Microsoft SharePoint Exploits Pose Risk of Document Theft
- Blog
- SharePoint
- Post

Key Takeaways:
- Cybersecurity researchers have identified two new techniques that enable hackers to steal data from Microsoft SharePoint.
- Threat actors could abuse SharePoint’s logging mechanisms and mask file downloads as access or synchronization events.
- Microsoft has categorized these exploits as moderate security issues not requiring immediate patching.
Cybersecurity researchers have discovered two new techniques that could enable hackers to steal data from Microsoft SharePoint. Microsoft SharePoint is a web-based platform used for collaboration, content management, and business process automation within organizations. It integrates with other Microsoft products like Office 365.
According to a report from Varonis Threat Labs, these methods cybercriminals could abuse these methods to trick SharePoint into logging downloads of exfiltrated files as access or synchronization events. This technique lets hackers evade detection by cloud access security and data loss prevention tools, which would typically identify the intrusion.
The first technique exploits the ‘Open in App Method’ feature within Microsoft SharePoint. This enables attackers to open SharePoint files using applications like Microsoft Word rather than a web browser. By doing so, a local copy of the document is created, and this action does not trigger a ‘FileDownloaded’ event in SharePoint’s audit logs.”
This tactic allows threat actors to download SharePoint files either using a PowerShell script or manually. “This script can be extended to map an entire SharePoint site and, using automation, download all the files to the local machine. While this method does not generate download logs, it does create access logs, which can be used to detect such activities,” Varonis explained.
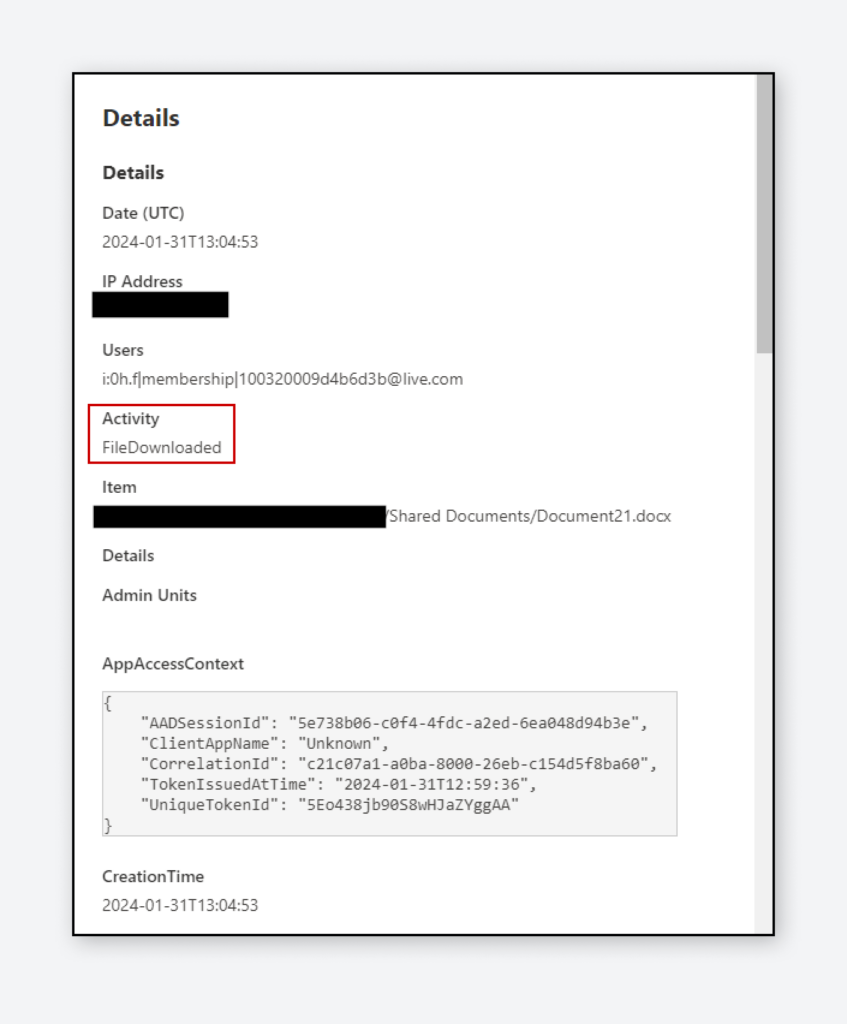
The second technique allows hackers to exploit the User-Agent string, which is utilized for managing file sync events between a computer and SharePoint. This enables SharePoint files to be replicated to users’ local machines without triggering a ‘FileSyncDownloadedFull’ log entry. Consequently, attackers can more easily hide their activities from audit logs, policy enforcement, and built-in detection mechanisms.
“By altering the browser’s User-Agent, it’s possible to download files via conventional methods, like the GUI or Microsoft Graph API, and have them appear in logs as sync event,” Varonis added.
Researchers urge vigilance against SharePoint exploits
It’s important to note that threat actors could exploit these misconfigured SharePoint permissions to extract substantial amounts of data. Varonis Threat Lab notified Microsoft of these vulnerabilities back in November 2023. However, Microsoft considers it a moderate security concern that doesn’t require immediate patching.
Meanwhile, Varonis researchers recommend that SharePoint customers thoroughly review their audit logs for any significant access from unfamiliar locations. Furthermore, security teams should closely monitor sync events to detect any unusual activities in order to prevent unauthorized data exfiltration within their organizations.


