In our previous series on Cisco IOS Access-lists Part 1 and Part 2 , we covered all the basics of ACL’s and went through a real-world example. In the past, it was not possible to edit an ACL. Now, the impossible is possible with IOS 12.2 or later. In this article, you’ll learn how you can edit your access-list by using line numbers. This will prevent you from having to remove, and recreate, your ACL whenever you need to modify it.
Creating the ACL with the ip access-list command
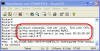
The key to being able to edit an ACL is to use the ip access-list command. Let me show you how it’s done. To start off, let’s create an ACL, like this: 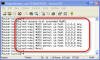
Editing the ACL with the ip access-list command
Next, let’s say that I want to edit the line that references host 5.5.5.5. In the past, I would have had to copy the ACL to a text editor (like Windows Notepad), remove the ACL on the router (during which time all traffic is allowed), edit the ACL in the text editor, and paste the ACL back into the router. This is a time consuming, and insecure, process to go through to edit a single line on an ACL. Now, you can edit your ACL’s with one caveat. You can remove and insert individual lines of an ACL but you cannot edit lines, in place, on the router. Let’s look at an example. To edit the line that references host 5.5.5.5, here is how you would do it: I went into the named ACL add/edit mode. In this mode I can add more lines to the end of the ACL, remove lines in the ACL, or insert lines in the middle of the ACL. In this case, I needed to edit the line with the “host 5.5.5.5” on it. I couldn’t actually edit that line on the router but I can easily remove it and re-add it. I did this without ever having to modify any other part of the ACL. To do this, I simply removed the existing line 500, replacing with no 500, then I added the new line 500 permit ip any host 5.5.5.5. By doing this, I reversed the source and destination that was permitted in this ACL. Let’s see what the entire ACL looks like with a show command:
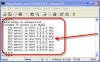
Inserting line in an ACL
By going back into ACL Edit mode, you could also insert a line in between the other lines. For example, you could do this:
We inserted a line number 450. Let’s see what it looks like when we do our show command: 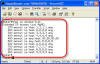
Summary
In summary, the ability to edit Cisco IOS ACL’s is a very powerful and time saving feature. In addition, by being able to edit the ACL’s, you don’t have to remove them and re-add them. In the past, when you had to remove them, your users or application would have suffered either: downtime (because you would have to shutdown the interface to protect the network), or lack of protection (because you would have to leave the interface without an ACL). Because we can now add, remove, and insert line numbers, we are all better off. More information on Cisco IOS named access lists can be found at the Cisco Command Reference for ip access-list website.
Related articles
You might also want to read the following related articles: