Mitigating Spectre Variant 2 with Retpoline on Windows
Microsoft patched the Spectre variant 2 vulnerability (CVE-2017-5753), a branch target injection microprocessor flaw, back in January 2018 along with two other processor bugs, CVE-2017-5753 and CVE-2017-5754. But the original Spectre v2 patch caused performance to drop by up to 30% under some load conditions. Microsoft distributed a fix for the performance issues at the beginning of March. Developed by Google and called Retpoline, the patch can be applied to CPUs that have predictable Return Stack Buffer (RSB) behavior. For Intel processors, that means that Retpoline can’t be used with Skylake and later generation CPUs, although Import Optimization can be enabled.
How to Enable Retpoline
The Retpoline update was part of the March 1st cumulative update for Windows 10 version 1809 and later (KB4482887), and it is disabled by default. But customers who wish to manually enable Retpoline on their systems can by manually editing the registry. Use the reg.exe command-line tool to add two keys to the registry and then reboot the system. The keys below are for client SKUs.
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0x400 reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 0x400
If you want to enable Retpoline on server SKUs of Windows, use the following commands and reboot:
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0x400 reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 0x401
The registry keys are for customers that have the default mitigation settings already enabled. Windows 10 client SKUs have the mitigations enabled by default. If you add the registry keys on server SKUs, default mitigations will be enabled. For more details, read Microsoft’s blog post carefully here.
Speculation Control Settings
To check the status of speculation control mitigations on your system, use the Get-SpeculationControlSettings PowerShell cmdlet. Install-Module downloads the SpeculationControl module from GitHub.
Install-Module -Name SpeculationControl Import-Module SpeculationControl Get-SpeculationControlSettings
Before running Get-SpeculationControlSettings, the PowerShell execution policy should be set to RemoteSigned. If Retpoline and Import Optimization are enabled on the system, you should see the following line in the output:
BTIKernelRetpolineEnabled : True
BTIKernelImportOptimizationEnabled : True
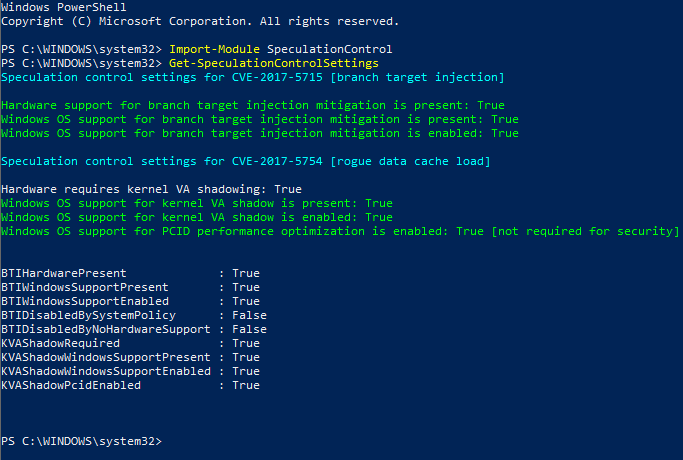
In the screenshot above, you can see that on my system Retpoline isn’t enabled.
$SaveExecutionPolicy = Get-ExecutionPolicy Set-ExecutionPolicy RemoteSigned -Scope Currentuser
To reset the execution policy, run:
Set-ExecutionPolicy $SaveExecutionPolicy -Scope Currentuser
Retpoline Arrives Early for Windows 10
The Retpoline patch for Windows 10 was originally slated to arrive in the Windows 10 May 2019 Update but Microsoft will enable the fix in Windows 10 version 1809 for some users. Most users won’t need to do anything, and Microsoft will automatically enable the patch at some point in the future if it is compatible with your system and it has tested to be stable.
According to Google, Retpoline has negligible impact on performance, as opposed to the mitigations most OS vendors put in place. So, customers who want to do their own testing or have specific cases where they would benefit from enabling the patch manually, like on server workloads, can do so using the registry keys provided.




