How to Configure Fine-Grained Password Policy in Windows Server 2012 with PowerShell
How can I create a fine-grained password policy in Windows Server 2012 with PowerShell?
Fine-grained password policy was introduced in Windows Server 2008 to overcome restrictions that had previously existed, where it was possible to set only one password policy for an entire domain. Fine-grained password policies allow sysadmins to apply different password policies to groups of users in an Active Directory domain.
Make sure that your domain is set at the Windows Server 2008 domain functional level or higher. For more information, see “Raising Windows Server 2008 Active Directory Domain and Forest Functional Levels” on the Petri IT Knowledgebase.
Configuring Fine-grained Password Policies Using PowerShell
If you would prefer to use the GUI for configuring fine-grained password policy, see my previous post on “How to Configure Fine-Grained Password Policy in Windows Server 2012 using ADAC.” If you want to continue reading, don’t worry, setting fine-grained password policy using PowerShell is quite easy.
- Log in to a Windows Server 2012 domain controller as a domain administrator.
- Open a PowerShell console using the icon on the desktop taskbar or from the Start screen.
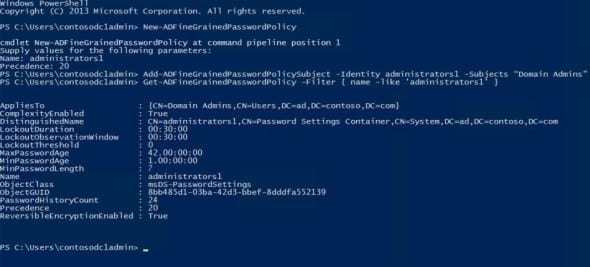
- In the PowerShell console, type New-ADFineGrainedPasswordPolicy and press Enter.
- At the Name: prompt, type a name for the new policy and press Enter.
- At the Precedence: prompt, type a precedence index number and press Enter. Policies with lower precedence index numbers take priority over those with higher numbers.
Using this method, the new policy will be configured with all the default values for a new policy. To configure specific values, you need to add parameters to the cmdlet as shown below:
New-ADFineGrainedPasswordPolicy -Name administrators1 -DisplayName administrators1 -Precedence 100 -ComplexityEnabled $true -ReversibleEncryptionEnabled $false -PasswordHistoryCount 10 -MinPasswordLength 8 -MinPasswordAge 3.00:00:00 -MaxPasswordAge 30.00:00:00 -LockoutThreshold 3 -LockoutObservationWindow 0.00:25:00 -LockoutDuration 0.00:30:00
Now we need to apply the policy to a user(s) or group(s).
- Back in the PowerShell console, type Add-ADFineGrainedPasswordPolicySubject -Identity administrators1 -Subjects “Domain Admins” and press Enter, replacing <administrators1> with the name of your password policy and <Domain Admins> with the name of the group or user you want to apply the policy to.
- To confirm that the policy has been applied to the group or user correctly, type Get-ADFineGrainedPasswordPolicy -Filter { name -like ‘administrators1’ } and press Enter, replacing <administrators1> with the name of the password policy you want to check.
In the resulting output, check the AppliesTo information to check the policy is applied to the intended user or group.