Microsoft Defender for Endpoint Gets New Zeek Integration to Detect Network-Based Threats

Microsoft has partnered with Corelight to add a new Zeek integration to its Defender for Endpoint solution. The new integration helps to reduce the time required to detect sophisticated network-based threats in enterprise environments.
Zeek is an open-source tool that monitors network traffic packets to detect malicious activity within a network. Microsoft Defender for Endpoint can now inbound and outbound traffic with a new Zeek engine that can aggregate network protocol data across an entire TCP/UDP session.
According to Microsoft, these insights help to improve the detection of network-based attacks. It can also detect attacks on non-default ports and respond to emerging network-based threats such as Log4Shell and PrintNightmare.
“The integration of Zeek into Microsoft Defender for Endpoint provides a powerful ability to detect malicious activity in a way that enhances our existing endpoint security capabilities, as well as enables a more accurate and complete discovery of endpoints & IoT devices,” the company explained.
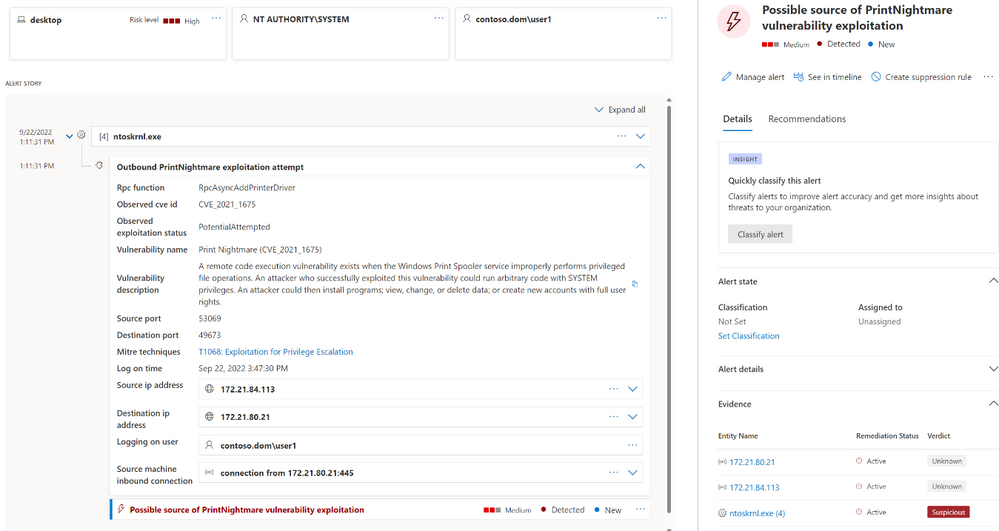
Microsoft Defender for Endpoint currently provides two Zeek-based detection capabilities for enterprise customers. The first feature allows IT admins to identify PrintNightmare exploitation attempts in their network. Moreover, Microsoft Defender for Endpoint can show alerts for proprietary password spray attacks.
Microsoft Defender for Endpoint adds new device discovery enhancements
Additionally, Microsoft says that the latest update brings improvements to passive device discovery capabilities in Microsoft Defender for Endpoint. This release brings out-of-the-box support for several popular device discovery protocols such as NTLM, SSH, and FTP.
Microsoft notes that the new Zeek integration doesn’t replace traditional Network Detection and Response solutions. Instead, it serves as a complementary data source that provides network signals that would otherwise be overlooked. “Microsoft recommends that security teams combine both data sources – endpoint for depth, and network for breadth – to gain full visibility across all parts of the network,” Microsoft added.



