Following TechEd Europe 2015, I posted an article that listed new features of the next version of Hyper-V in Windows Server 2016. Recently, I also reported that Microsoft would be providing a new headless installation of Windows Server 2016, called Nano Server, which would be optimized for cloud infrastructure and born-in-the-cloud applications. Microsoft also recently announced that Windows Server 2016 would have support for containers, including support from Hyper-V for a more secure deployment model. The announcements continued at Ignite 2015, as Microsoft released more information on what new Hyper-V features are included in the Technical Preview 2 release of Windows Server 2016.
Shielded Virtual Machines
A big hindrance to adoption of cloud services is trust. This can also be an issue for enterprise deployments, where some organizations may not trust the fabric administrators, where they choose to deploy physical servers instead.
Windows Server 2016 provides a new feature where virtual machines are shielded:
- Virtual hard disk encryption via a virtual TPM chip in the virtual machine and BitLocker enabled in the guest OS
- Encrypted in-flight virtual machines (Live Migration)
- Preventing access to memory or code of the virtual machine, at rest or running
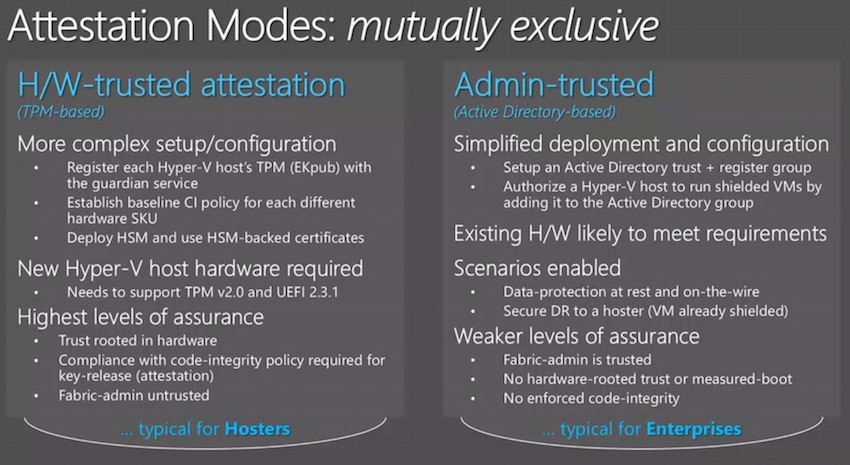
This feature is available in two modes, with a service called the Host Guardian Service (HGS) running in a dedicated AD forest managing virtual machine security:
- Admin-trusted attestation: This is the easiest model to deploy. Hosts are placed into a group and the HGS is configured to only allow virtual machines on members of this group.
- Hardware-trusted attestation: This solution requires a HSM for the HGS and each host must have TPM 2.0 chips (not available yet) and UEFI 2.3.1. This hardware offers greater security with measured boot and enforced hypervisor and management OS kernel code integrity.
Linux Secure Boot
An additional feature is the ability to enable secure boot for Linux guest operating systems in Generation 2 virtual machines. This feature is already available for Windows Server 2012 R2 Generation 2 virtual machines on Windows Server 2012 R2 hosts. When secure boot is enabled, the machine’s hardware protects kernel mode code from being compromised, possibly by root kits.
Host Resource Protection
This is a security feature that was born specifically for Azure’s needs and will trickle down to everyone else. Azure is constantly under attack and because a public cloud’s nature, these attacks often come from virtual machines that are hosted by the service itself. These machines consume valuable resources in an attempt to attack the infrastructure.
Host Resource Protection uses “patterns of access” to identify virtual machines that are not playing fair on the infrastructure and chokes resource usage. This action slows down the attack, frustrates the attacker, and ensures that normal machines have access to valuable services. To date, Azure and Hyper-V have yet to have had a successful break-out attack, where an attacker breaks out from a compromised machine and into host or another machine via the hypervisor. This mechanism also cripples the effectiveness of denial of service attacks that are launched against Hyper-V from within a guest OS.
Storage Resiliency
Hyper-V already has means for dealing with storage connectivity glitches. MPIO (iSCSI and host bus adapters) and load balancing/SMB Multichannel (SMB 3.0) offer multiple paths of connectivity between a host and a different tier of storage (SAN or Scale-Out File Server). In the event of a host becoming isolated from storage, Redirected IO (block level over SMB 3.0 in WS2012 R2) can be used to redirect storage traffic across the compute cluster networks to another host that proxies the storage traffic to the storage tier.
Microsoft is introducing a third level of storage resiliency in Windows Server 2016. Normally the guest OS will panic and crash if a virtual machine has a failed storage operation. In Windows Server 2016, Hyper-V will intercept the timeout and place the virtual machine into a paused critical state. The virtual machine will be un-paused once storage connectivity resumes.
Cluster Resiliency
The act of failing over a virtual machine after a clustered host fails to send a heartbeat can be disruptive:
- The virtual machine is stopped.
- Ownership of the cluster resource is changed to another host that continues to heartbeat and has quorum.
- The virtual machine starts up, booting up the guest OS and then restarting the services that were previously running.
This disruption is often unwarranted; many host heartbeat failures are caused by transient errors, such as a switch crash or a human cabling error, which quickly go away. In these events, a failover can happen and can cause a longer service outage than the root cause.
A Windows Server 2016 Hyper-V cluster will not immediately jump into failing over virtual machines after a timeout. Instead, the host goes into an isolate state and the virtual machine goes into an unmonitored state, where the virtual machine continues to run on the isolated host. If the node resumes responding to heartbeats within four minutes (the configurable default at this time), then the already running virtual machine returns to a healthy state; otherwise it is failed over.
If a host is deemed to be flapping, it is placed into quarantine. This means that no more virtual machines can be placed on the host and all virtual machines are live migrated by default to the remaining healthy hosts. This action minimizes service downtime and allows administrators to take their time investigating the issue.
Shared VHDX
This version 1 feature of Windows Server 2012 R2 enables guest clusters to use a VHDX file for common cluster storage. Unfortunately, Shared VHDX was quite limited, but this changes in Windows Server 2016. TPv2 adds:
- Host-based backup of guest clusters and shared VHDX files without using an in-guest backup agent.
- Online-resizing of the shared VHDX file
PowerShell Direct
I might have gone a very long way to have this feature for my demos at Microsoft Ignite. With PowerShell Direct, you can run PowerShell against the guest OS of a machine without network access. All you need are credentials for the guest OS. This will make deployment, configuration, and management much easier.
ReFS Accelerated VHDX Operations
Some disk operations are resource expensive. Creating a fixed VHDX file, the preference for many of us, can take quite some time to complete. Merging checkpoints, which are required for file-based backup, can create a lot of IOPS and limit the scalability of backup. If you are lucky, you have a SAN that supports Offline Data Transfer (ODX). But few people are in that position.
ReFS is Microsoft’s file system of the future and is used in Stoarge Spaces Direct (S2D) storage architecture, which is also new in Windows Server 2016. ReFS will accelerate the creation of fixed VHDX files and enables a zero data copy merge of checkpoints, thus improving the performance of service deployment and file-based backup.
Second-Level Address Translation (SLAT) Requirement
All versions of Hyper-V, Windows 10, and Windows Server 2016 will require SLAT-capable processors in the host. Intel calls this Extended Page Tables (EPT) and AMD calls it Rapid Virtualization Indexing (RVI).


