Microsoft patches 103 security vulnerabilities this month, including PrintNightmare, a Windows DNS Server bug, 3 elevation of privilege vulnerabilities in the Windows kernel, and much more.
Windows and Windows Server
Let’s start with the bug that surfaced earlier in July month called PrintNightmare.
PrintNightmare
Microsoft issued an out-of-band cumulative update (CU) for a remote execution flaw (CVE-2021-34527), which allows local privilege escalation, in the Windows Print Spooler service. It was actively being exploited in the wild. The vulnerability could allow a remote attacker to run code of their choice on a compromised system.
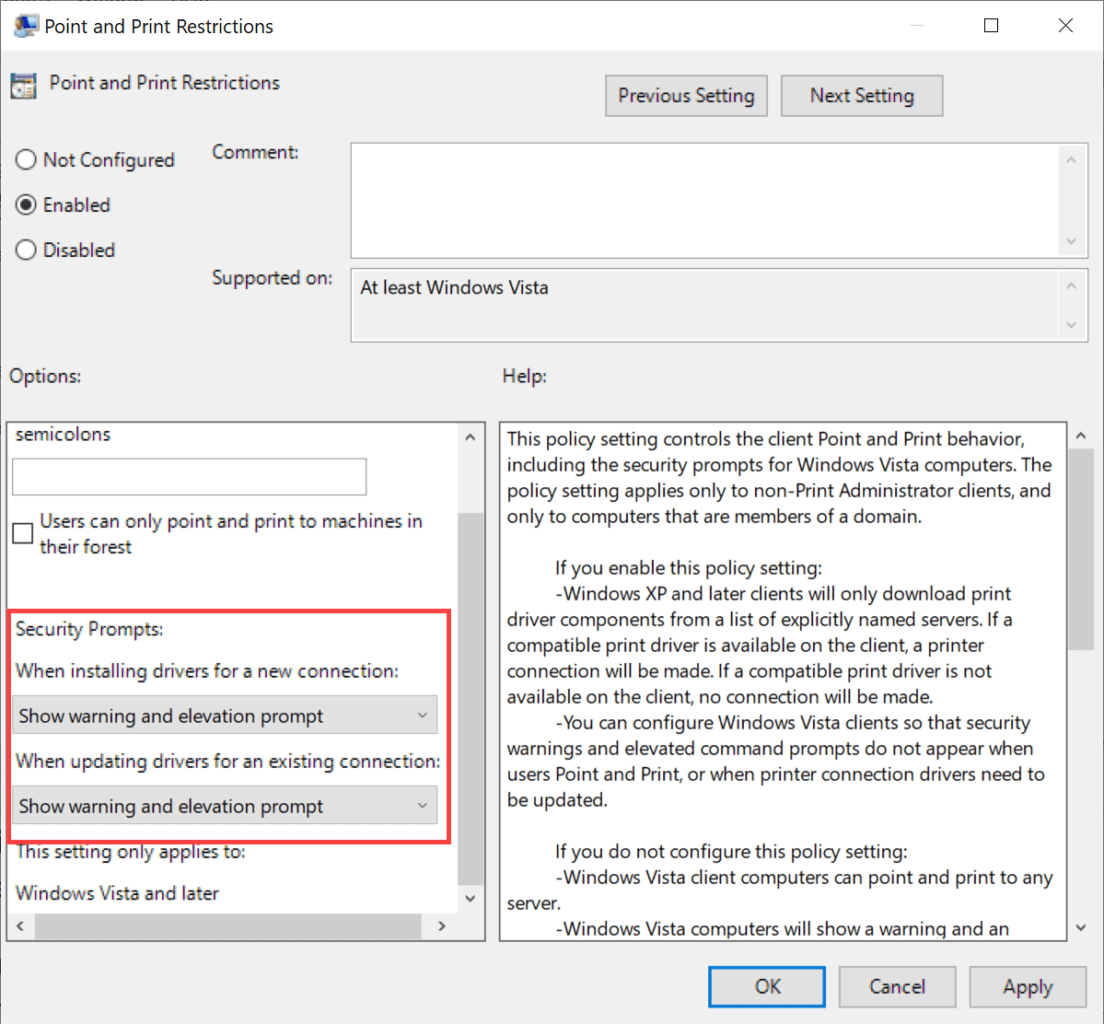
In addition to applying the update, you should check that the following registry values are set to 0 (zero) for complete protection:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
In a blog post, Microsoft said that the fix issued 6th July ‘fully addresses the public vulnerability, and it also includes a new feature that allows customers to implement stronger protections’. Although, some researchers didn’t agree that the fix fully resolved the issue with the Print Spooler service.
July 2021 and later updates for Windows contain a new protection that prevents non-administrators, including delegated admin groups like printer operators, installing signed and unsigned printer drivers to a print server. After the update, only administrators can install signed and unsigned printer drivers to a print server.
There’s also a new control for overriding all Point and Print Restrictions Group Policy settings so that only administrators can install printer drivers on a print server.
Microsoft says the fixes for CVE-2021-34527 don’t affect the default Print and Point driver installation behavior. If a client device connects to a trusted print server and downloads and installs drivers. The fixes are intended to block attackers installing a malicious driver on a print server, whether locally or remotely.
For more information on the new controls, check out KB5005010 on Microsoft’s website.
As always, make sure you test any out-of-band updates and monthly CUs. The PrintNightmare update seems to have caused problems for some users, including not being able to use printers redirected through Remote Desktop.
Scripting engine vulnerability
CVE-2021-34448 is a critical remote code execution bug in the scripting engine built into Windows. It requires user interaction, and it is being actively exploited.
Windows kernel flaws
CVE-2021-33771 and CVE-2021-31979 are critical elevation of privilege kernel flaws, which are both being actively exploited. Neither requires any user interaction.
CVE-2021-34458 is another remote code execution bug in the Windows kernel. It doesn’t require elevated privileges or user interaction to exploit.
Windows Server DNS
CVE-2021-34494 is a remote execution vulnerability in the DNS server service. Because Active Directory relies on the DNS server service in Windows, it’s important to get this vulnerability patched.
Exchange and SharePoint Server
There are 7 flaws patched for Exchange Server this month. Including CVE-2021-31206, which was discovered during the Pwn2Own computer hacking competition. SharePoint Server also gets patches for 3 RCE flaws, one spoofing bug, and two information disclosure bugs.
Microsoft Office
Microsoft 365 Apps for Enterprise get patched for two RCE flaws and a security feature bypass vulnerability, all rated important.
Adobe software
And finally, Adobe Acrobat and Reader both get updates for several critical and important security vulnerabilities.
And that is it for another month!