Microsoft is working on a new project, code-named “Sonar,” to offer “malware detonation as a service,” according to ZDNet’s Mary Jo Foley. What could this mean? In this article, I will explain Advanced Persistent Threats (APTs) and how the security industry is adapting to deal with them.
Traditional Malware Detection
Way back when I was in college (when screens were mostly green), I was working in a team on a project and we shared code and documents using floppy disks. PCs were still expensive, so we relied on access to lab rooms filled with VAX/VMS terminals, Macs and PCs. I remember the shock when the PC freaked out about a disk that I was using — apparently I’d picked up something called a virus, and this was bad.
Malware detection, for the most part, has remained unchanged in decades. A programmer writes some code that does something malicious and sends it out to the world. Malware protection provides scanning services. Much like antibodies in our systems, detection only works with previously identified malware. If Symantec, McAfee, and all the others haven’t seen some malware before, then they don’t know how to identify and clean it up. Up until a few years ago, that wasn’t a big deal; there were only so many new malware releases and variants per day and the security companies could release updates — of course, someone had to be a victim first. But times have changed.
A story on CNN reported back in May that there are nearly 1 million new malware threats released every day. Malware is being released, the coders brag, and then other programmers create variants. How could any anti-malware company keep up with this?
Advanced Persistent Threats (APTs)
The days of the attacker being a teenager or malcontent in their parents’ basement are mostly over. Attacks against business are a professional and well-funded business. Nation-states and criminal organizations are funding the development of malware to breach the very best of defenses. You can put in all the scanners and firewalls that Neo or Felicity Smoak can dream up of, but there’s no defending against a user opening an email attachment that’s really a zero-day attack disguised as a PDF.
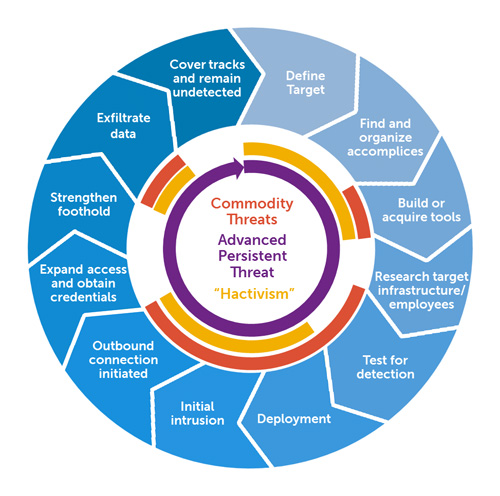
Attacks today are not just some shotgun blast out to the Great Ethernet; instead they are the result of:
A set of stealthy and continuous computer hacking processes.
That’s the definition of an advanced persistent threat (APT), according to Wikipedia. An attack by traditional malware is a quick bang — one minute you have Word documents and the next you don’t. APTs are a long-term play to counter complex defenses and extract data:
- Advanced: The attacker is well organized and funded. They have the ability to perform reconnaissance on a victim. They have access to a variety of tools, often previously unseen by security companies; these tools are developed in house or acquired on the “dark web”.
- Persistent: The attacker has an objective, instead of randomly attacking any potential victim. This objective can be blackmail, hacktivism, theft, and so on. Because they are motivated, these attackers are patient.
- Threat: The attacker is human and is a real threat to their victim. If they don’t have the tools or the time isn’t right, they will do what it takes to achieve their goal.
An APT attacker expects their intended victim to deploy security updates and modern security systems and designs. Using previously unknown zero-day threats, the author of an APT attack will open a crack to get inside the edge of a victim’s network. From there, they will use multiple tools to work their way slowly towards the crown jewels, which will be extracted without detection.
Defending Against APTs
Most organizations think that running the following will provide complete protection:
- Edge firewalls and PC firewalls
- Anti-malware on PCs, servers, email servers, and firewalls
The reality is that malware scanning only works against previously detected threats. APTs use a mixture of zero-day attacks and social engineering to counter these basic defenses. So how do you protect against a zero-day threat? The wrong answer is “deploy patches as soon as they are released”; the threat is a zero-day so, by definition, Microsoft, Apple, Oracle, Adobe, and no one else has seen the vulnerability before and there is no patch.
The security industry has understood that they could not keep up with the rate of development in the malware industry. This is why companies such as WatchGuard, Palo Alto, and others have been developing APT detection systems. The idea with these technologies is that most APTs enter via the edge network (downloads or email attachments). Normal scanning will not identify a threat and will allow the files to pass unfiltered. However, an APT blocker will be less trusting, the attachments are typically sent to virtual machines in a cloud service (why these services usually require a subscription) where the attachments are provoked into activating any possible threats:
- The files are opened & manipulated
- The guest OS experiences “time travel”
If the cloud service detects unexpected behavior then administrators are alerted and a quarantine & clean-up service can be initiated.
Project Sonar
Mary Jo Foley found an advertisement on Microsoft’s career site that describes Project Sonar:
The Sonar team is a small, fast growing team that is building a large scale, distributed security service. This service dynamically analyzes millions of potential exploit & malware samples in VMs and collects terabytes of data during that analysis every day.
Microsoft is not talking about Sonar, but Mary Jo does seem to think that Microsoft is already using Sonar in the Windows App Store and Exchange Online. There are also some mentions of an Internet Explorer “zero-day sandbox detonation chamber.”
To me, it sounds like a perfect tie-in with Azure IaaS. A possible threat is found and uploaded into one or more Azure virtual machines, nearly-instantly deployed using Azure Resource Management. A series of tests are done, and if there’s an “explosion” then malware is found, tracked down and dealt with. In theory, Microsoft could use or share this data to update Microsoft Defender.