Designing a DMZ for Azure Virtual Machines
This article will show you three designs, each building on the other, for a demilitarized zone (DMZ) or perimeter network for Internet facing n-tier applications based on Azure virtual machines and networking.
The DMZ
The concept of a DMZ or perimeter network is not new; it’s a classic design that uses a layered network security approach to minimize the attack footprint of an application.
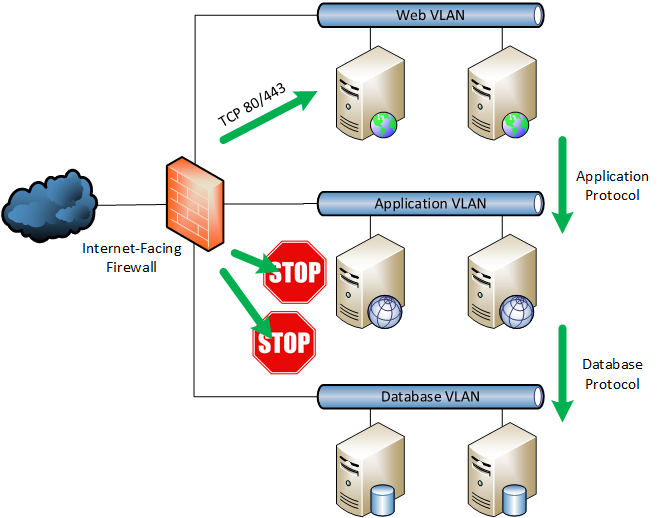
In a simple design:
- Web servers are placed in one VLAN, with just TCP 80 and TCP 443 accessible from the Internet.
- Application servers are in another VLAN. Web servers can communicate with the application servers using just the application protocol. The Internet has no access to this VLAN.
- Database servers are in a third VLAN. Application servers can communicate with the database servers using only the database communications protocol. Web servers and the Internet have no access to this VLAN.
You can modify this design in many ways, including:
- Adding additional application layer security.
- Including reverse proxies.
- Using logical implementations of multiple VLANs by using other methods of network isolation, such as network security groups (NSGs) in Azure.
So how do you recreate this concept in Azure for virtual machines? I’ll present you with three designs from Microsoft, each of which builds on the concepts of the previous ones.
Network Security Groups
The first and simplest way to build a DMZ in Azure is to use network security groups (NSGs). An NSG is a five-tuple rule that will allow or block TCP or UDP traffic between designated addresses on a virtual network.
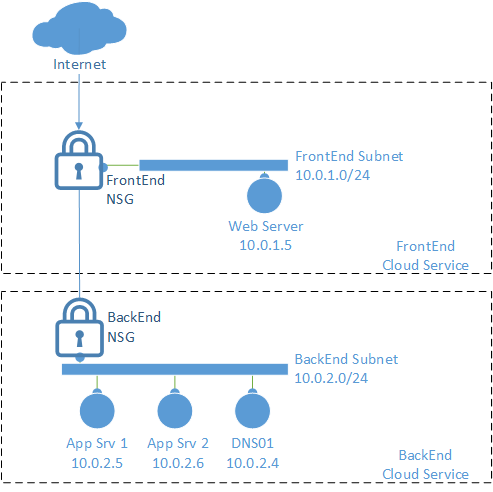
You can deploy an n-tier solution into a single virtual network that is split into two or more subnets; each subnet plays the role of a VLAN, as shown above. NSG rules are then created to restrict network traffic. In the below diagram, NSGs will:
- Allow web traffic into the FrontEnd subnet.
- All application traffic to flow from the FrontEnd subnet to the BackEnd subnet.
- Block all other traffic.
The benefit of this design is that it is very simple. The drawback of this design is that it assumes that your potential hackers are stuck in the 1990s; a modern attack tries to compromise the application layer. A port scan of the above from an external point will reveal that TCP 80/443 are open, so an attacker will try to attack those ports. A simple five-tuple rule will not block that traffic, so the hacker can either flood the target with a DDOS attack or compromise application vulnerabilities.
NSGs and a Firewall
Modern edge network devices can protect and enhance hosted applications with applications layer scanning and/or reverse proxy services. The Azure Marketplace allows you to deploy these kinds of devices from multiple vendors into your Azure virtual networks.
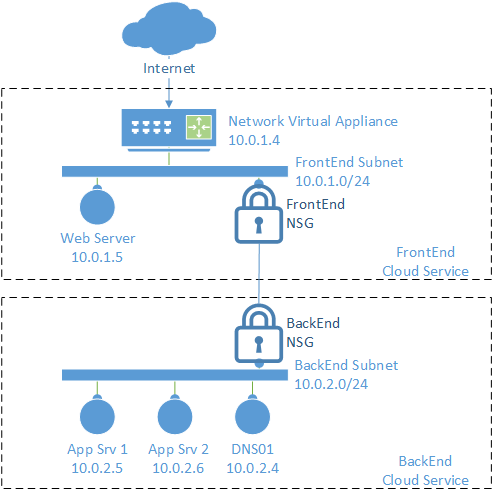
The following design below uses a virtual network appliance to protect an application from threats; this offers more than just simple protocol filtering because the appliance understands the allowed traffic and can identify encapsulated risks.
NSGS are deployed to enforce that all communications from the Internet must flow through the virtual appliance. NSGs will also control the protocols and ports that are allowed for internal communications between the subnets.
Ideally, we’d like to have all communications inside of the virtual network to flow through the virtual appliance, but the default routing rules of the network will prevent this from happening.
User Defined Routes, NSGs, and a Firewall
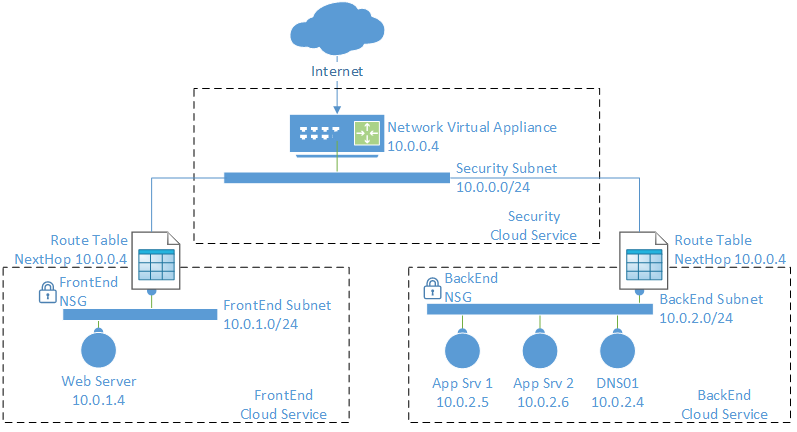
We can override the default routes of a virtual network using user-defined routes (UDRs). The following design uses one subnet in a single virtual network for each layer of the n-tier application. An additional subnet is created just for the virtual firewall appliance, which will secure the application.
UDRs are created to override the default routes between the subnets, forcing all traffic between subnets to route via the virtual firewall appliance. NSGs are created to enforce this routing and block traffic via the default routes.
The result is a DMZ where the virtual appliance controls all traffic to/from the Internet and between the subnets.
Tip: Try to use a next generation firewall and compliment this with defense with additional security products that will work with the Azure Security Center so that you have a single view of all trends and risks.