Set it and Forget it is the Worst Practice in Azure
I’ll admit that I may have done a not-so-best-practice type of thing, I have not gone into the Azure Portal in quite a long time (around 2 months). Now everyone’s usage of Azure is different and for me, I spend most of my time in the Azure Storage world, with many applications interacting with those storage accounts (properly provisioned of course). But, I got into a mode where I had not gone into the Azure Portal in a while and that is not a best practice. In this blog post, I’ll explain why.
Azure is watching out for you
The main reason I’m calling this a worst practice is because I was missing out on advice that Azure has for me. The various services in Azure that review your usage and what is using it (including threats) are always working on your behalf, with a lot of them available at no cost.
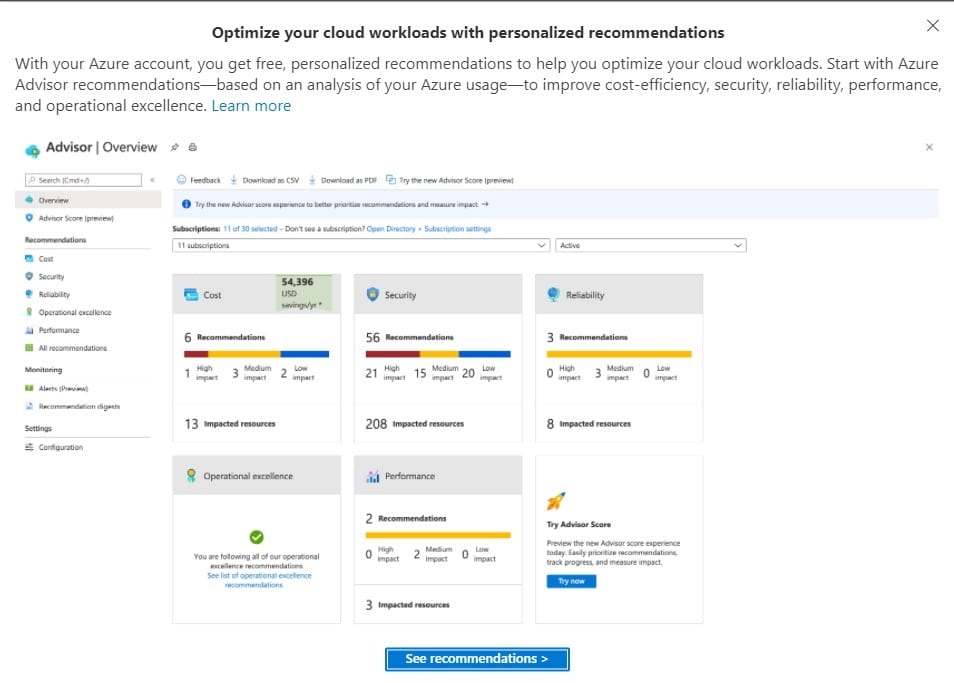
I’ve long said that every time you log in and log out of the Azure Portal, your first and last stops should be into Azure Advisor to see what is new since your last session and if anything happened during this session that changes your recommendations, security, performance or other categories. The good news about logging in for the first time in a while is that I am reminded to check out Azure Advisor recommendations are there for me:
Azure Security Best Practices
When I went into the recommendations, there were not necessarily surprises or tragedies but there could have been as some services (like Azure VMs) may not have been updated since the last login. When I do log in, I can see that it has been two months since my services were accessed in the Azure portal (which is as I’d expect):
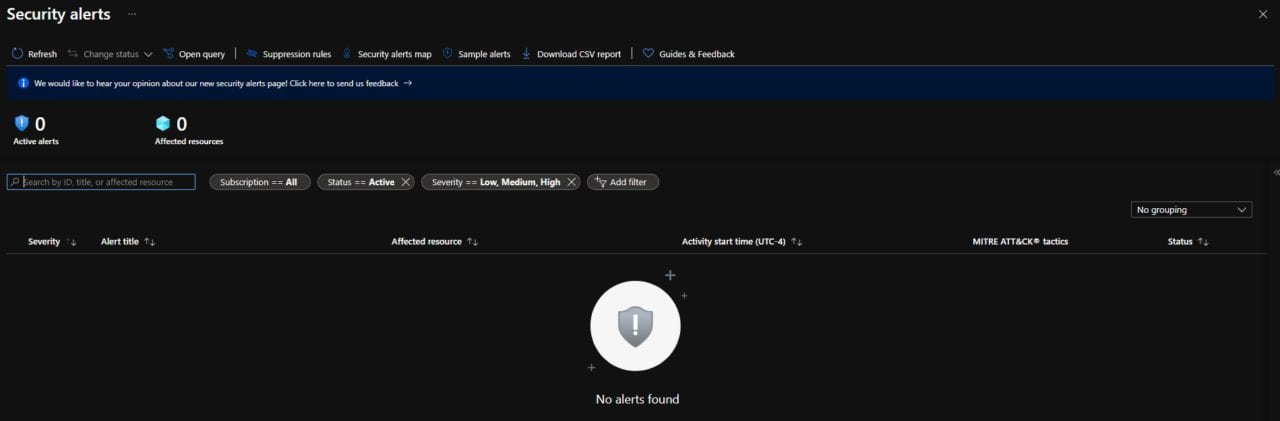
An important area to go beyond that is the Security Center. Both the Security Alerts and Recommendations are a good area to go for more specific information and security perspective on the services you are using in Azure.
I did not have any alert in Azure, which was a good thing:
In the recommendations section, I wish I could say that I came through with the same level of insight. But the practicality of some of the suggestions should be considered with a grain of salt or consideration of the cost implications as some of the recommendations align to consuming additional Azure services.
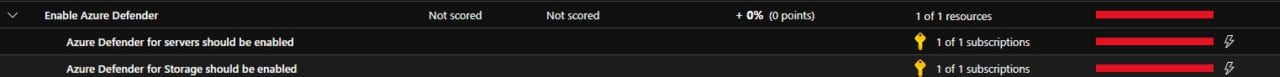
For example, I had the recommendation to enable Azure Defender for the Storage accounts I have:
Configuring Azure Services Cost Advice
I currently don’t have this on the 10 Storage accounts I am using, but according to current pricing in my region if I wanted to add it for Storage, it would be $0.02 for 10K transactions. For Servers (Azure VMs) would be another $0.02/Server/Hour. The Storage account isn’t so expensive, but for an Azure VM that translates to $14.60/Server/month. This is something to consider, but for highly sensitive data (not in use in my Azure account) or maybe something unencrypted (again not in my Azure account) this may be a necessity.
While I didn’t find anything horribly wrong, I’ll admit, I was a bit worried I may when I logged in after so long. I’ll promise not to do my own worst practice again!