Patch Tuesday in November 2021 sees Microsoft release patches to address 55 CVEs, including fixes for 6 zero-day bugs. There are updates for products including Windows, Windows Server, Office, Exchange Server, Active Directory, Microsoft Dynamics, Hyper-V, and Azure Real Time Operating System (RTOS), which is ThreadX RTOS, an embedded real-time operating system that Microsoft purchased from Express Logic in 2019.
Windows and Windows Server
Another month and Microsoft patches a Remote Desktop Protocol (RDP) bug (CVE-2021-38666) in Windows. The patch fixes a vulnerability in the RDP client software that’s built into Windows and Windows Server. An attacker could use the vulnerability to install malicious code on a client system if they were able to trick a user into connecting to a malicious RDP server. This bug affects all versions of Windows, going back to Windows 7 and Windows Server 2008.
There’s a patch this month for a remote code execution vulnerability in the Virtual Machine Bus (VMBus) in Windows (CVE-2021-26443). The bug could allow an attacker to escape from a guest virtual machine (VM) to the host Hyper-V server. An attacker could send a specially crafted message on the VMBus Channel to the host operating system and then run arbitrary code on the host.
There are several elevation of privilege (EoP) bugs fixed in Windows this month that affect NTFS and Active Directory (AD). The bugs in AD could allow an attacker to move laterally across devices, so it’s important to get your domain controllers (DC) patched. There’s also a patch for a bug that could be used to perform a denial-of-service (DoS) attack against Windows. An attacker could remotely launch a DoS attack against Windows without any permissions on the remote device. Finally, there’s a security feature bypass flaw being fixed for Windows Hello in Windows 10 and Windows Server 2019.
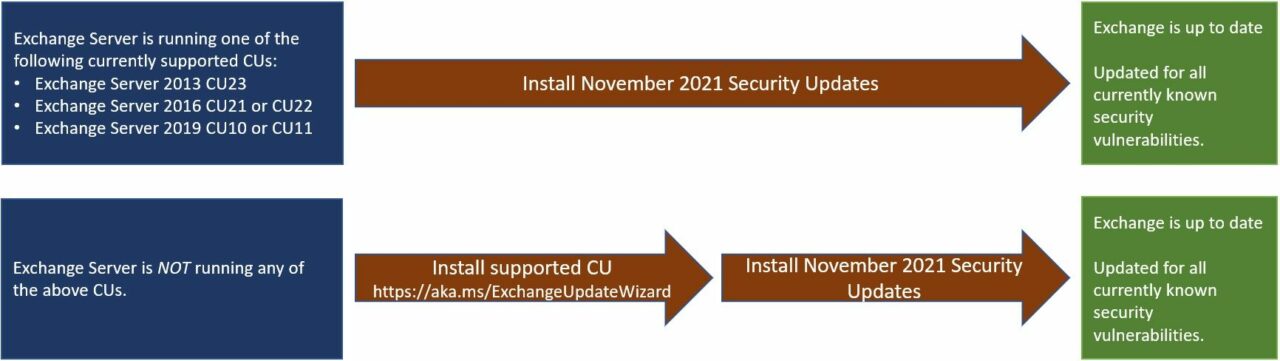
Microsoft Exchange Server
Exchange Server gets a fix for a remote code execution flaw (CVE-2021-42321) and Microsoft says that it is currently being used in the wild. Because Exchange Server is more vulnerable to attack than some other application servers, it’s wise to get this tested and deployed as quickly as possible. To help you get this patch deployed, Microsoft has published some information on how to patch your Exchange Server environment. CVE-2021-42321 affects Exchange Server 2016 and 2019, and it requires a hacker to authorize to Exchange. There is also a security update for Exchange Server 2013 this month.
Microsoft Office
A bug in Excel (CVE-2021-42292) could let an attacker execute code when opening a specially crafted document. Microsoft has released a patch, which it categorizes as a fix for a security bypass vulnerability. If you are using Office on macOS, be especially careful as there is currently no patch for this bug. Microsoft lists the bug as currently under attack and it affects all versions of Office dating back to Office 2013.
Here is a complete list of patched vulnerabilities released in the November 2021 Patch Tuesday updates:
Table 1
| Product | Impact | Severity | Article | Details |
| Microsoft Edge (Chromium-based) in IE Mode | Spoofing | Important | 5007186 | CVE-2021-41351 |
| Microsoft Malware Protection Engine | Remote Code Execution | Critical | Release Notes | CVE-2021-42298 |
| Windows Server 2016 | Remote Code Execution | Critical | 5007192 | CVE-2021-42279 |
| 3D Viewer | Remote Code Execution | Important | Release Notes | CVE-2021-43209 |
| 3D Viewer | Remote Code Execution | Important | Release Notes | CVE-2021-43208 |
| Azure RTOS | Information Disclosure | Important | Information | CVE-2021-26444 |
| Azure RTOS | Information Disclosure | Important | Information | CVE-2021-42323 |
| Visual Studio Code | Elevation of Privilege | Important | Release Notes | CVE-2021-42322 |
| Microsoft Exchange Server 2019 Cumulative Update 11 | Remote Code Execution | Important | 5007409 | CVE-2021-42321 |
| Microsoft Visual Studio 2019 version 16.11 (includes 16.0 – 16.10) | Elevation of Privilege | Important | Release Notes | CVE-2021-42319 |
| Microsoft Dynamics 365 (on-premises) version 9.0 | Remote Code Execution | Critical | 5008479 | CVE-2021-42316 |
| Azure Sphere | Information Disclosure | Important | Release Notes | CVE-2021-41376 |
| Azure Sphere | Information Disclosure | Important | Release Notes | CVE-2021-41374 |
| Azure RTOS | Elevation of Privilege | Important | Information | CVE-2021-42304 |
| Azure RTOS | Elevation of Privilege | Important | Information | CVE-2021-42303 |
| Azure RTOS | Elevation of Privilege | Important | Information | CVE-2021-42302 |
| Azure RTOS | Information Disclosure | Important | Information | CVE-2021-42301 |
| Azure Sphere | Tampering | Important | Release Notes | CVE-2021-42300 |
| Microsoft Exchange Server 2019 Cumulative Update 11 | Spoofing | Important | 5007409 | CVE-2021-42305 |
| Microsoft Visual Studio 2015 Update 3 | Elevation of Privilege | Important | 5007275 | CVE-2021-42277 |
| Microsoft Office LTSC 2021 for 32-bit editions | Remote Code Execution | Important | Click to Run | CVE-2021-42296 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-42291 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-42287 |
| Windows Server, version 20H2 (Server Core Installation) | Security Feature Bypass | Important | 5007186 | CVE-2021-42288 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-42285 |
| Windows Server 2012 R2 (Server Core installation) | Denial of Service | Important | 5007247 | CVE-2021-42284 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-42283 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-42282 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-42278 |
| Windows Server 2012 R2 (Server Core installation) | Remote Code Execution | Important | 5007247 | CVE-2021-42275 |
| Windows Server 2016 (Server Core installation) | Denial of Service | Important | 5007192 | CVE-2021-42274 |
| Windows 11 for x64-based Systems | Remote Code Execution | Critical | 5007215 | CVE-2021-26443 |
| FSLogix | Information Disclosure | Important | Release Notes | CVE-2021-41373 |
| Azure Sphere | Information Disclosure | Important | Release Notes | CVE-2021-41375 |
| Power BI Report Server | Spoofing | Important | 5007903 | CVE-2021-41372 |
| Microsoft Office 2013 Service Pack 1 (64-bit editions) | Remote Code Execution | Important | 5002038 | CVE-2021-41368 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-41367 |
| Microsoft Visual Studio 2019 version 16.11 (includes 16.0 – 16.10) | Remote Code Execution | Critical | Release Notes | CVE-2021-3711 |
| Microsoft Office Web Apps Server 2013 Service Pack 1 | Remote Code Execution | Important | 5002065 | CVE-2021-40442 |
| Windows Server 2012 R2 (Server Core installation) | Remote Code Execution | Critical | 5007247 | CVE-2021-38666 |
| Windows Server 2012 R2 (Server Core installation) | Information Disclosure | Important | 5007247 | CVE-2021-38631 |
| Windows Server 2012 R2 | Information Disclosure | Important | 5007247 | CVE-2021-38665 |
| Microsoft Office 2013 Service Pack 1 (64-bit editions) | Security Feature Bypass | Important | 5002035 | CVE-2021-42292 |
| Windows Server, version 20H2 (Server Core Installation) | Elevation of Privilege | Important | 5007186 | CVE-2021-42286 |
| Windows Server 2016 (Server Core installation) | Remote Code Execution | Important | 5007192 | CVE-2021-42276 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-41379 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-41377 |
| Windows 11 for ARM64-based Systems | Remote Code Execution | Important | 5007215 | CVE-2021-41378 |
| Windows Server 2012 R2 (Server Core installation) | Information Disclosure | Important | 5007247 | CVE-2021-41371 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-41370 |
| Windows Server 2012 R2 (Server Core installation) | Elevation of Privilege | Important | 5007247 | CVE-2021-41366 |
| Microsoft Exchange Server 2019 Cumulative Update 11 | Spoofing | Important | 5007409 | CVE-2021-41349 |
| Windows Server 2016 (Server Core installation) | Denial of Service | Important | 5007192 | CVE-2021-41356 |
| Windows Server 2016 (Server Core installation) | Elevation of Privilege | Important | 5007192 | CVE-2021-36957 |
| Windows Server 2016 (Server Core installation) | Elevation of Privilege | Important | 5007192 | CVE-2021-42280 |
Adobe Software
Unusually in the Patch Tuesday November 2021 updates, Adobe has only released fixes for four CVEs, plugging security holes in Creative Cloud Desktop, InCopy, and RoboHelp. The update for Creative Cloud patches a DoS bug that’s rated Important. InCopy gets a patch that fixes two bugs, one of which is a code execution flaw that’s rated Critical. And finally, RoboHelp Server gets a security hotfix that patches a bug that could let an attacker run arbitrary code. It is rated Critical.
Windows Update testing and best practices
Organizations looking to deploy this month’s patches should conduct thorough testing before deploying them widely on production systems. That said, applying the patches widely shouldn’t be delayed longer than necessary as hackers start to work out how to weaponize newly reported vulnerabilities.
Best practice is to make sure you have backed up systems before applying updates. Every month, users experience issues with Windows updates that lead to systems not booting, application and hardware compatibility issues, or even data loss in extreme cases.
There are backup tools built into Windows and Windows Server that you can use to restore systems in the event a patch causes an problem. The backup features in Windows can be used to restore an entire system, or files and folders on a granular basis.
Patch Tuesday November 2021
If you have any problems with the Patch Tuesday November 2021 updates, please let us know in the comments below. Other readers might be able to share their experiences in how to roll back problematic updates or mitigate issues caused by patches that are important to have in place.
But that is it for another month and happy patching!