This two-part article explains two security features in Windows Server 2012 (WS2012 – and later) Hyper-V networking, DHCP Guard and Router Guard. These features allow Hyper-V admins to prevent virtual machine admins from enabling unwanted network services within the guest operating system. The second part of this article will outline how to deploy these two security features.
The Need for Network Security Services
My first job as a solo contractor was as an administrator in a security software research and development company. One morning a number of developers complained that they could not access the servers. I stayed calm and began performing the usual command line diagnostics on one of their PCs. That’s when I noticed that they had a DHCP-assigned IP address that was not valid on the company network. It wasn’t an address from our DHCP server however. Someone had set up a rogue DHCP server. With the help of a network administrator, we eventually tracked down the floor port that the rogue DHCP server was plugged into. A researcher had fired up a DHCP server on one of their lab machines on the company network.
DHCP clients are pretty dumb. They broadcast, receive, and IP from the first respondent. The researcher incorrectly assumed that his lab DHCP server couldn’t operate on the network because it offered IP addresses for a different subnet. He made an honest and uninformed mistake. Unfortunately, everyone in his VLAN, he should not have run lab machines on an office VLAN, was a potential victim of his accidental denial of service attack.
Anyone with administrator rights on a machine can offer network services. Some of these servers are found and offered using a broadcast. That means issues can easily arise. Perhaps there is an accident as with the story about the researcher, or a disgruntled employee with local admin rights in a virtual machine who decides to cause some damage. Virtualization has led to “VM sprawl”, (which we can control with cloud-based cross-charging or quotas), and that means a lot more employees or customers have local admin rights in virtual machines. There is an increased risk of issues so we need a way to control them.
DHCP Guard in Windows Server 2012 (and later)
The first of the two new security features added to Hyper-V in Windows Server 2012 (WS2012) is DHCP Guard. Here is a quick primer on how DHCP works.
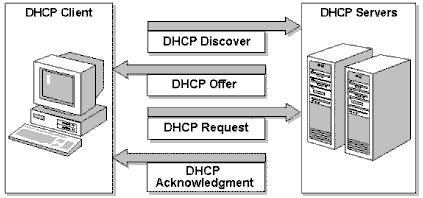
A client starts up and realizes that it is configured to use a dynamic IP address instead of a statically assigned address. The client will broadcast a DHCP discover. Any DHCP server that can receive this broadcast (directly on the VLAN or via network helpers) can respond with an offer. This is where a rogue DHCP server can interfere with the legitimate process. The client will (hopefully) receive offers and will send a DHCP request to the first DHCP server to send a DHCP offer.
How DHCP works (Source: Microsoft)
Hyper-V administrators typically know which machines are legitimate DHCP servers on their network. All other machines should not be DHCP servers. Hyper-V includes a feature called DHCP Guard. When enabled in the advanced virtual NIC settings, DHCP Guard will prevent that virtual NIC from sending a DHCP offer. The guest OS admin can perform as many DHCP configurations they want but the DHCP Guard prevents the virtual machine from being a DHCP server.
Router Guard in Windows Server 2012 (and later)
If you’ve sat through Microsoft certification or training, you know that an operating system can be configured as a router. What you may not know is that a router can offer its routing services to the network much like a DHCP server can. That means that the administrator of a computer, including the guest OS administrator of a virtual machine, can set up a rogue router on a network (physical or virtual) and start re-routing packets to a rogue location or a black hole.
Router Guard was also added to WS2012 Hyper-V to prevent any accidental or rogue guest OS routers from offering their services on the network. Just like with DHCP Guard, the guest OS admin can do what they want within the confines of their virtual machine, but when Router Guard is enabled, they cannot interfere with normal network operations. This is done by blocking the following packets:
- ICMPv4 Type 5 (Redirect message)
- ICMPv4 Type 9 (Router Advertisement)
- ICMPv6 Type 134 (Router Advertisement)
- ICMPv6 Type 137 (Redirect message)
Alterative Scenario
Microsoft’s Ben Armstrong has posted a scenario that had not occurred to me previously. You might have a virtual machine that legitimately runs DHCP or routing services on your network. The virtual machine might have multiple virtual networks connected to different virtual networks, which in turn might connect to physical networks. You can enable DHCP Guard or Router Guard on one or more NICs to control which networks the virtual machine will offer services on. This might be to limit services for long term purposes, or this might be to temporarily disable services while you troubleshoot an issue.
The next part of this article will cover the deployment of DHCP Guard and Router Guard.