How to Audit and Test Windows 10 Controlled Folder Access
Ransomware has rarely been out of the headlines over the past few years and it is the most prevalent threat in 2020. WannaCry and NotPetya may be distant memories but the vulnerabilities they rely on are still exploited. And more recently, malware in the RobbinHood family has been used to target large organizations. First by getting access to networks using brute force attacks against RDP and then introducing a vulnerable kernel driver that lets hackers take full control of systems.
Microsoft Defender vs ransomware
Controlled Folder Access (CFA) was added to Windows 10 in the Fall Creators Update to protect users’ files in the event of a ransomware attack. Windows Defender Exploit Guard replaced the Enhanced Mitigation Experience Toolkit (EMET) in Windows 10. CFA is part of Exploit Guard and it helps users and organizations protect folders, such as Documents, from malicious apps.
CFA is disabled by default. However, users can enable it and receive better protection with the default settings. The protected folders list includes the Documents, Videos, Music, Favorites, and Pictures folders for all users. You can also add your own folders to the list. Network shares can also be protected, although the use of wildcards is not supported.
For more information about how to enable CFA, check out Controlled Folder Access in Windows 10 FCU on Petri.
Enable Controlled Folder Access in audit mode
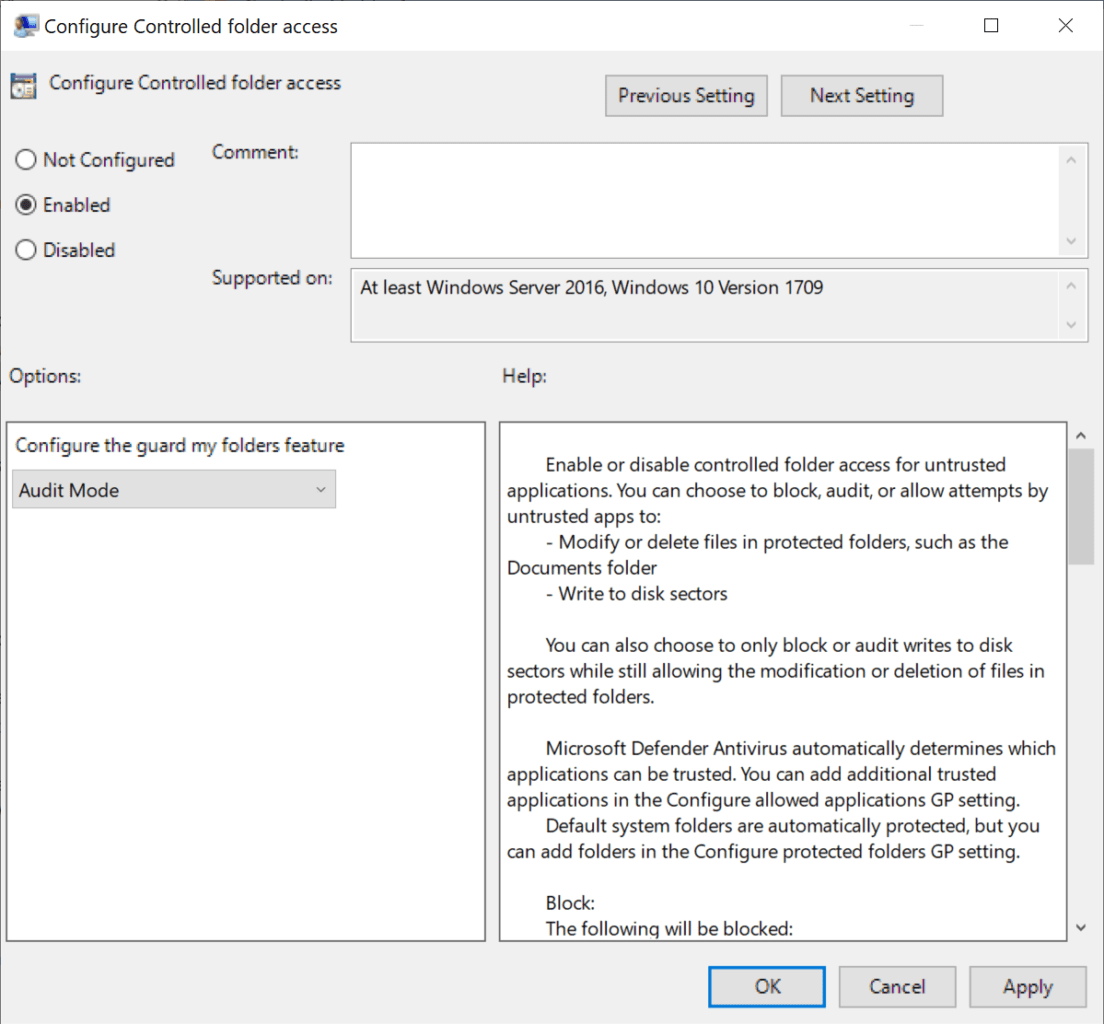
Before you enable CFA in your organization, you can set it up in audit mode to assess the impact on endpoints. Audit mode can’t be enabled in the Windows 10 Settings app. You need to use PowerShell or Group Policy. To enable CFA in audit mode using PowerShell, run the following command in an elevated PowerShell window:
Set-MpPreference -EnableControlledFolderAccess AuditMode
When audit mode is enabled, check the Windows Defender/Operational folder in Event Viewer for the following events:
- 5007 – Event when settings are changed
- 1124 – Audit controlled folder access event
- 1123 – Blocked controlled folder access event
Group Policy gives you a bit more flexibility because there are two different types of audit mode. Audit Mode can be enabled using Group Policy, which logs events if an untrusted app tries to make changes to files in a protected folder. Additionally, Audit disk modification only can be set to log only attempts to write to protected disk sectors.
You can enable Controlled Folder Access in audit more or block mode under Windows components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Configure Controlled folder access in Group Policy. If you don’t know how to work with Group Policy, read How to Create and Link a Group Policy Object in Active Directory on Petri.
Testing Controlled Folder Access
Microsoft provides a sample ransomware file that you can use to test CFA. You can access the file here. You’ll need to sign in to Microsoft to download the file and bypass any SmartScreen prompts that might prevent you from downloading the file in your browser.
Create a folder, C:\Demo, and add a text file to the demo folder. The sample ransomware needs something to encrypt. Add the C:\Demo folder to the CFA protected list. The quickest way is using the following PowerShell command:
Set-MpPreference -ControlledFolderAccessProtectedFolders C:\Demo\
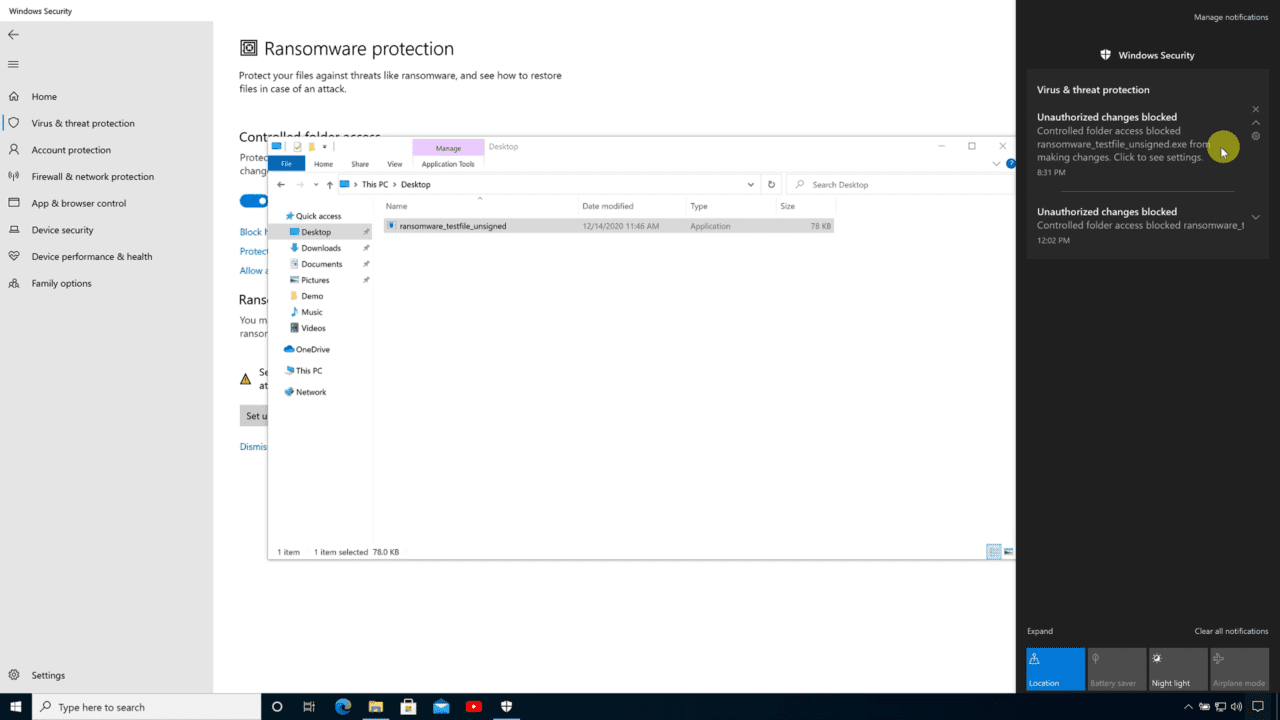
Now run the ransomware sample (ransomware_testfile_unsigned.exe) you downloaded from Microsoft’s website. If CFA is working, within a few seconds, you should see a notification in the Action Center telling you that unauthorized changes were blocked.
Now let’s see what happens if CFA is disabled. To turn off CFA, run the following command in an elevated PowerShell prompt:
Set-MpPreference -EnableControlledFolderAccess Disabled
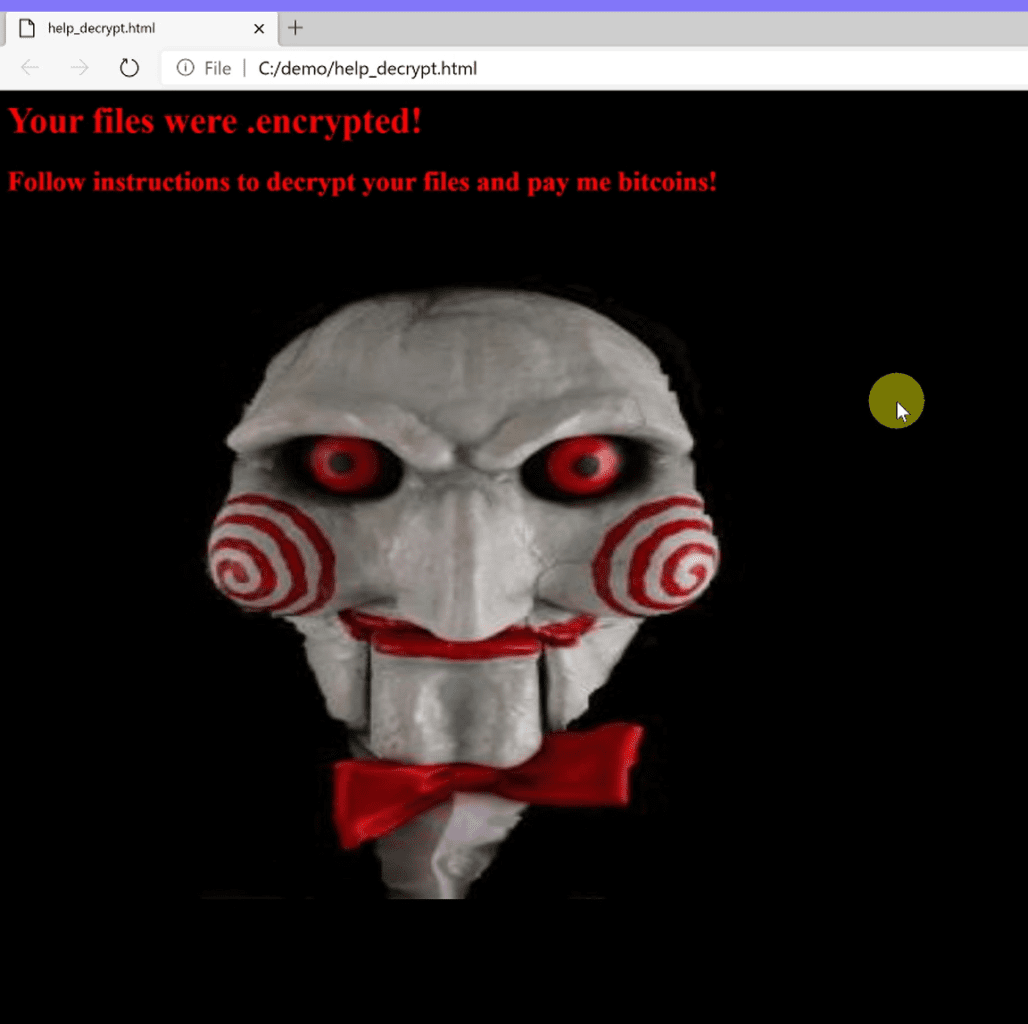
Run the ransomware (ransomware_testfile_unsigned.exe) again. This time you should see a warning open in a browser window telling you that your files have been encrypted. Check the contents of the C:\Demo folder and you will see your file was encrypted.
If you want to reenable CFA and run the malware again, you’ll need to run the following commands in an elevated PowerShell prompt to reset Attack Surface Reduction rules:
Add-MpPreference -AttackSurfaceReductionRules_Ids BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550 -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids D4F940AB-401B-4EfC-AADC-AD5F3C50688A -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids 3B576869-A4EC-4529-8536-B80A7769E899 -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids 75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84 -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids D3E037E1-3EB8-44C8-A917-57927947596D -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids D1E49AAC-8F56-4280-B9BA-993A6D77406C -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids B2B3F03D-6A65-4F7B-A9C7-1C7EF74A9BA4 -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids C1DB55AB-C21A-4637-BB3F-A12568109D35 -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids 01443614-CD74-433A-B99E-2ECDC07BFC25 -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids 26190899-1602-49E8-8B27-EB1D0A1CE869 -AttackSurfaceReductionRules_Actions Disabled Add-MpPreference -AttackSurfaceReductionRules_Ids 7674BA52-37EB-4A4F-A9A1-F0F9A1619A2C -AttackSurfaceReductionRules_Actions Disabled
Controlled Folder Access as part of a defense in depth security strategy
Controlled Folder Access can’t protect Windows against ransomware in all situations. If a hacker gets elevated privileges on a system, by exploiting an unpatched vulnerability for example, or tricks a user that has admin rights, then it might be possible to disable CFA. But on systems that are properly secured, CFA provides a defense in depth protection against ransomware.