be outweighed by the security risks. USB sticks are a common source of malware, making it possible for users to remove large amounts of data from corporate systems very quickly. Blocking removable storage can also be useful on servers that are not physically secured, as is often the case in small branch offices.
Office Politics
Before implementing a policy to block removable storage, you should assess whether there is a current legitimate use for removable storage on your network. Plan to make some exceptions to any blanket rules if required.
Users will often work with USB sticks in preference to more official mechanisms such as file servers or email because of restrictions in file sizes, quotas, security permissions or a slow network. If you suspect that USB sticks are being used as a workaround because of a perceived or real inconvenience, you should consider rectifying that situation before blocking USB drives.
Create a Policy to Block Removable Storage
To block access to removable storage on your network, open the Group Policy Management Console (GPMC) on Windows 7 (or later) or Server 2008 R2 (or later) using a domain account that has permission to create new Group Policy Objects (GPOs).
- In the left pane of GPMC, expand your AD forest and domain.
- Right click the Group Policy Objects folder and select New from the menu.
- In the New GPO dialog, name the GPO Block Removable Storage and click OK.
- Click the Group Policy Objects folder in the left pane.
- Right-click the new GPO in the right pane of GPMC and select Edit from the menu.
- In the Group Policy Management Editor window, expand Computer Configuration > Policies > Administrative Templates > System > Removable Storage Access.
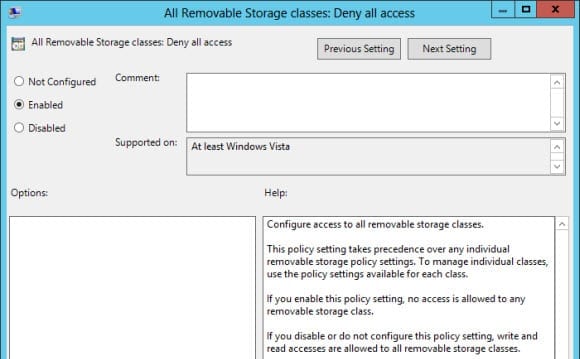
- In the right pane of the editor window, double-click All Removable Storage classes: Deny all access.
- In the policy setting dialog box, select Enabled and click OK.
- Close the Group Policy Management Editor window.
- In the left pane of GPMC, right-click your AD domain or an Organizational Unit and select Link an Existing GPO here from the menu.
- In the Select GPO dialog, choose the Block Removable Storage GPO and click OK.
Once Group Policy has updated on the affected machine(s), which you can force using the gpupdate command if you don’t want to wait, users will not be able to write to, read from, or execute files stored on removable storage.
Other Ways to Control Access to Removable Devices
The method I’ve described above is an all-or-nothing solution. While you can make exceptions to the rule, you might want to consider more flexible options. BitLocker Group Policy settings allow you to block devices that are not encrypted using BitLocker. Additionally, Device Installation Control settings in Group Policy can be used to prevent users from adding new hardware – including USB sticks – to their PCs, with the ability to white or blacklist hardware by GUID.