In today’s Ask the Admin, I’ll provide a brief overview of the anomaly detection features used by Microsoft to keep cloud identities safe and how these features have been made commercially available to enterprises in the form of Azure Active Directory (AAD) Identity Protection.
Microsoft claims that 60 percent of all successful attacks rely on compromised credentials, so extra care needs to be taken to protect user identities in Active Directory (AD), and Microsoft’s cloud-based directory services solution, AAD. Microsoft Advanced Threat Analytics (ATA) is a product for protecting user accounts in on-premises AD, and while I haven’t seen it stated anywhere, it’s likely that many of the features in AAD Identity Protection are provided by ATA behind the scenes.
For more information on protecting user identities in on-premise AD using Microsoft ATA, see What Is Microsoft Advanced Threat Analytics? on the Petri IT Knowledgebase.
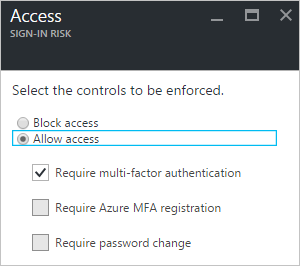
AAD Identity Protection goes beyond simple monitoring and reporting by allowing organizations to set risk-based policies that respond to issues when a specified risk level is reached. For instance, a policy could block access, force a user to reset their password, or stipulate the use of multifactor authentication. AAD configuration issues are also flagged, such as the alerts from AAD Privileged Identity Management and the presence of unmanaged cloud apps.
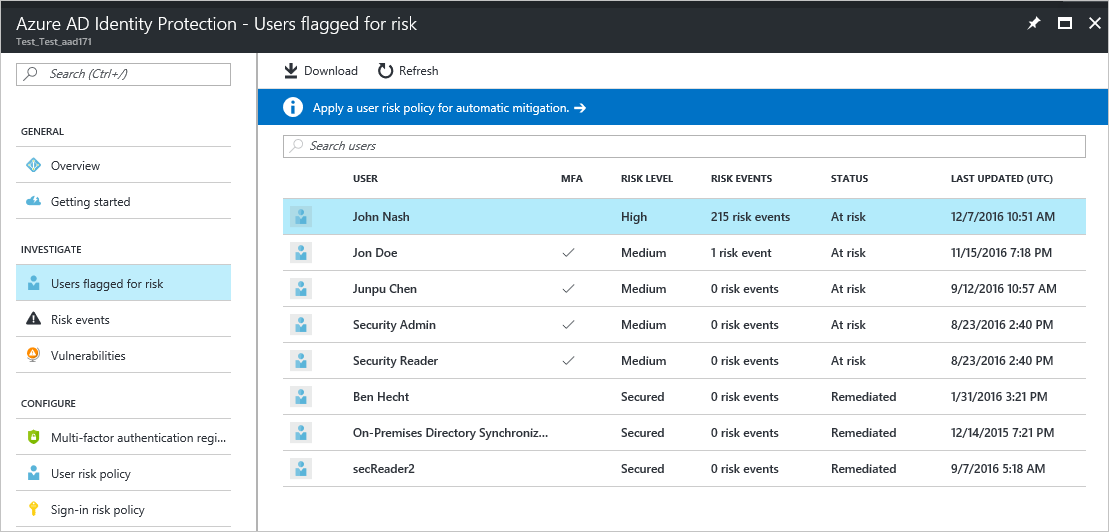
There are six risk event types that AAD Identity Protection detects and each is assigned a risk level: High, Medium, or Low.
- Users with leaked credentials
- Sign-ins from anonymous IP addresses
- Impossible travel to atypical locations
- Sign-ins from unfamiliar locations
- Sign-ins from infected devices
- Sign-ins from IP addresses with suspicious activity
Just like Microsoft ATA, AAD Identity Protection uses machine learning and behavioral analysis to detect malicious activity related to user identities. For each incident that is detected, a risk event is created. Some risk events can be detected in real-time, while others are detected offline. To mitigate risk events, actions defined in policy are activated when a certain risk level is reached.
The default risk level threshold is set to Medium, and Microsoft recommends planning carefully because although high thresholds reduce the frequency at which policies trigger mitigation actions, it also increases the risk of malicious activity. Low and Medium risk thresholds might introduce more inconvenience for users but are more likely to prevent credentials being compromised. Identity Protection allows administrators to select the users to which policies apply, so organizations can create policies for different risk groups.
Identity Protection is available as part of AD Premium P2 subscriptions, and you can sign up for a free trial at Microsoft’s website here.
In this article, I explained how AAD Identity Protection helps keep cloud user identities safe.



