
Last week, cybersecurity researchers warned that the North Korean hacking group “Lazarus” exploited Dell hardware drivers to deploy a Windows rootkit. The phishing campaign was discovered by security firm ESET in the Fall of 2021, and it targeted Aerospace experts and political journalists in Europe.
According to the ESET’s report, the North Korean state-backed advanced persistent threat (APT) group impersonated Amazon to send fake job offers to the victims via emails. These phishing emails contained malicious Amazon-themed documents. Lazarus managed to trick targets into opening these files and deploy malicious tools (such as droppers, loaders, fully featured HTTP(S) backdoors, and HTTP(S) uploaders) on the victim’s computer.
Specifically, the Lazarus group leveraged the BYOVD (Bring Your Own Vulnerable Driver) technique to abuse the CVE–2021–21551 vulnerability in Dell DBUtil drivers to gain administrative control of the target computer. Moreover, the threat actor exploited the vulnerability to disable Windows protections and install an advanced backdoor called Blindingcan.
Blindingcan is a remote-access trojan that lets attackers execute malicious commands, create and terminate processes as well as steal sensitive information. It can also capture screenshots from compromised systems.
“For the first time in the wild, the attackers were able to leverage CVE-2021-21551 for turning off the monitoring of all security solutions,” explained ESET researcher Peter Kálnai. “It was not just done in kernel space, but also in a robust way, using a series of little- or undocumented Windows internals. Undoubtedly this required deep research, development, and testing skills.”
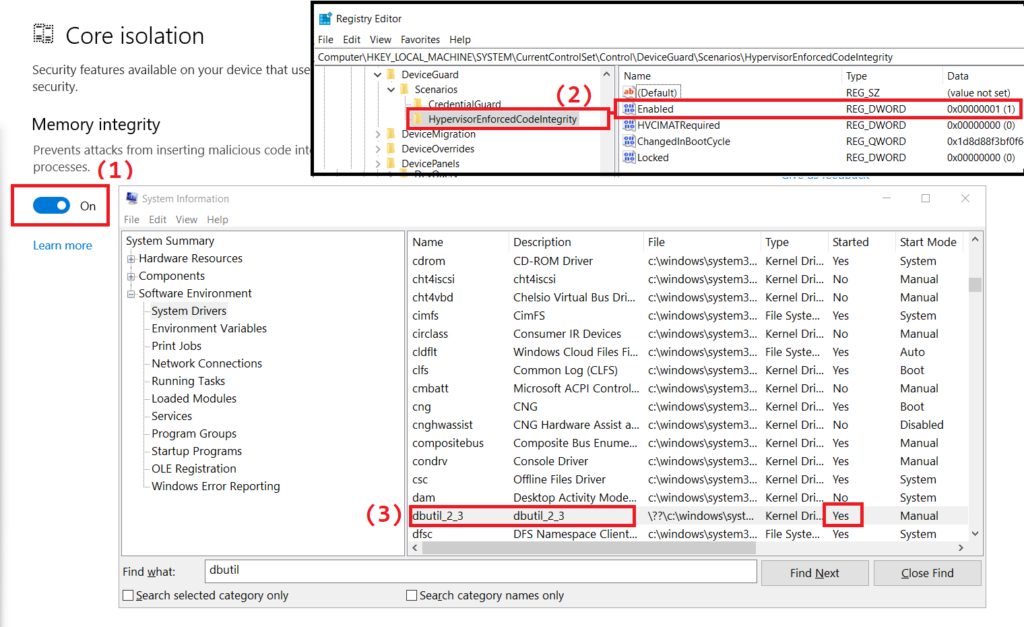
BYOVD attacks can bypass protections against vulnerable drivers in Windows
The security researchers highlighted that the BYOVD attack was quickly detected and blocked by the ESET solutions. Interestingly, Microsoft claims that users can enable memory integrity and Hypervisor-protected code integrity (HVCI) to protect their Windows 10 and 11 PCs against driver-based attacks.
However, researchers managed to load the vulnerable Dell driver on a device running
the Windows 10 Enterprise edition. It is important to note that the aforementioned security features were already enabled on the targeted Windows system.
“Vulnerable drivers have been abused by the game-cheating community and malware authors alike for a long time. It is still an ongoing battle. The vendors are trying to fix the vulnerabilities; Microsoft is trying to strengthen the operating system from the inside and third-party security vendors are trying to detect such drivers themselves. But still, the industry doesn’t have a unified way of handling the problem and there’s no guarantee that [one] even exists,” Kálnai said in an emailed statement to Ars Technica.
Microsoft has yet to clarify whether the new security features in Windows 11 will help to boost protections against BYOVD attacks. Moreover, it remains to be seen if Microsoft will provide any mitigations to block similar threats in enterprise environments.



