Microsoft Warns About New Zero-Day Vulnerabilities in Exchange Server

Microsoft has issued an advisory about two new zero-day vulnerabilities affecting Exchange Server. The critical flaws, which were discovered by a Vietnamese cybersecurity company GTSC last month, impact on-premises installations of Microsoft Exchange Server 2013, 2016, and 2019.
Microsoft’s Security Response Center (MRSC) detailed that the two vulnerabilities are tracked as CVE-2022-41040 and CVE-2022-41082. The first one is a server-side request forgery (SSRF) flaw and the second vulnerability allows remote code execution on vulnerable Exchange installations via PowerShell.
Microsoft has not shared any details about the security flaws, but it believes that the threat actor requires authenticated access to Exchange Server for successful exploitation. Moreover, GTSC found that the attackers abused these vulnerabilities to target the victim’s systems and infect enterprise networks.
“After successfully mastering the exploit, we recorded attacks to collect information and create a foothold in the victim’s system,” GTSC explained. “We detected webshells, mostly obfuscated, being dropped to Exchange servers. Using the user-agent, we detected that the attacker uses Antsword, an active Chinese-based opensource cross-platform website administration tool that supports webshell management.”
Microsoft Exchange Server flaws are being used in cyberattacks
Unfortunately, Microsoft has yet to release a patch to address the zero-day vulnerabilities in on-premises environments. However, security researcher Kevin Beaumont said on Twitter that the flaws are being actively exploited by attackers in the wild, which have already infected several Exchange Servers.
Microsoft has detailed a few temporary mitigation methods to help enterprise customers prevent attacks on Exchange Servers. The company has advised that IT admins should add a blocking rule in IIS Manager as well as block the ports (5985 (HTTP) and 5986 (HTTPS)) used for Remote PowerShell. Microsoft says that these vulnerabilities don’t affect Exchange Online customers.
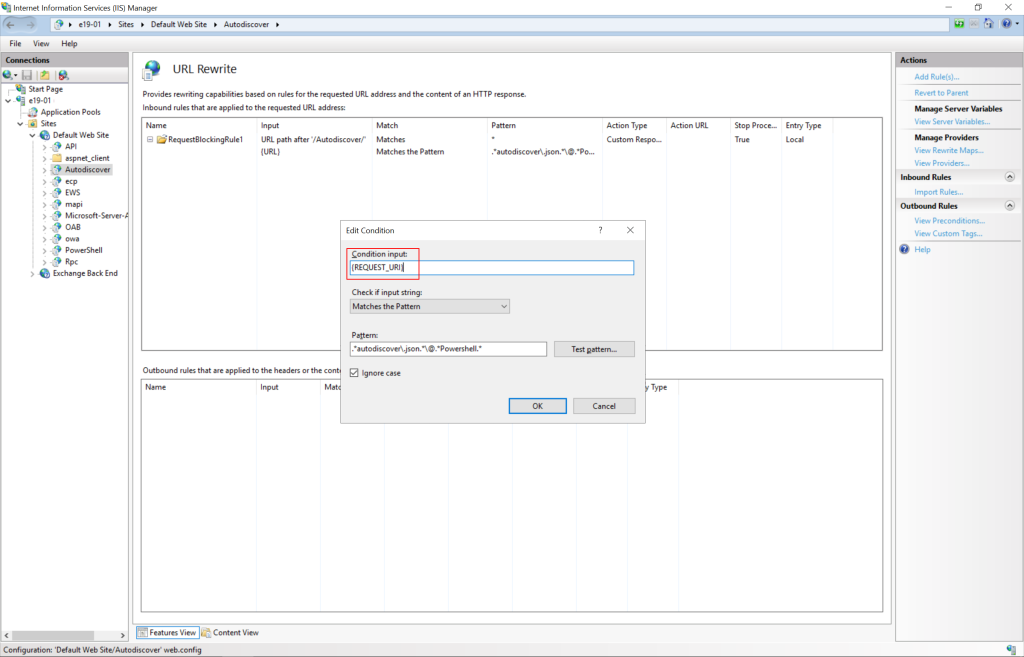
Microsoft has not detailed any detection queries for Microsoft Sentinel. Moreover, Microsoft Defender for Endpoint and Microsoft Defender Antivirus can only detect post-exploitation activities. If you’re interested, you can check out the blog post for more details about detection and mitigation techniques.



