Resilient File System (ReFS) is the new file system that was introduced in Windows Server 2012 (WS2012). It offers the promise of a CHKDSK-free life. ReFS accomplishes this and prevents bit rot using built-in mechanisms, with the idea that time-consuming offline maintenance should become a thing of the past. WS2012 Cluster Shared Volumes (CSVs) do not support ReFS; therefore the new files system was of no use to highly available Hyper-V hosts or Scale-Out File Server (SOFS) SMB 3.0 storage. That changes in Windows Server 2012 R2 (WS2012 R2); CSV does support ReFS, and therefore you can use the new file system in Hyper-V clusters’ CSVs and SOFS clusters.
Today I’m going to cover how to disable the integrity bit of virtual hard disks copied to an ReFS volume using PowerShell cmdlets.
How to Disable the Integrity Bit of a Virtual Hard Disk
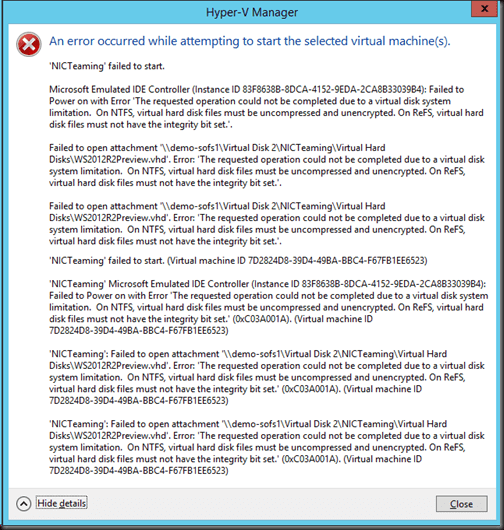
There is a requirement when you use ReFS volumes to store Hyper-V virtual machines. The integrity bit of the virtual hard disks (VHD or VHDX) that are stored in the ReFS volume(s) must be turned off. You will get the following error in Hyper-V Manager if you try to turn on a virtual machine that has virtual hard disks with this integrity bit turned on:
The solution is to disable the integrity bit of each virtual hard disk. This is a good news and a bad news story.
- The good news: Virtual hard disks (either VHD or VHDX) that are newly created on a ReFS volume have the integrity bit turned off by default. There is no extra work for you to do or script.
- The bad news: You will need to disable the integrity bit of any virtual hard disk that is copied to a ReFS volume.
Configuring the integrity bit is done using a PowerShell cmdlet called Set-FileIntegrity. You can query the status of the integrity bit using Get-FileIntegrity. The mistake here will be to try running the following:
Get-FileIntegrity MyVirtualHardDisk.VHDX
Unfortunately both Get- and Set-FileIntegrity are a bit dumb, and that just won’t work. You will be rewarded with the following error:
Get-FileIntegrity : The system cannot find the file specified.
However, the following example will work, and it will tell you if the integrity bit is enabled or not for this particular virtual hard disk:
Get-Item MyVirtualHardDisk.VHDX | Get-FileIntegrity
Once you have confirmed the problem you can turn off the integrity bit using:
Get-Item MyVirtualHardDisk.VHDX | Set-FileIntegrity -Enable $False
Querying the Integrity Bit Status for Many Virtual Hard Disks
Earlier I said that the problem is limited to virtual hard disks that are copied to a ReFS-formatted volume. What if you have copied lots of virtual machines to a ReFS volume? Do you really want to set each and every file, one at a time? Hopefully the answer to that is no, and if so, you can use the following PowerShell snippets. You can browse to the root of your ReFS volume and run this first example to query the status of the integrity bit for all of your virtual hard disks:
Get-ChildItem -Recurse | Where {$_.Extension -EQ “.VHD” -or $_.Extension -EQ “.VHDX”} | Get-FileIntegrity
The above snippet will do the following:
- Use Get-ChildItem -Recurse to search every subfolder
- Filter the search results to include only VHD or VHDX files (the Extension attribute is not case sensitive)
- Query the integrity bit using Get-FileIntegrity
Once you know that there are files to modify then you can take out the big gun: The next snippet uses the basis of the above search and changes it to only modify the integrity bit of virtual hard disks that require action:
Get-ChildItem -Recurse | Where {$_.Extension -EQ “.VHD” -or $_.Extension -EQ “.VHDX”} | Get-FileIntegrity | Where {$_.Enabled -EQ $true} | Set-FileIntegrity -Enable $False
Now, the above snippet will do the following:
- Use Get-ChildItem -Recurse to search every subfolder
- Filter the search results to include only VHD or VHDX files (the Extension attribute is not case sensitive)
- Use Get-FileIntegrity to query the integrity bit status of the virtual hard disks
- Filter the results to include only files where the integrity bit is set to $true (enabled)
- Run Set-FileIntegrity -Enable $False to disable the integrity bit
Armed with these cmdlets, you should be able to get your virtual machine with copied virtual hard disks up and running on a ReFS volume.