Getting Started with Azure Adaptive Network Hardening
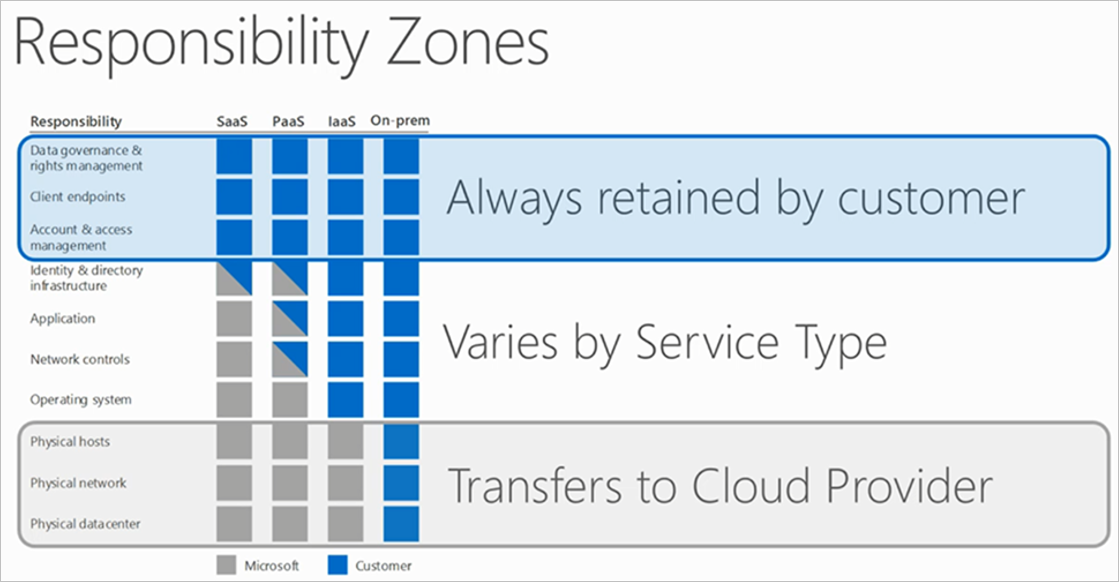
Microsoft is continuously expanding Azure on a daily basis; this expansion also includes security features. There is some debate about who owns the responsibility of securing assets in the cloud, regardless of who owns the platform. Microsoft identifies who is responsible for what as the customer progresses through their platform displayed in their shared responsibility model (seen below). Securing and configuring your virtual machines falls under the ownership of the customer. In this article, we’ll look at a new method for securing virtual machines with Microsoft’s preview release of Adaptive Network Hardening.
What is it?
Adaptive Network Hardening is a feature found in the Azure Security Center. You can find it under the Networking blade once you’ve activated Azure Security Center.
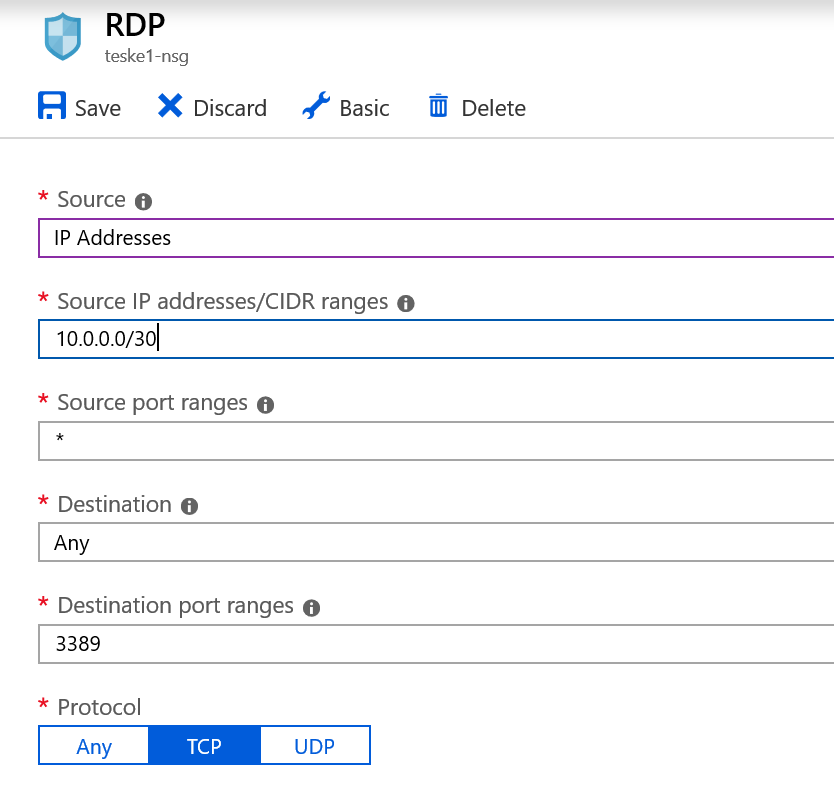
This feature is like an add-on to your Network Security Group. At a fundamental level, a Network Security Group can have rules applied to it granting or denying network traffic or access. Adaptive Network Hardening provides a more granular recommendation based on the traffic it has analyzed. For instance, you have a virtual machine in Azure you use as a jump box to administer the other Azure assets. You access this jump box through remote desktop protocol on port 3389. You created a Network Security Group rule which allows this traffic from a 10.0.0.0/24 subnet. Adaptive Network Hardening will analyze this traffic (machine learning) and make recommendations to reduce the scope of the subnet. It does not apply the recommendations for you. It will provide instructions under Remediation Steps found under Adaptive Network Hardening.
Activating Azure Security Center
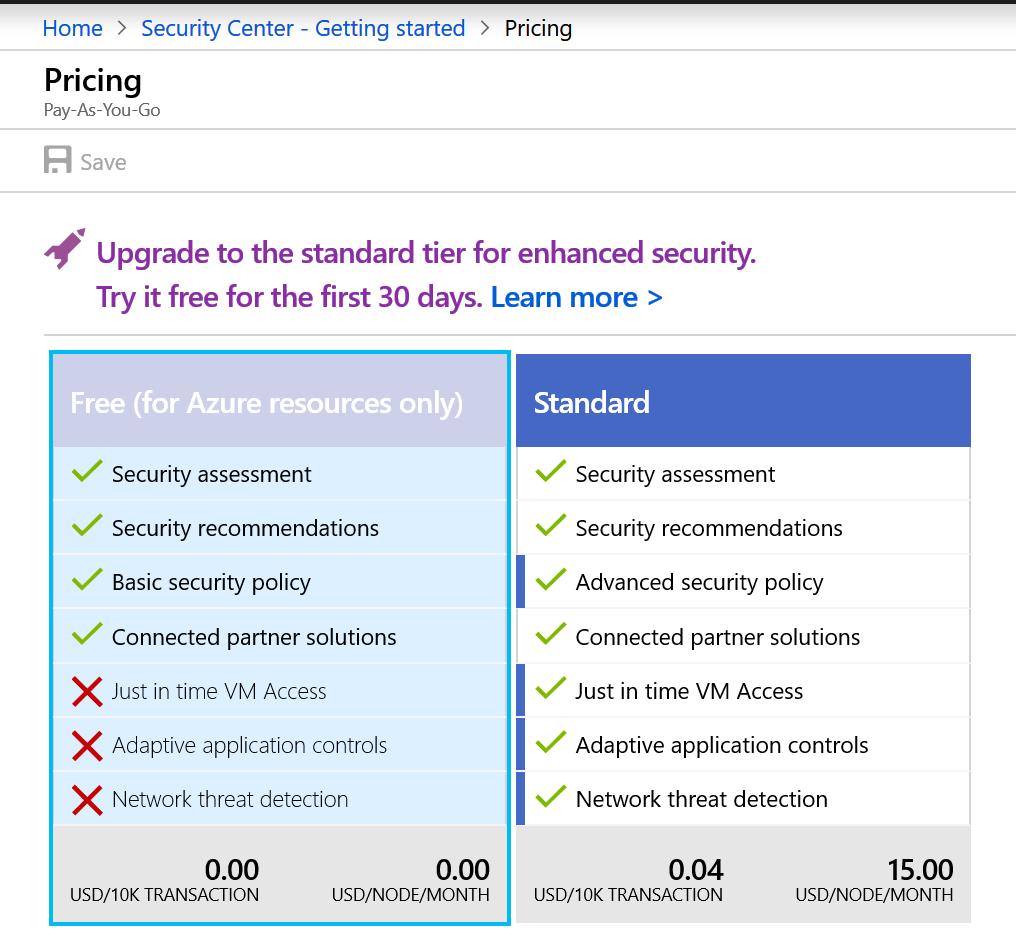
Adaptive Network Hardening is pretty straight forward. It does require that you have virtual machines to harden. The first thing you will have to do is activate the Azure Security Center. The Security Center has 2 pricing tiers, free and Standard. You get a free 30-day trial of the Standard plan. The features available for each tier are listed below:
Working with Adaptive Network Hardening
Once you’ve activated your plan, the Azure Security Center features will become available allowing you to explore the features and services provided at your pricing tier. Let’s take a quick look at Adaptive Network Hardening:
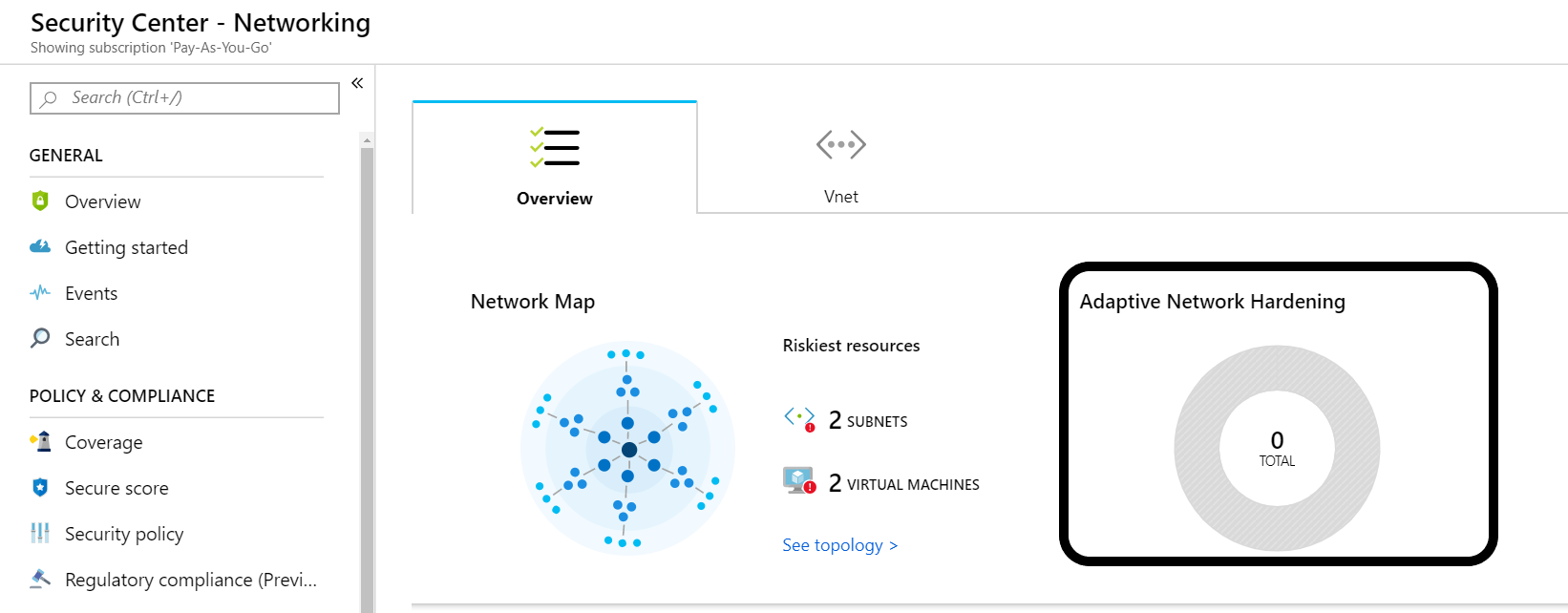
- Log into your Azure Portal
- Select Security Center
- Select Networking
- Click on the center panel labeled Adaptive Network Hardening
- The Adaptive Network Hardening page has several areas of information:
- Description: provides information on what it has found that has increased your attack surface.
- General Information: Displays the recommendation score and user and cost impact (low, moderate, high).
- Azure Security Center analyzes your resources. If a vulnerability is discovered, it will provide a recommendation and guidance to correct.
- Threats: What are the possible threats/risks/vulnerabilities if not corrected.
- Remediation steps: Generalized steps to harden the Network Security Group traffic rules.
- Resources:
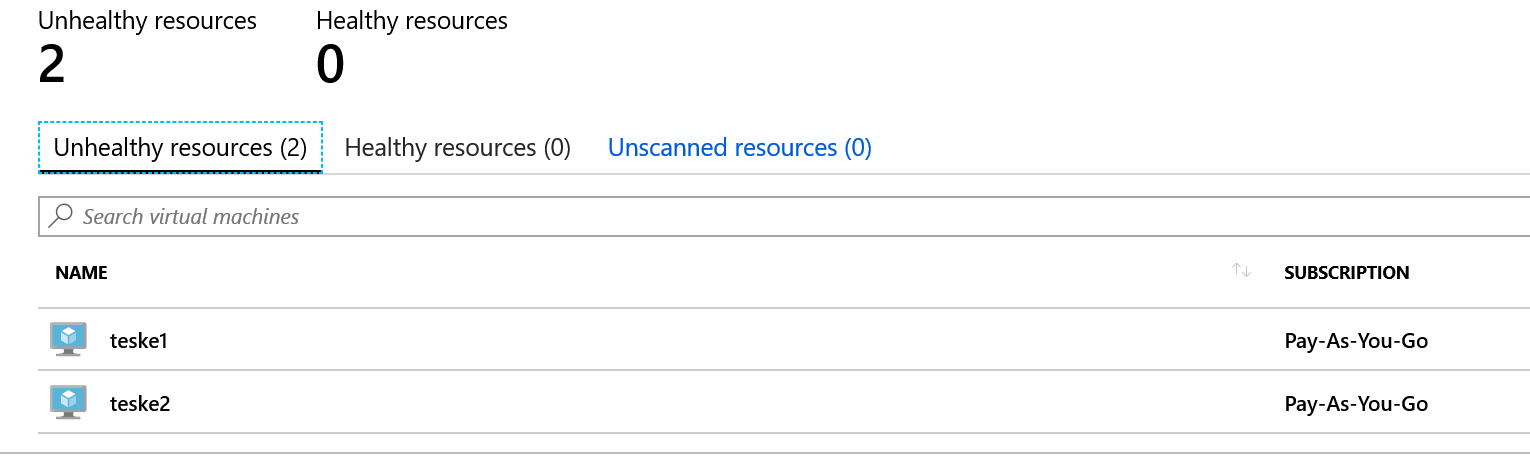
- Unhealthy Resources: The Adaptive Network Hardening algorithm has detected issues and has generated alerts and recommendations to remediate.
- Healthy Resources: VMs do not have any alerts or recommendations
- Unscanned Resources: resources may be flagged as unscanned due to the following:
- Classic VMs
- Not enough data has been collected. Security Center requires at least 30 days of traffic to be analyzed.
- VM is not protected under the Azure Security Center standard tier.
Viewing and Applying Recommendations
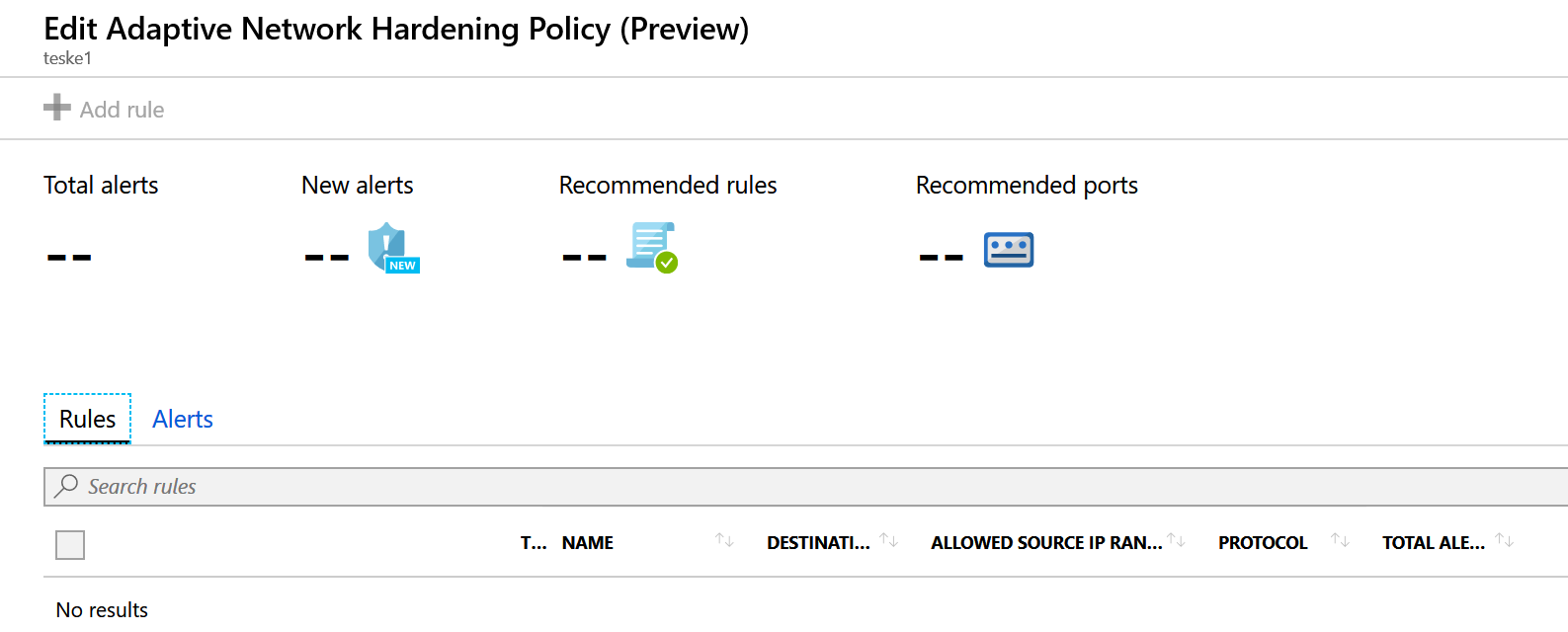
You can select any of the virtual machines in any of the categories to view the Edit Adaptive Network Hardening Policy page. This page will display any alerts and recommendations it has discovered while enabled. You also have the ability to add rules (similar to a Network Security Group) here as well (see below). Azure Security Center needs to collect data for more than 30 days on your resources in order to provide more granular recommendations as it analyzes the traffic to and from these resources. As a reminder, Microsoft does not apply the recommended rules or adjusts to the recommended ports. They place the responsibility of hardening the network squarely on the customer’s shoulders.
Conclusion
I hope this gives you a better insight into this new security feature. Unfortunately, I just started my Azure Security Center subscription so Azure wasn’t able to gather enough data (needs 30 days) to provide any solid recommendations other than securing my RDP connections. I hope to come back and update this article with some better graphics and data. However, the concept of using machine learning to improve your virtual machines is a great idea at this level. Adaptive Network Hardening is one more Azure security feature you can leverage to improve your Azure security posture.