
The US Department of Homeland Security has issued a security advisory about the risks associated with Log4j vulnerabilities. The DHS’ Cyber Safety Review Board (CSRB) warned that the security flaw is expected to affect federal agencies and organizations until at least 2032.
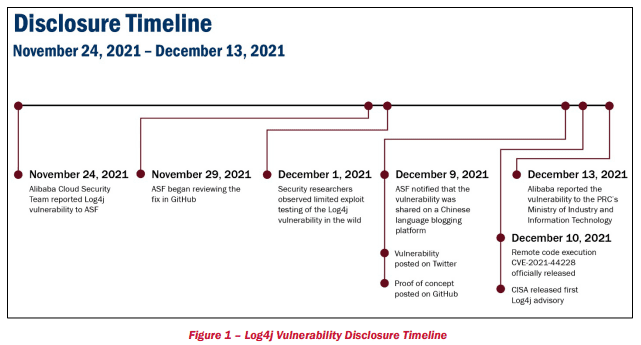
For those unfamiliar, Apache Log4j is a popular open-source Java-based logging framework. It enables developers to collect and manage information about system activity. The critical Log4j vulnerability (known as Log4Shell) was first disclosed in December 2021, and it lets malicious actors gain full control of affected systems.
The Log4j system-logging code library is widely used in enterprise applications and cloud services. The vulnerability impacted several popular products sold by Oracle, IBM, VMware, SolarWinds, Cisco, and other vendors. At the time, the Cybersecurity and Infrastructure Security Agency (CISA) ordered federal agencies to patch their internet-facing network assets immediately.
CSRB has investigated the critical Apache Log4J flaw and published a report which suggests that it will continue to plague vulnerable systems for many years. “Most importantly, however, the Log4j event is not over. The board assesses that Log4j is an ‘endemic vulnerability’ and that vulnerable instances of Log4j will remain in systems for many years to come, perhaps a decade or longer. Significant risk remains,” CSRB said.
According to the report, CSRB is unaware of any major Log4j-based attacks against critical infrastructure. However, organizations still had to spend money and allocate human resources to locate implementations of the Log4j library in their products and suppliers’ software to protect their networks.
Recommendations to address continued risks of Log4J flaw
The report has provided several suggestions that could help businesses monitor and address the Log4J risks in the long term. First up, organizations should adopt best practices for security hygiene and vulnerability management. Companies should also invest in automated tools to ensure real-time monitoring of vulnerable systems.
Additionally, it is important to take necessary measures to protect the larger open-source software ecosystem. Software developers should engage in security uplift programs and get in touch with organizations that offer developer tools, training, audits, and other services required to assess the risks of open source projects. These include OpenSSF, Open Web Application Security Program, and The Open Source Software Security Mobilization Plan.



