Cloud-Native SIEM and Built-in AI for Analytics with Azure Sentinel

Microsoft has gradually been transforming itself into a cloud and security company over the last few years. Now in public preview, Azure Sentinel brings many of the security features Microsoft uses to secure its own cloud environments to organizations that need to collect data from on-premise systems and cloud apps.
What is Azure Sentinel?
Currently, in public preview, Azure Sentinel is Microsoft’s take on a modern cloud-native Security Information and Event Management (SIEM) solution. While Splunk maybe one of the best known SIEM solutions today, Sentinel differs in that it is designed from the get-go to straddle cloud and on-premise infrastructure. And integration with Microsoft’s Security Graph gives Sentinel insight into cloud services that might not be otherwise possible when using Microsoft Software-as-a-Service (SaaS). The Security Graph is a set of APIs that Microsoft uses internally to monitor its own services, tracking millions of events daily to determine how even the slowest and stealthiest of attacks progress.
Because Sentinel is SaaS, it automatically scales when you need to collect more data and you only pay for what you use. It is designed to collect, detect, investigate, and respond to threats. Microsoft says that Sentinel will help organizations detect threats that were previously hidden in your infrastructure to preempt attacks – Microsoft calls this ‘hunting’ – and minimize false positives with the help of intelligence data collected by Microsoft.
Using artificial intelligence (AI) and years of intelligence data, Sentinel can surface suspicious activity and take necessary action to respond to incidents. Built-in AI reduces noise from data you collect so you can quickly focus on real security incidents.
Getting Started with Azure Sentinel
Sentinel is designed to be easy to set up and use, and low maintenance. I created a new workspace and added it to Sentinel. There are currently 24 connectors that let you pull in data from other systems, including Amazon Web Services (AWS) cloud trail, Azure Active Directory (AAD), Azure Advanced Threat Protection, Cisco ASA, F5, and the list goes on. Connecting AAD sign-in and audit logs was as simple as clicking Connect. Connecting Sentinel to non-Microsoft systems is a bit more complicated but in the case of AWS at least, full and detailed instructions are provided.
To view data, you need to add one or more dashboards. Again, this is as simple as choosing the kind of data you want to view and clicking Add. Once you’ve got a dashboard in place, you can customize the view by adding or removing tiles. Each tile represents a kind of information. For example, on an Azure AD dashboard, there are tiles for User Activity Summary and Service Health.
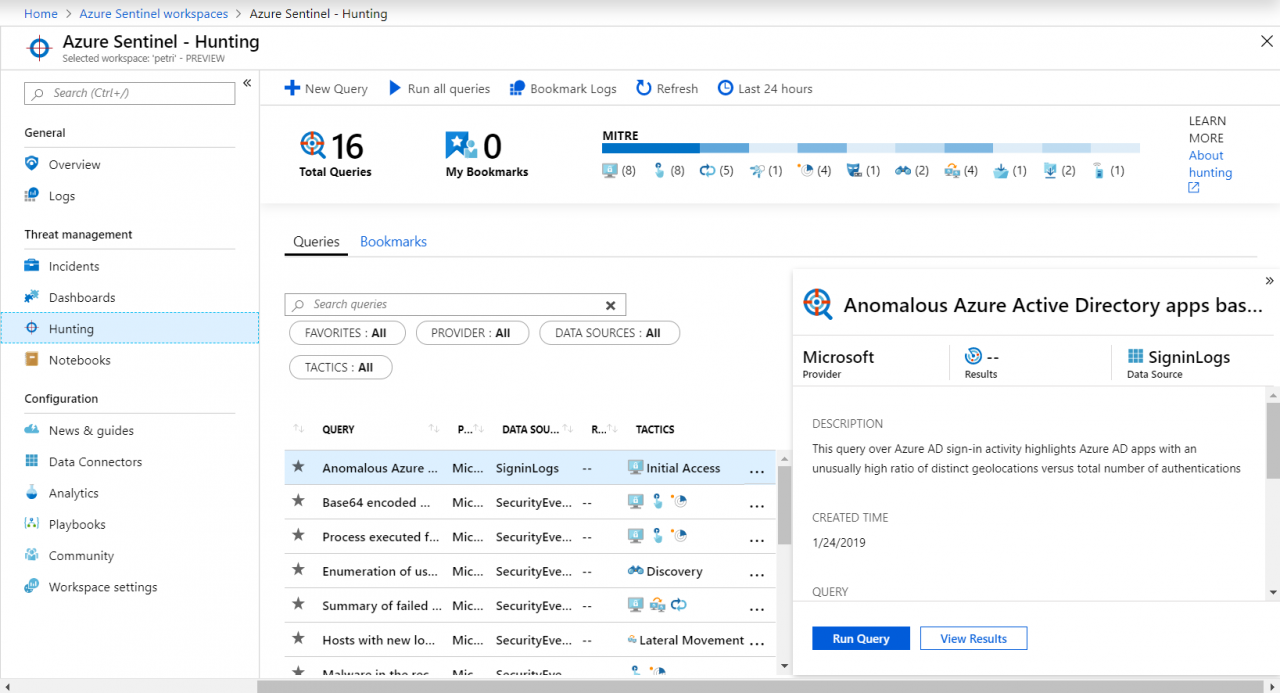
Incidents and Hunting
Incidents are automatically generated based on alert rules defined on the Analytics page. While it is possible to create alert rules manually, Microsoft provides a series of ‘detections’ on GitHub that you can use to automatically set up alert rules for common issues. The YAML files on GitHub can’t be uploaded to Sentinel as it stands. You need to copy the information into the correct alert rule fields. Assumedly, that will change at some point in the future.
Once you have some alert rules configured, you can also automate responses using playbooks. Security playbooks are based on Azure Logic Apps, which is another cloud service for scheduling, automating, and orchestrating tasks. Logic apps can be triggered by alert rules or run manually. Creating Logic Apps is a whole other topic, but in brief, Microsoft says that in many cases it is not necessary to write code. Microsoft provides a set of prebuilt APIs that can be used as connectors for running tasks on your systems.
The Hunting page contains a series of out-of-the-box queries that you can run against your data to dig out anomalies. You can also add your own queries using Microsoft’s Azure Log Analytics query language. In my lab, I don’t have enough data to evaluate the effectiveness of Microsoft’s built-in queries for AAD but as these are likely based on what Microsoft runs internally, I suspect that in a real-world deployment, they would prove useful.
First Cloud-Native SIEM Solution from a Major CSP
One advantage Sentinel has over Splunk, and other on-premise solutions, is the ability to quickly deploy a SIEM solution without any infrastructure and integrate with cloud services and apps. There’s no need to have your own servers, storage, or other infrastructure to get started with Sentinel. And that provides an advantage for the smallest to the biggest deployments. Where on-premise SIEM solutions might be out of reach for small organizations because of the initial deployment costs, Sentinel can cater for all sizes or organizations and needs.
It’s early days for Sentinel but if you have systems and apps that need monitoring, regardless of whether they are in the cloud or on-premises, and you want a flexible solution that doesn’t require any infrastructure to be deployed, you might want to check out Sentinel. Even if it doesn’t meet your needs right now, it might in the future as the service matures.



