Join Windows 10 to Azure Active Directory During OOBE
Azure Active Directory Domain-Joined or Registered Devices?
Before you perform an Azure Active Directory (recently renamed Microsoft Entra ID) domain join, you should understand the difference between an Azure AD domain-joined device and one that is registered with Azure AD.
Domain-Joined AAD Devices
When you join a Windows 10 device to AAD, users sign in to Windows using their organizational work or school account from the lock screen, either using a password, Windows Hello for Business, or FIDO2.0 security keys.
A domain join provides single sign-on (SSO) to both cloud and on-premise resources; and optional features like conditional access, self-service password reset, and enterprise state roaming if you have an AAD plan that supports those features. Windows 10 can be joined to an AAD domain either during the out-of-box-experience (OOBE) setup phase, using the Settings app after Windows 10 has installed, via bulk enrollment, or using Windows Autopilot. Devices can be managed using Mobile Device Management (MDM) or co-managed with Microsoft Intune and System Center Configuration Manager (SCCM).
AAD Registered Devices
Azure AD registered devices are more suitable for Bring Your Own Device (BYOD) users and registration is supported on not just Windows 10 but also iOS, Android, and macOS. Users sign in with their local credentials, or in Windows 10 that might also mean a Microsoft Account (MSA). Passwords, Windows Hello, PIN, and biometrics are all supported. Devices are managed using MDM and Mobile Application Management (MAM). SSO is provided for cloud resources only and you get conditional access if devices are enrolled with Intune. There’s also conditional access via app protection policy.
Configure Azure Active Directory to Allow Users to Join Devices
Before you can join Windows 10 devices to an Azure Active Directory (AAD) domain, make sure that users are permitted to perform a domain-join operation. That’s easy to check in the Azure management portal.
- Open the Azure management portal.
- Sign in with an account that has global admin rights.
- Type azure in the search box at the top of the portal window and select Azure Active Directory from the list of services.
- In the list of options on the left, click Devices under Manage.
- Again, under Manage, click Device settings.
- Below Users may join devices to Azure AD, make sure that All is selected. If you want to restrict which users can join devices to AAD, click Selected and then click the area below it to add members.
- Click Save to confirm any changes.
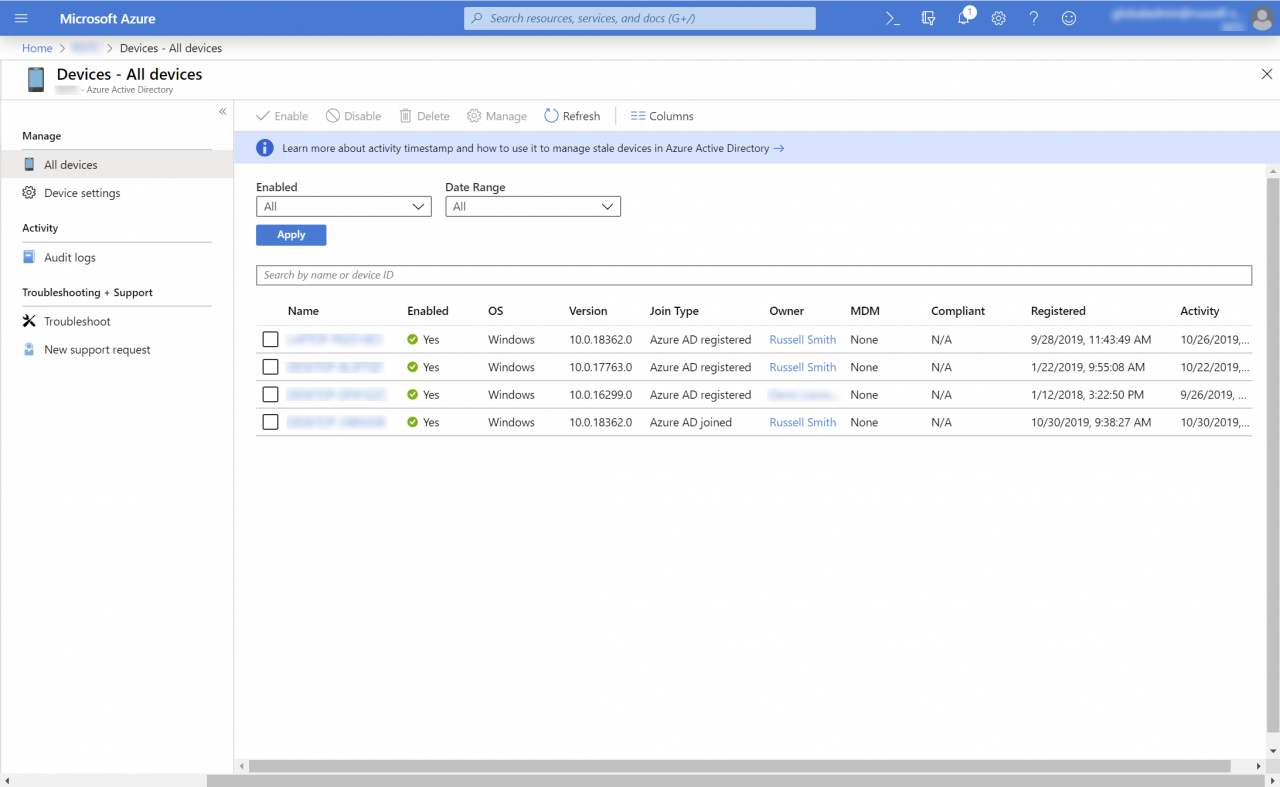
- Make a note of the number set in the Maximum number of devices per user dropdown menu.
- Now click All devices under Manage on the left.
- Check that the user adding a device to AAD hasn’t joined or registered more than the maximum number of permitted devices. If they have exceeded the maximum, the domain join operation will fail.
Join Windows 10 to an Azure AD Domain
When you start a Windows 10 Enterprise version 1903 device for the first time, and once you’ve selected your language and keyboard settings, the default option is to join Windows to an Azure Active Directory domain. While the wording is a little different – Sign in with Microsoft (Work or school account) – essentially what is being offered is to perform an AAD domain join. If you want to join the device to a Windows Server Active Directory domain, you still have that option by clicking Domain join instead in the bottom right of the Account screen.
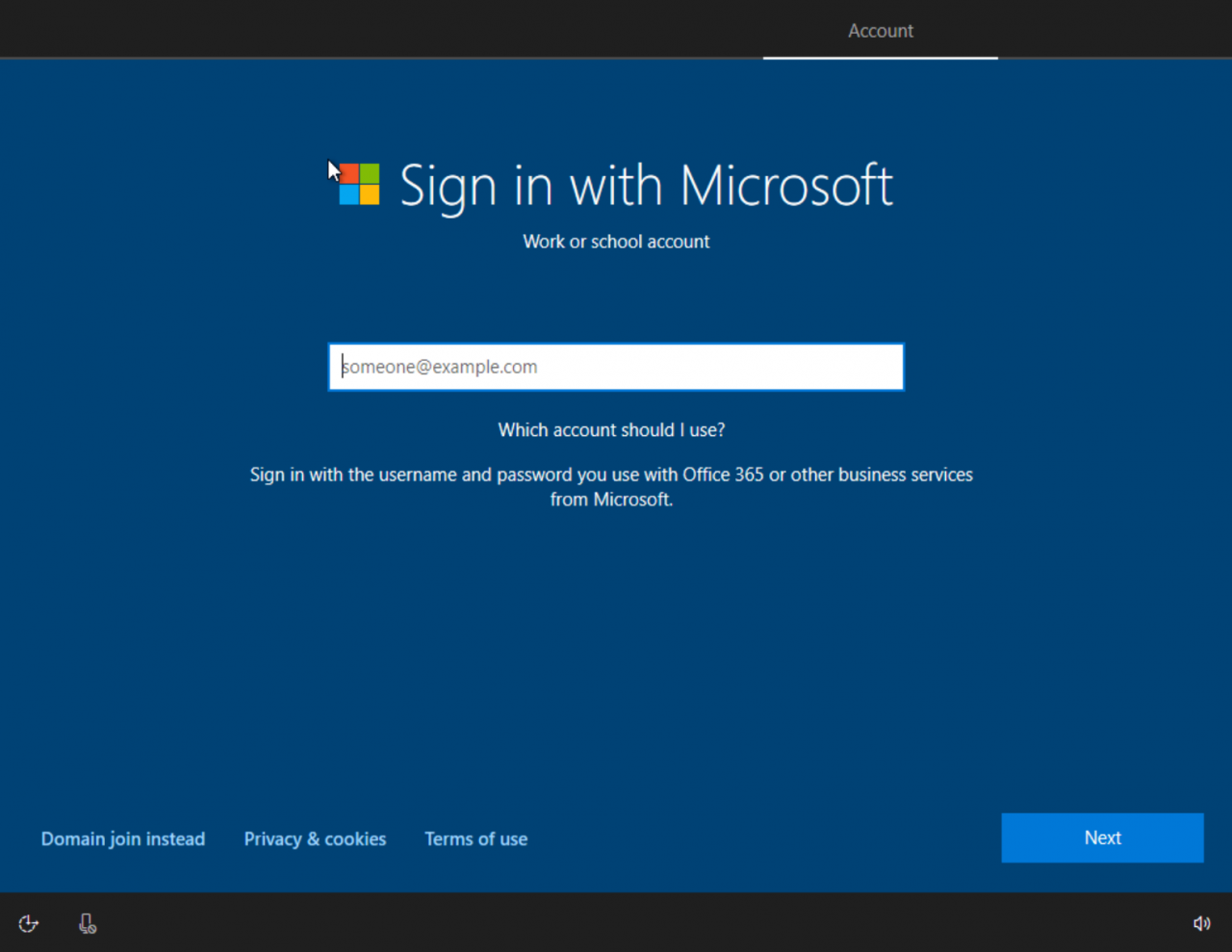
- Start the domain join process by typing the email address for the work or school AAD account that will join the device to the domain on the Sign in with Microsoft Click Next.
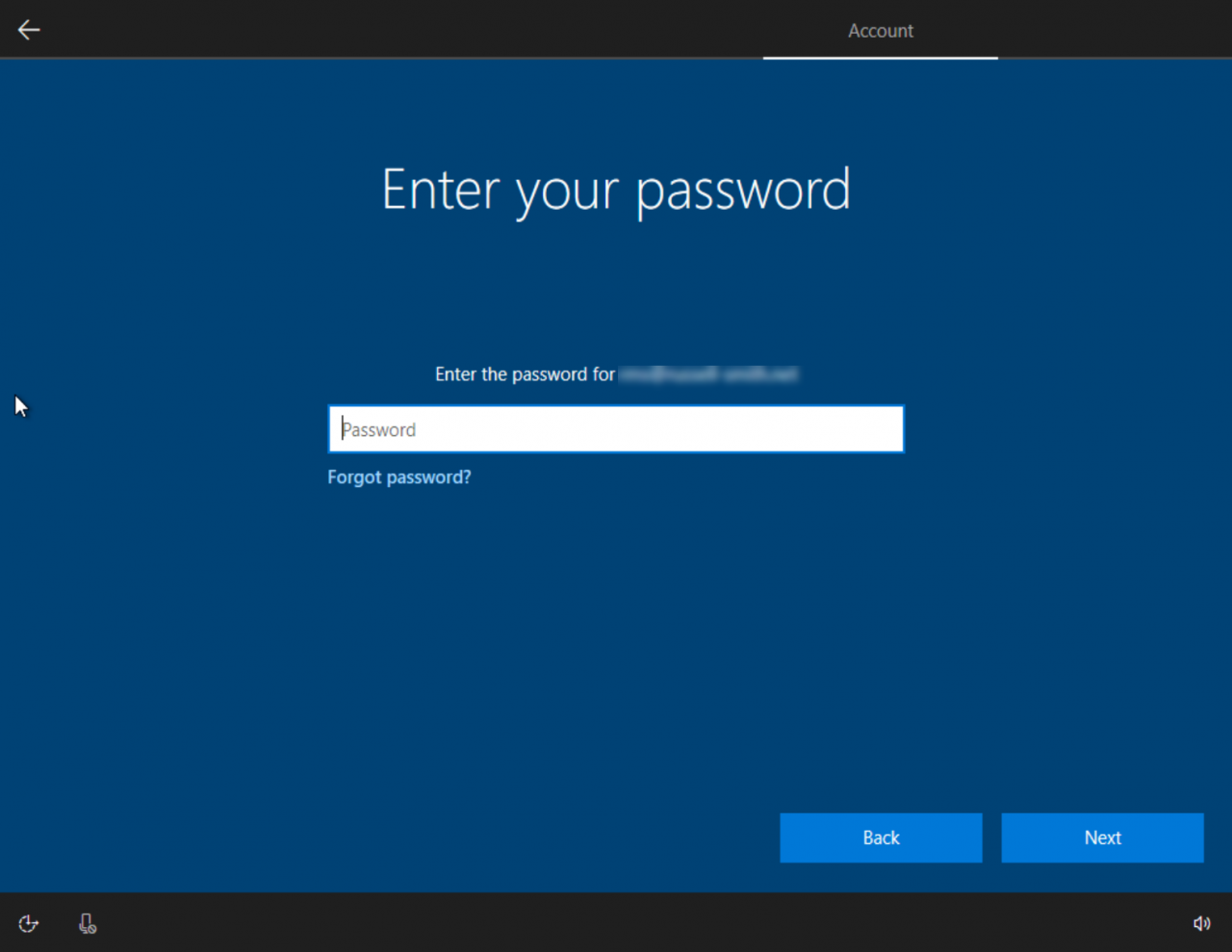
- Type the account password on the Enter your password screen and click Next. If you have multifactor authentication enabled for the account, you might need to provide a second factor at this point.
- If everything goes to plan, the rest of the process is the same as setting up Windows 10 with an MSA or local account.
Once your desktop environment has been configured, you might need to set up a PIN for Windows Hello for Business if your organization requires it. The process is a little convoluted in that it also asks you to set up the Microsoft Authenticator app before you can enter your new PIN. Alternatively, you can use phone verification instead of the Authenticator app.
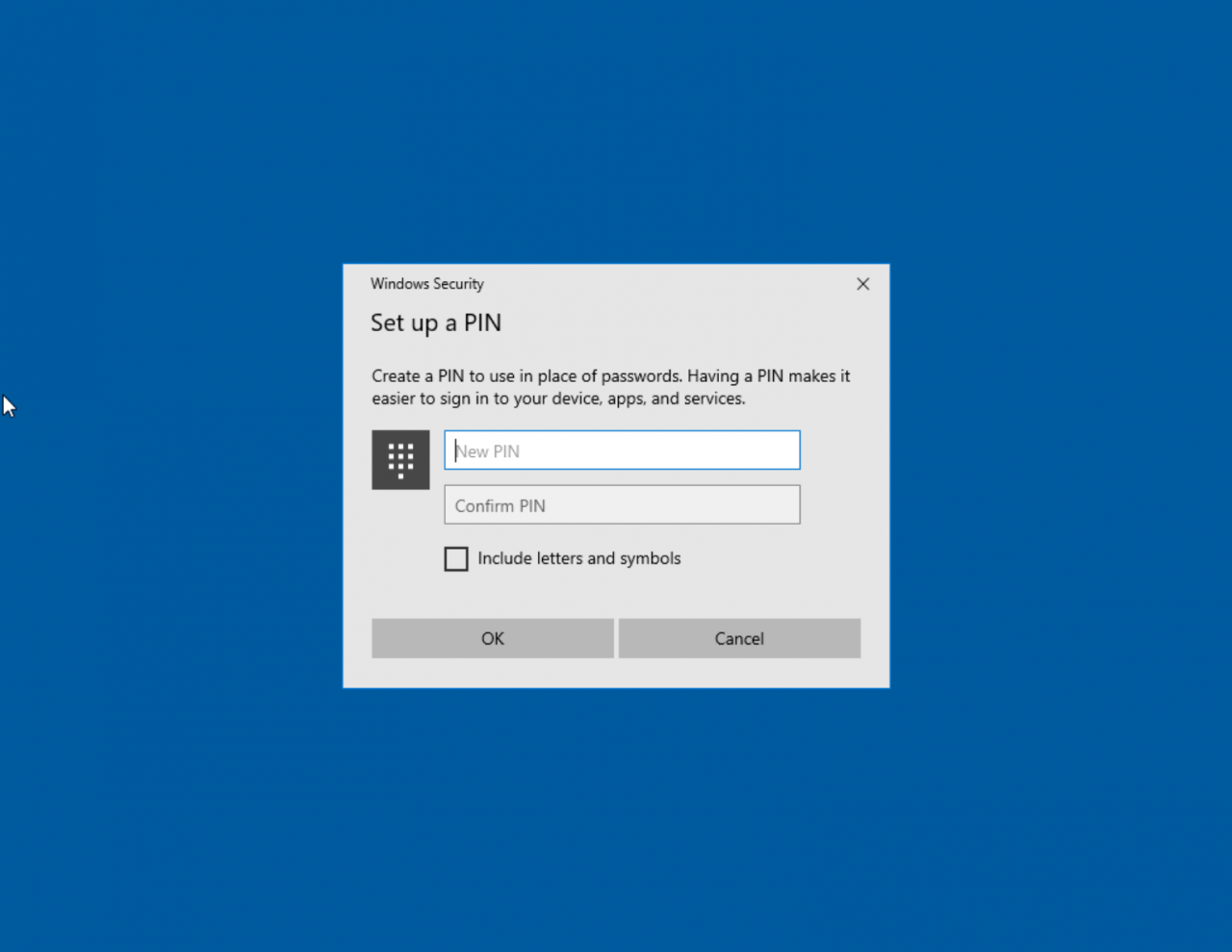
Even if you already have the account added to the Authenticator app on your phone, you’ll need to step through the process of adding the account to the app again. Once you’re done, all you need to do is enter and confirm a new PIN to sign in to the device without a password.
Managing the Local Administrators Group
The account you used to join the device to AAD automatically becomes a local administrator. That’s not an ideal situation but you can prevent this by using Windows Autopilot, which has an option to prevent the user performing the domain join becoming a local administrator; or use bulk enrollment with the help of a provisioning package. For more information on managing the local administrators group on Azure AD joined devices, check out How to manage the local administrators group on Azure AD joined devices on Microsoft’s website.




