Grant DNSAdmins the Right to View DNS Event Log Entries Remotely on Windows Server 2008 R2
Overview
This is an issue we’ve struggled with in the past day or so. An organization running Windows Server 2008 R2 is delegating control of their DNS servers to specific people, and in order to do so, they added these users to the DNSAdmins built-in group in Active Directory. However, since these users are not members of any administrative groups, while they can view the DNS Event Logs and manage them locally, on the DNS server(s), they cannot do so remotely from another Windows Server 2008 R2 or Windows 7 management workstation.
The Problem: Access Denied when Viewing Event Logs Remotely
To demonstrate this in our lab environment, we created a user called DNSManager, and added him to the DNSAdmins group. Once the user logs on to their management workstation and opens Event Viewer, they connect to a remote computer.
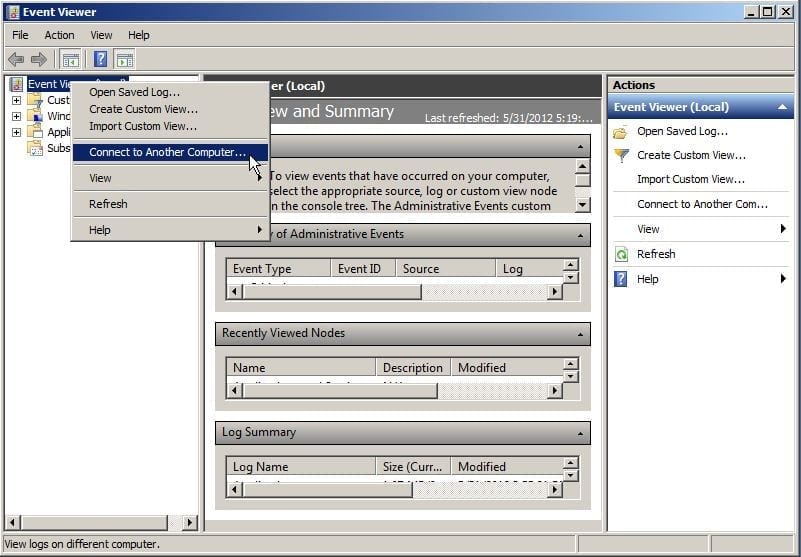
Figure 1: Connecting to a Remote Computer
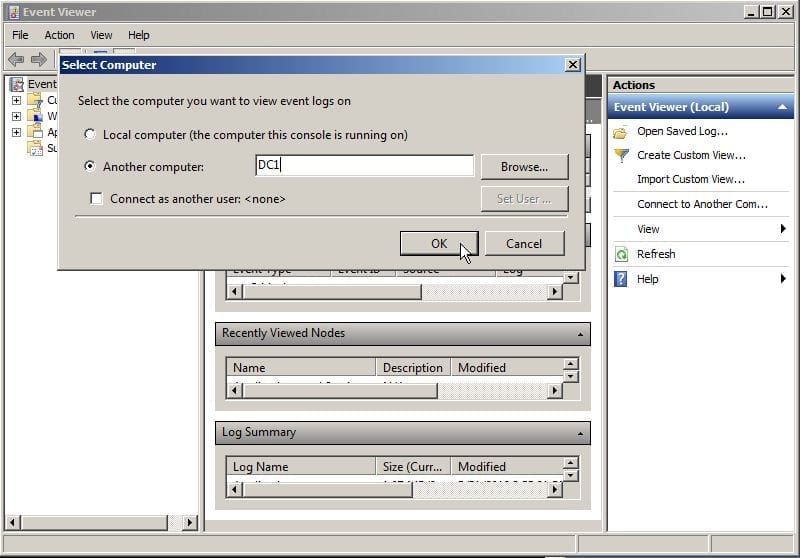
Figure 2: Select Computer to View Event Logs on
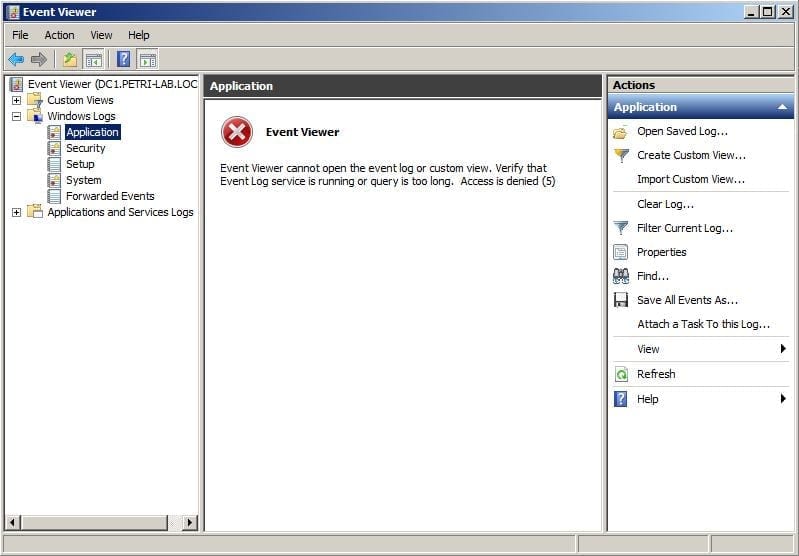
Figure 3: Access Denied Error Message when Viewing Event Logs Remotely
The Solution: Granting DNSAdmins to the Event Log Readers Group
This can be easily fixed by adding these users (or group of users) to the “Event Log Readers” built-in group on the servers that you need to have remote access to.
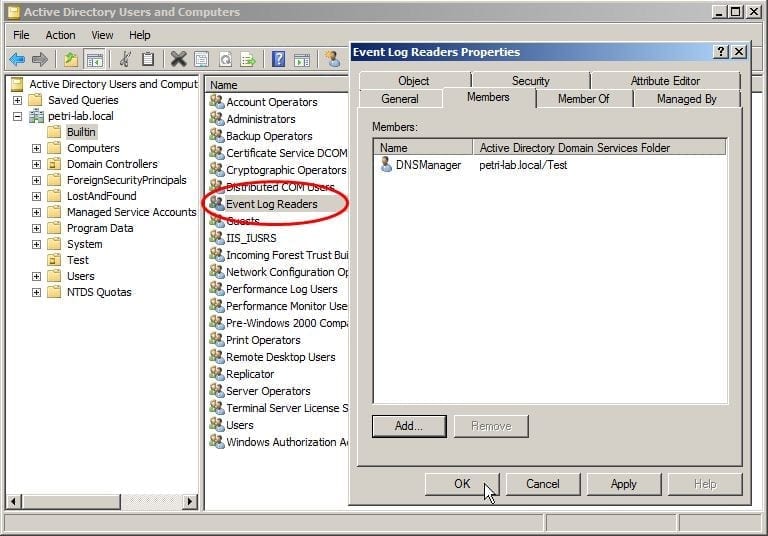
Figure 4: Adding DNSAdmins to the Event Log Readers Group
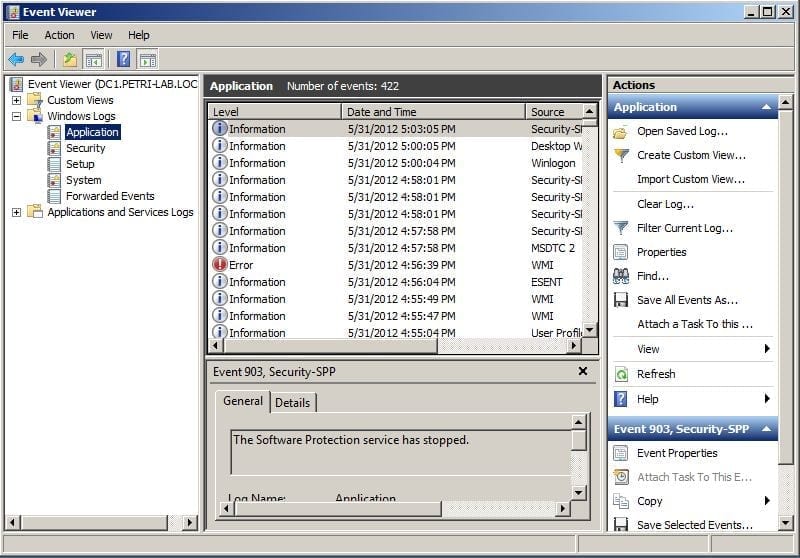
Figure 5: Access Granted to DNSAdmins
The Problem: Access Denied to DNS Event Logs
However, while this trick works for most Event Logs, it does NOT work for the DNS Event Log, as can be seen from this screenshot below.
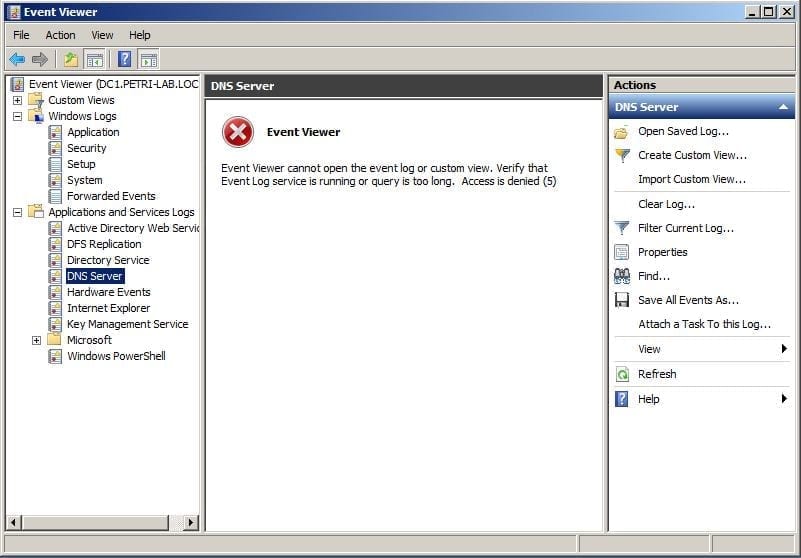
Figure 6: Access Denied error when Viewing DNS Event Logs
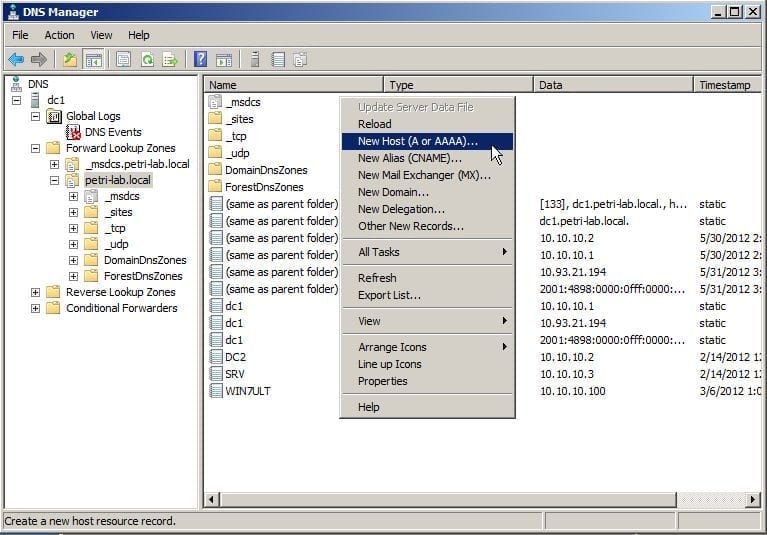
Figure 7: DNS Management Console works find
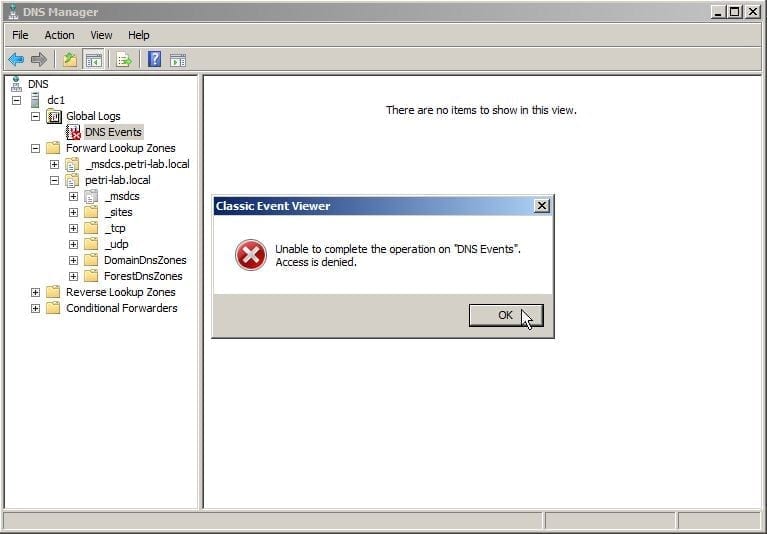
Figure 8: Unable to Access DNS Event Logs
The Solution: Granting Remote Access to DNS Event Logs
The fix lies in a somewhat complex Microsoft knowledgebase: How to set event log security locally or by using Group Policy in Windows Server 2003
And also in this great blog post: Giving Non Administrators permission to read Event Logs Windows 2003 and Windows 2008 – Jane Lewis’s Weblog
But the trick is that in Windows Server 2008 R2, the procedure is a lot simpler. Here are the steps:
-
- Open Command Prompt with elevated permissions (Run as Administrator), and run the following command:
wevtutil gl "DNS Server" > C:\Temp\DNS_Server.txt
Note: Change the path to fit your needs.
By the way, if you need to perform the same trick on other custom or application logs, you can find out the name of the log by running the following command and examining the resulting text file for the exact name syntax:
wevtutil el > C:\Temp\All_Logs.txt
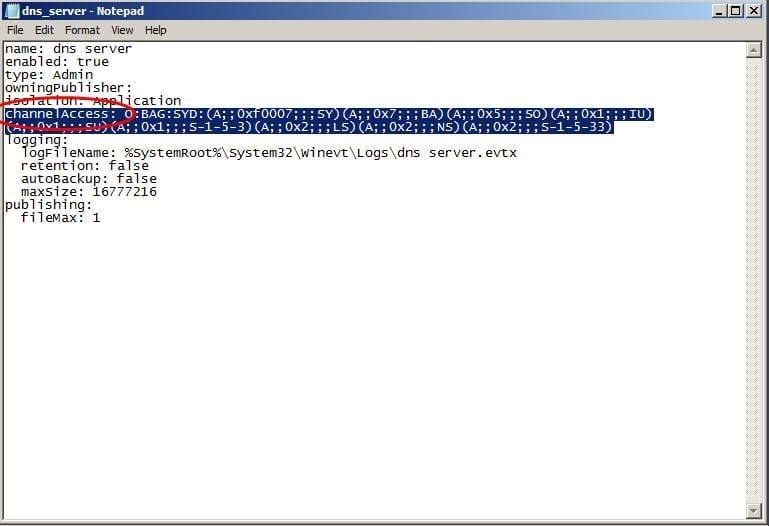
- Next open the text file from the above path, and look for the channelAccess: entry.
Figure 9: ChannelAccess entry - Now we need to find the SID of the DNSAdmins group. To do so, if the logged on user is a member of that group, you can find the SID by typing the following command (assuming this is Windows Server 2008 R2 or Windows 7):
whoami /groups | find /i "dnsadmins"
The result should look something like this:
PETRI-LAB\DnsAdmins Alias S-1-5-21-3903327414-3371247034-3746192915-1102 Mandatory group, Enabled by default, Enabled group
Naturally, the domain name and SID will differ, but you get the point…
You can also use other tools such as PSGetsid from Sysinternals.
Copy the SID, we’ll need it in a moment.
- Going back to the text file, append the following text string to that long line:
(A;;0x1;;;XXX)
Where XXX is the SID you’ve copied from above.
In this case, I will append the following line:
(A;;0x1;;;S-1-5-21-3903327414-3371247034-3746192915-1102)
Figure 10: Adding Your SID - Next, copy the entire text from the O:BAG… part till the end of the line (including your recent addition):
O:BAG:SYD:(A;;0xf0007;;;SY)(A;;0x7;;;BA)(A;;0x5;;;SO)(A;;0x1;;;IU)(A;;0x1;;;SU)(A;;0x1;;;S-1-5-3)(A;;0x2;;;LS)(A;;0x2;;;NS)(A;;0x2;;;S-1-5-33)(A;;0x1;;;S-1-5-21-3903327414-3371247034-3746192915-1102)
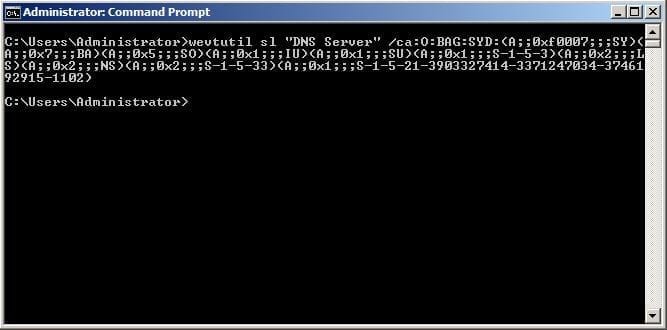
- And finally, run the following command in the Command Prompt, pasting the above string just after the /ca: parameter:
wevtutil sl "DNS Server" /ca:O:BAG:SYD:(A;;0xf0007;;;SY)(A;;0x7;;;BA)(A;;0x5;;;SO)(A;;0x1;;;IU)(A;;0x1;;;SU)(A;;0x1;;;S-1-5-3)(A;;0x2;;;LS)(A;;0x2;;;NS)(A;;0x2;;;S-1-5-33)(A;;0x1;;;S-1-5-21-3903327414-3371247034-3746192915-1102)
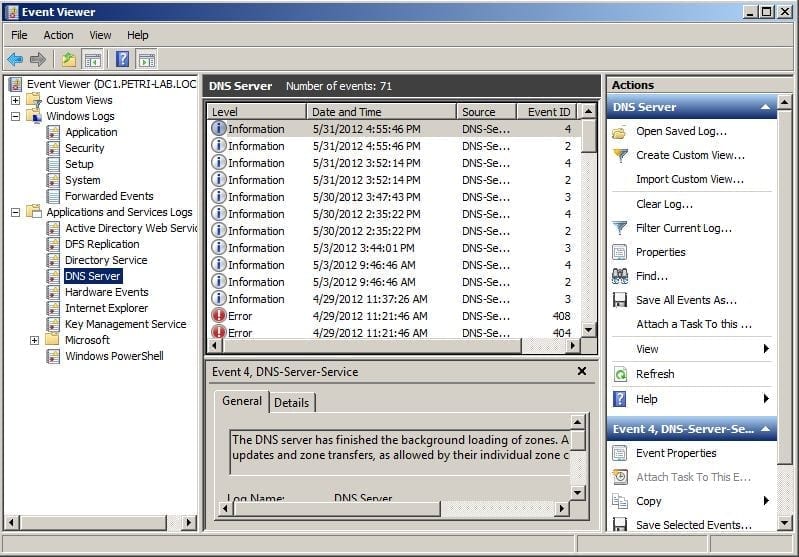
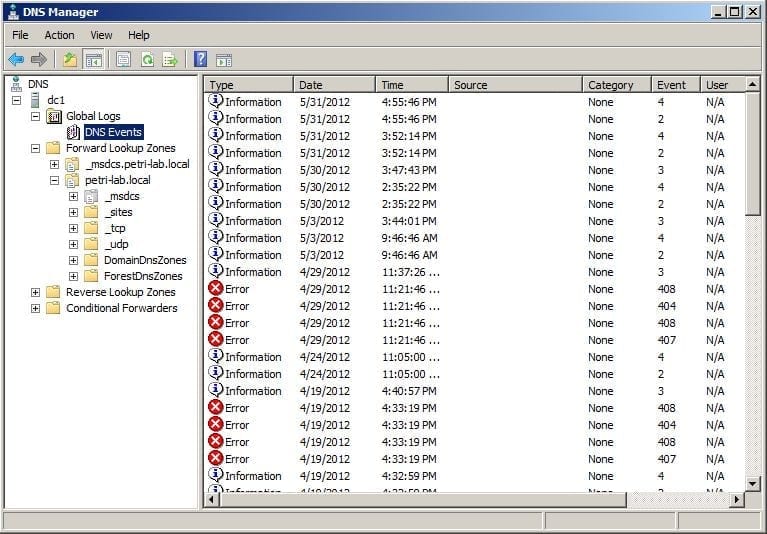
Figure 11: Run the command You can now close the text file, we don’t need it anymore. No need to save it.Going back to the management workstation, open Event Viewer or open DNS management console as the DNSManager user, and behold, you can now view the DNS Event Logs:
Figure 12: Problem solved, the DNS Event Logs show up Figure 13: Problem solved, the DNS Event Logs show up
- Open Command Prompt with elevated permissions (Run as Administrator), and run the following command:
Summary
In our next blog post, we will show you how to add these settings to Group Policy in order to configure them for multiple servers.