Overlooked Features in Window Server 2008 R2
I am as guilty as anyone when it comes to getting caught up with the latest, greatest version of Windows Server. I always advocate Software Assurance for Windows Server and its Client Access Licenses (CALs), especially when deploying (any) virtualization. But sometimes in this features race, we forget that not every business is in a position to maintain Software Assurance on server licenses or CALs. In my travels, I’m often surprised by how many administrators know so little of what is already available to them in their existing software acquisitions. In this article I’m going to talk about what I think are these oft-overlooked features in Windows Server 2008 R2 (W2008 R2).
Windows Server 2008 R2: Forgotten Features
Virtualization
This is where some readers will sigh while thinking “Here goes Aidan again on his Hyper-V trip”! I promise to keep this brief. I think at this time, most sane engineers and architects agree that the primary methods for deploying servers should be via virtualization or cloud. So this is why I’m jumping straight into this topic.
W2008 R2 came with the second release of Hyper-V. This version added live migration within Hyper-V clusters and Microsoft’s cluster file system, Cluster Shared Volume (CSV). With Service Pack 1 (SP1), W2008 R2 added RemoteFX for virtualizing graphics cards in Remote Desktop Services scenarios. And more importantly, Dynamic Memory was introduced to improve the assignment of memory to virtual machines based on the guest operating systems’ pressure to allocate RAM. With SP1, many businesses decided that Hyper-V was ready. However, I’m not going to tell you to start firing up the Hyper-V role in W2008 R2. That’s right, there is a way to make the most of your existing investment in W2008 R2 and its CALs, and use the latest virtualization and cloud solution from Microsoft.
Enter Hyper-V Server 2012 and the soon-to-be-released Hyper-V Server 2012 R2. These are the free versions of Windows Server that come with all the features and scalability of Hyper-V and failover clustering. One of the intended scenarios of Hyper-V Server is to allow businesses without Software Assurance to deploy the latest version of Hyper-V, and continue to use their legacy Server licenses in virtual machines. There are a few possibilities, depending on your existing deployment:
- No virtualization: You can deploy Hyper-V Server and convert your physical servers into virtual machines. Bear in mind that there are specific licensing rules for Windows Server when it is being virtualized on any virtualization platform.
- W2008 R2 Hyper-V: You can upgrade W2008 R2 Hyper-V hosts to Hyper-V Server 2012/R2 or migrate a legacy cluster to a new cluster that is running Hyper-V Server 2012/R2.
- VMware: Not everyone is running the latest or greatest version of vSphere either. Many businesses aren’t happy with the significant “virtualization tax,” as it has been dubbed by Microsoft marketing. Customers could convert vSphere virtual machines to run on Hyper-V Server 2012/R2 hosts/clusters.
Each of these scenarios could allow:
- Businesses to take advantage of all the great features and scalability of the latest version of Hyper-V.
- Stay on their existing version of Windows Server and CALs.
Hyper-V Server does not have a GUI. That can be scary at first, but don’t worry. A simple text-based wizard gets the new host on the network, and then you can manage it remotely from System Center or from your PC. The Remote Server Administration Toolkit (RSAT) for Windows 8 will manage Hyper-V Server 2012.
Better Together
Microsoft came up with the “Better Together” tagline for W2008 R2 and the Enterprise edition of Windows 7. The concept was that with both products, businesses could deploy better functioning and deeply integrated solutions for branch offices, remote access, control, and security.
Direct Access
There are two real needs for a remote- or mobile-worker connectivity solution:
- Simple-to-use and secure remote access to company resources
- Remote control, support, and management of end users and devices
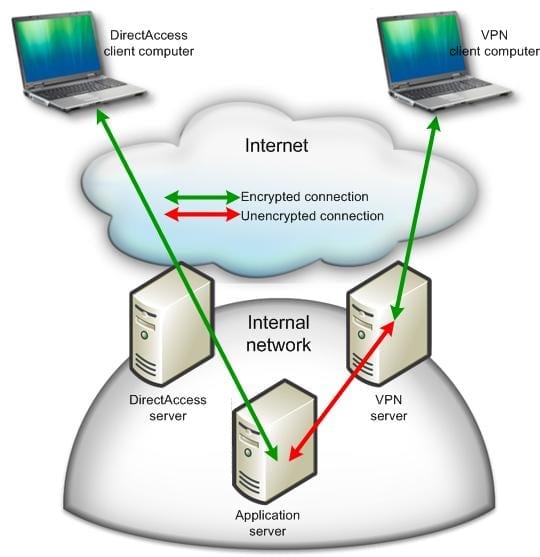
Microsoft came up with a VPN alternative called Direct Access. Where VPN allows the end user to sign into a client (often generating a helpdesk ticket to get things working) to punch a hole into the company network, Direct Access basically extends the company network to the mobile worker’s laptop once they log in. The solution allows the user to simultaneously access company and Internet resources. At the same time, corporate systems can manage the PC as if it were on a remote link in the company WAN.
Contrasting VPN and Direct Access.
Direct Access on W2008 R2 is complicated. The feature matured greatly in WS2012 and Windows 8. However, if you want a VPN alternative, then Direct Access might be something to look at.
BranchCache
It is the desire of nearly all, if not every, medium/large enterprise to centralize all servers into the head office or regional hubs. However, the performance of file and web services for remote office workers would suffer. You could deploy costly network caching solutions that do an amazing job of masking the latency of WANs for those remote workers. Alternatively, you can use BranchCache, a feature in the Enterprise edition of Windows 7 (and later) and powered by W2008 R2.
Administrators can enable BranchCache support in their file and web servers. Group policy can be engineered to configure BranchCache functionality in the desktop in two ways:
- Peer-to-peer model: Enterprise clients will work together to maintain a distributed cache of previously downloaded file blocks and reduce the overall download traffic while improving the end user experience.
- Centralized cache: A server, possibly a low-end micro-server with domain controller and DHCP roles, will provide a central cache in the branch office that never turns off. Clients will download non-cached blocks and store them on the local cache server for later reference.
BranchCache has become more than just a file and web server solution – System Center Configuration Manager can leverage BranchCache to support centralized content (Distribution Points), thus mimicking third-party solutions that are often deployed in widely dispersed environments such as retail.
There are more solutions in the “better together” package, but these are the highlights that build upon W2008 R2.
Active Directory (AD)
It’s quite surprising how many Active Directory forests run at Windows Server 2003 (W2003) forest functional level. To me, AD is one of the easiest “applications” to upgrade, and it can offer quick results.
Earlier this year I did a roadshow to highlight the new features of Windows Server 2012 (WS2012). We wanted to highlight the non-virtualization features because, lately, it seems that Hyper-V steals a lot of the limelight. We did an entire section on Active Directory. What amazed me at each event was that few realized that we were presenting features that were first introduced in W2008 R2. Here are some of the AD highlights you should check out:
- AD Recycle Bin: Every AD administrator dreads the day they have to do an authoritative restore to recover an OU full of users that was accidentally deleted. No need, as the AD Recycle Bin retains deleted items just like the Windows Recycle Bin, allowing you to undelete those lost objects.
- PowerShell: W2008 R2 gave us the first native PowerShell module for managing AD. A university can automate the creation of 10,000 student user accounts with just a single line of code parsing a comma separated values (CSV) file.
- Active Directory Administrative Center (ADAC): I wonder how many readers have never heard of or started this tool? Active Directory Users And Computers (ADUC) is an engineering tool, revealing lots of detail that can confuse operators and helpdesk staff. Unlike ADUC, ADAC focuses on day-to-day operational tasks such as finding an object or resetting a password, and that’s why shortcuts to those operations are the first thing you see in the console.
- Offline Domain Join: You can pre-stage computers to join Active Directory even if that PC is disconnected when it is built.
- Managed Service Accounts (MSAs): We’re supposed to change user passwords every X days (passphrases change less frequently). Lots of applications require AD user accounts so it’s unrealistic to change their password. By using an MSA instead of a normal AD user account, Windows will automate the password management for us, and keep security at a higher level.
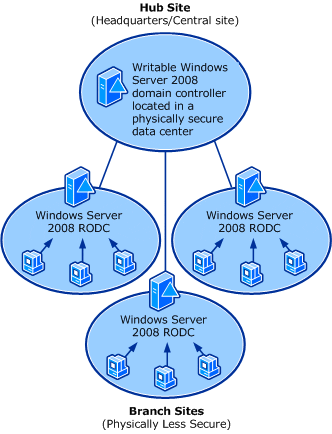
An even older feature, added in W2008, is the Read-Only Domain Controller (RODC). This is the ideal form of domain controller for branch offices where physical security cannot be guaranteed. Instead of maintaining a database of every user’s password hash, it caches passwords just for the branch office users, thus minimizing risk to the entire business. Once again, too few people are aware of this great solution.
Read-Only Domain Controllers in the branch office.
There’s Way More
I’ve just given you a small sample of the commonly overlooked features in Windows Server 2008 R2. There is a lot more for you to look at if you want to make the most of your investment in the Microsoft platform, and this may save you from increasing complexity by adding third-party products and vendor relationships. But don’t stop there – take a look at W2008 as well. There’s a good chance that you haven’t looked at Network Access Protection, Windows Deployment Services, and other great features that were added in W2008 and improved in W2008 R2.