Office macros are one of the most common ways hackers infiltrate Windows PCs. In this Ask the Admin, I’ll look at how you can secure Office 2016 to prevent attacks.
Macro-based malware used to be one of the most popular ways of infecting Windows and had largely become extinct. But at the beginning of 2015, Microsoft reported that macro-based malware had started to make a comeback. Despite efforts by Microsoft to bolster security in Office 2016, infections caused by macro-based malware are on the rise.
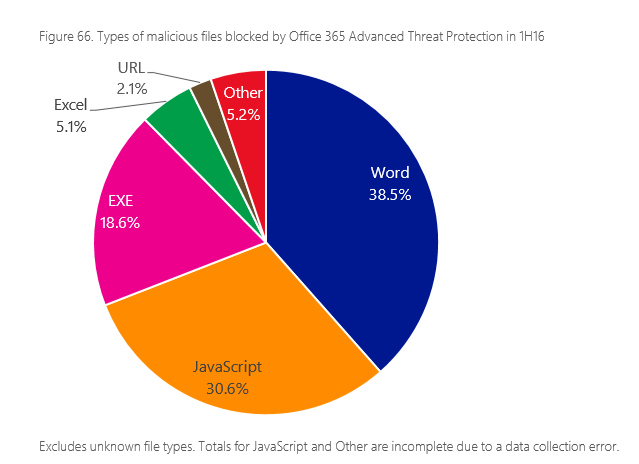
Microsoft’s Security Intelligence Report volume 21, which presents data collected from January to June 2016, shows that Microsoft Word documents were the most common file type to contain malicious payloads:
Microsoft Word files accounted for 38.5 percent of malicious files. Of these, the most common file extensions were .doc, used for the binary file format used in Word 97-2003 and .docm, used for Word documents that contain macros.
Visual Basic for Applications and Macros
Visual Basic for Applications (VBA) is a programming language, based on Visual Basic, that is included in the Microsoft Office desktop apps. Developers can use it to automate complex or repetitive tasks, or users can create macros to automate tasks without any programming knowledge. Like any powerful technology, VBA can be abused by hackers to run malicious code. According to Microsoft, 98 percent of all attacks against Office involve macros.
Attacks using macros are not new and there are technologies built into Office aimed at reducing the likelihood that users accidentally run malicious code. Protected View opens documents downloaded from the Internet zone in a sandbox, restricting active content and the ability to edit documents until users provide explicit permission. The Trust Center sets macro security to ‘Disable all macros with notification,” which means that once Protected View is turned off, users receive another warning before active content is enabled in the document.
Safety Mechanisms vs. Security Controls
It is important to understand that the default Trust Center settings in Office are designed to encourage users to consider whether they trust a document before opening it with full access to Office. It is also designed to provide a line of defense if a malicious document is opened accidentally or out of curiosity. Most of the default Trust Center settings are not controls to prevent users opening infected documents, but function as a safety mechanism that can be bypassed. Like seatbelts in cars, users can opt out of their use.
There are specific scenarios where Office documents open in Protected View:
- Downloaded from the Internet
- Received as an email attachment from an unsafe sender
- Is in an unsafe folder like the Temporary Internet Files folder
- Cannot be validated as a known format
- Is blocked by File Block policy
Depending on the scenario, users can bypass Protected View. Files downloaded from the Internet zone activate Protected View but this can be switched off by clicking Enable Editing. And that is not the only way. When files are extracted from zip archives using Windows, they retain the metadata setting that identifies them as downloaded from the Internet. If a third-party app is used, like 7-zip, that metadata is stripped out of extracted files. Alternatively, files can be ‘Unblocked’ by changing the file’s properties in File Explorer.
Once Protected View has been disabled, users receive another warning about the presence of active content, such as VBA code. Again, the default Trust Center settings provide this notification with the ability to Enable Content.
Disable Macros
The safety mechanisms in Office 2016 might provide a sensible balance between security and usability for security conscious, tech-savvy users. But can you risk letting unqualified staff make critical decisions about your organization’s security? Most users do not need access to advanced features like macros and VBA. Because of the threat that macros pose, I recommend that you disable macros in Office. Do not leave security to chance. Users ignore security warnings and can be easily tricked into disabling security defenses by social engineering.
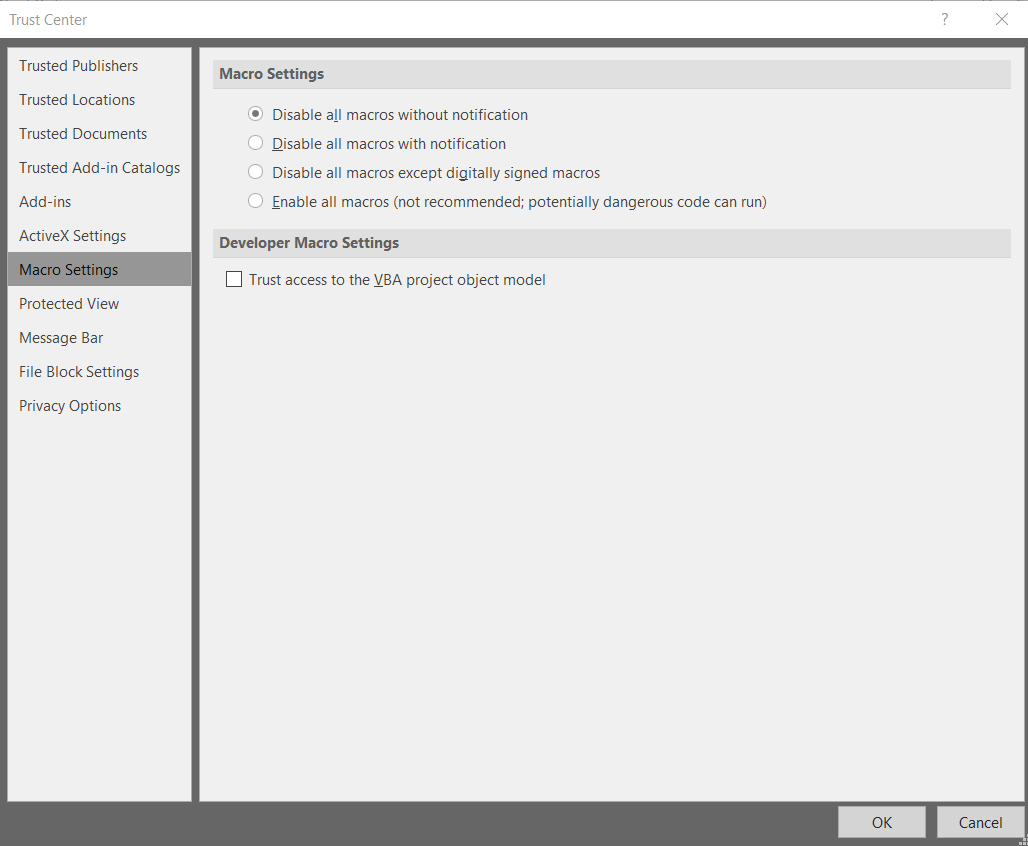
Use Group Policy to configure the Trust Center. Users should not be allowed to add trusted locations and macro security should be set to Disable all macros without notification. This setting means that users will not be presented with the option to enable active content even if they choose to turn off Protected View or somehow bypass it. If you want to truly disable macros, you must ensure that users cannot add trusted locations in the Trust Center or copy documents to any trusted locations that they have access to.
If you decide to stop short of disabling macros, you can tighten up the default Trust Center settings in a couple of ways. For example, you can block unsigned code or add trusted locations. Office 2016 also includes a Group Policy setting called Block macros from running in Office files from the Internet. This automatically blocks macros in documents downloaded from the Internet even if the Trust Center is set to Enable all macros.
Trusted Locations
Files in trusted locations open with full access to Office, regardless of whatever other restrictions you have in place. Documents opened from trusted locations are always trusted, so even if you disable macros in the Trust Center, including Disable all macros except digitally signed macros, active content will always run in documents opened from trusted locations.
If you have users that do need to work with macros, you can carefully manage one or more trusted network locations that are restricted to a limited set of documents, users, and permissions. Trusted locations can be set in the Trust Center. Trust Center trusted locations can also be defined using Group Policy and administrators can block users from defining their own trusted locations.
Signing VBA Code
Another option is to require that code embedded in Office documents is digitally signed. This method can work for documents produced in-house but getting business partners to sign code is not such an easy task. One way around this is to sign the code yourself in documents from business partners using a code-signing certificate issued by your own public key infrastructure (PKI) certification authority (CA). That way, you can avoid signing somebody else’s code using a certificate issued by a public root CA, which would be trusted by devices outside your organization. However, this not a recommended approach.
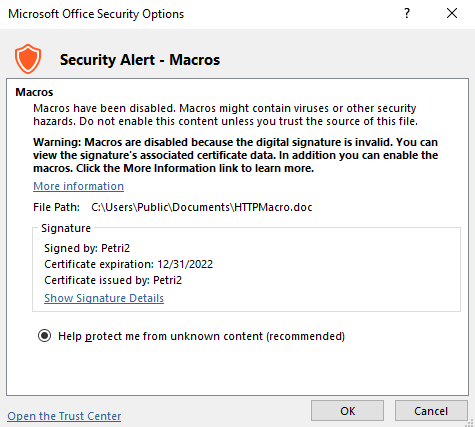
Disabling all macros except those that are digitally signed is not a security panacea. Far from it. Users can self-sign code in Office documents. Office 2016 only trusts self-signed certificates created by the logged in user on the device where the certificate was generated or where the certificate was added to the Trusted Root Certification Authorities folder in the Certificates-Current User store. You should consider the possibility that users might be persuaded to self-sign documents that they receive containing malicious VBA code through social engineering. It is not hard. Users may also try to import a self-signed certificate so that the malicious code becomes trusted by Office.
Block Binary and Open XML Macro File Formats
Open XML file formats, like .docx and .pptx, were introduced in Office 2007 to replace legacy binary file formats like .doc. One advantage of Open XML is better detection of malicious code because the document can be parsed more easily by antimalware software. When antimalware software scans Office documents, it is less accurate at detecting malicious payloads in binary file formats. Users cannot add VBA code to standard Open XML Office documents and must save documents using a file extension ending in ‘m’, such as .docm and .pptm if they contain VBA code.
The Trust Center is set by default to open Office 95, 6.0, and 2 documents in Protected View but does not allow editing. File Block can be set in Group Policy to enable this behavior for other file formats, so you might consider adding later Office versions of binary formats to the list.
With power comes responsibility. Microsoft Office is a powerful suite of tools that can drive your business to success. But like many technologies, there are drawbacks if you do not properly manage the risks.
Follow Russell on Twitter @smithrussell.




