What Is Azure AD Privileged Identity Management?
In today’s Ask the Admin, I’ll look at Azure Active Directory (AAD) Privileged Identity Management (PIM) and how it can help protect user identities in the cloud.
Privileged Identity Management is available to AAD Premium P2 subscribers and allows organizations to better control what users are doing with privileged accounts. Just like in an on-premises Active Directory (AD) environment, the use of privileged domain accounts, such as Domain Admins and Enterprise Admins, should be kept to a minimum. To help facilitate that, Windows Server 2016 includes a new feature called Just-In-Time (JIT) administration, which allows users to be granted privileges on a temporary, time-limited basis.
In AAD, Just-In-Time administration allows administrative privileges to be granted ‘on-demand’ to the directory and online services, such as Office 365 and Intune. Much of what Microsoft added to Windows Server 2016 was the result of features that were first appeared in Azure, so it should come as no surprise that JIT administration is also part of AAD. PIM also allows administrators to
- See which AAD users are tenant administrators.
- Run reports detailing changes and access attempts made by administrators.
- Set up alerts for access to privileged roles.
Eligibility and Activation
When PIM is enabled for a tenant, users that occasionally need privileged access can be assigned the role of Eligible admin, and only when they complete ‘activation’ are their accounts granted elevated privileges for a set period. Users activate a role by logging in to the AAD management portal and start the activation process on the Privileged Identity Management panel.
Each role supported by PIM accepts users that are either Permanent or Eligible members of the role. For instance, in the image below, you can see that users assigned the Global Administrator role have Permanent permission, others Eligible.
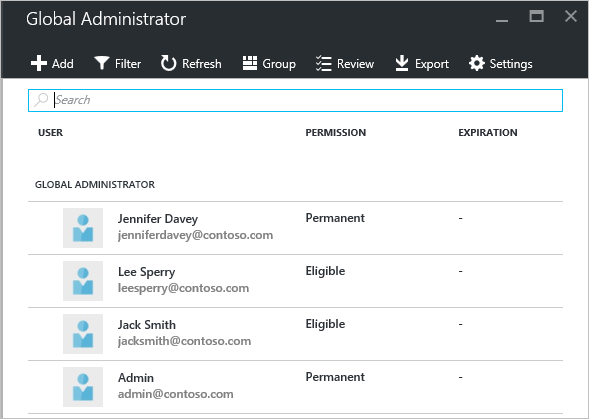
Roles have activation settings that determine the maximum amount of time for activation, how admins are notified of the activation, whether users requesting activation should provide any additional information such as a request ticket ID, and whether multifactor authentication is required.
Role Activity
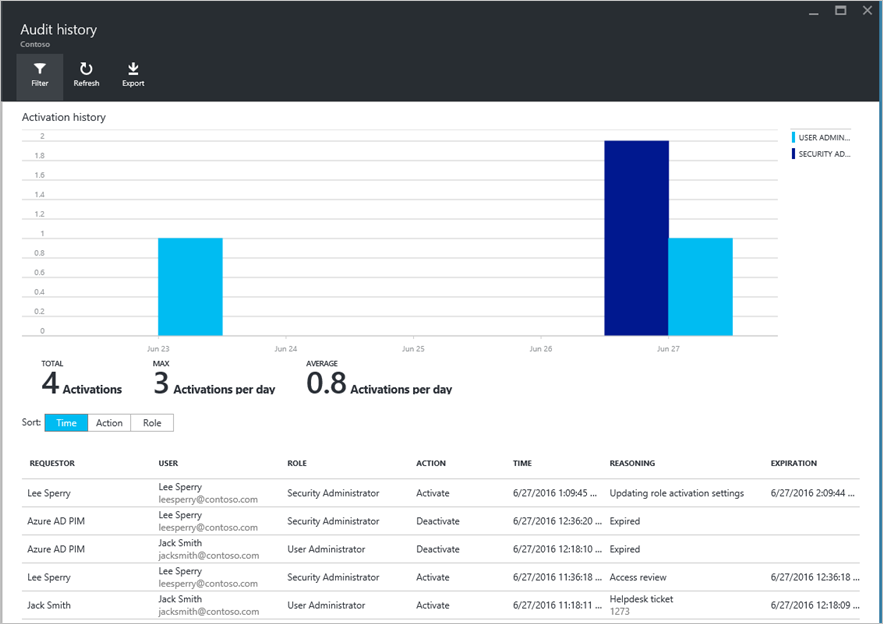
Administrators can view activity on the Audit history panel, where changes in privileged role assignment and activation history are recorded. Alternatively, access reviews can be configured, which requires an assigned person to review historical access data and determine who still requires privileged access.
In this article, I explained what AAD Privileged Identity Management is and how it can be used to improve the security of your AAD tenant.




