In today’s Ask the Admin, I’ll show you how to enable two-factor authentication on a Microsoft account with the help of Microsoft’s Authenticator mobile app.
In What Is Multifactor Authentication and How Does It Work? on the Petri IT Knowledgebase, I explained the concept of two-factor and multi-factor authentication, and why you should enable it for sensitive accounts. Two-factor authentication (2FA) has been available in Office 365 for a couple of years, but you need to manually enable it for your users. Microsoft’s Authenticator app for iOS, Android, and Windows Phone makes it easier than ever to implement 2FA by using push notifications for verification rather than requiring users to type in access codes.
Before setting up 2FA for Office 365 users, make sure you enable Modern Authentication (MA) for Exchange Online if users are accessing Exchange using Outlook 2016 or 2013. Versions of Outlook prior to 2013 don’t support Modern Authentication. For details on how to enable MA for Exchange Online tenants, see Enable Modern Authentication in Exchange Online.
I’ve tested 2FA with Microsoft’s mobile Office apps, Outlook Groups, Office 2016 desktop apps, and OneDrive for Business in Windows 10, and found no problems. But there may be apps that are incompatible or require an app password, so make sure you test all the apps in your organization before enabling 2FA.
If you intend to set up 2FA for tenant administrator accounts, you should note that those accounts won’t be able to sign in to Office 365 using PowerShell. Microsoft recommends creating a specialized account for each administrative user for the purposes of accessing Office 365 via PowerShell. These accounts should be disabled when not in use.
Enable 2FA in the Admin Portal
The first step is to enable 2FA for one or more users in the Office 365 admin portal. 2FA can be enabled for individual users or in bulk. In this demo, because I’m testing 2FA before I roll out the feature to all users, I’ll enable 2FA for one account only. Before continuing, I recommend installing Microsoft Authenticator on your mobile device, not to be confused with Authenticator, a similar app from Microsoft but without support for push notifications.
- Log in to the Office 365 admin portal here using an administrator account.
- In the menu on the left of the portal, expand Users and Active users.
- In the list of users, click the user for which you want to enable 2FA. Note the only licensed users can use 2FA.
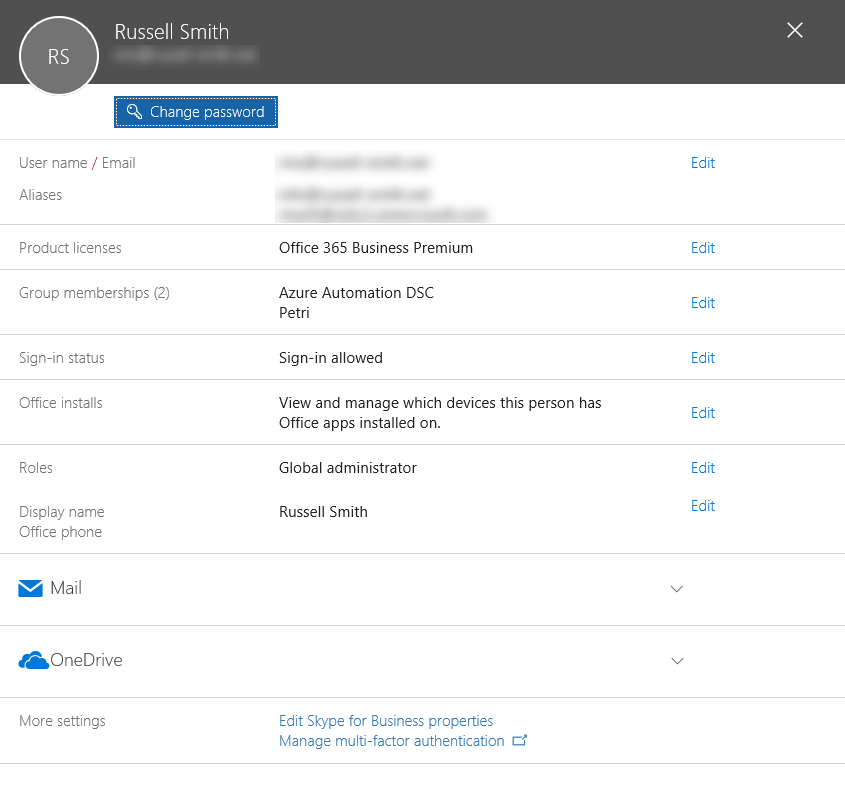
- In the user’s pane, click Manage multi-factor authentication under More settings.
- On the multi-factor authentication screen, select the user account to enable, and then click Enable under quick steps on the right.
- In the About enabling multi-factor auth dialog box, click enable multi-factor auth.
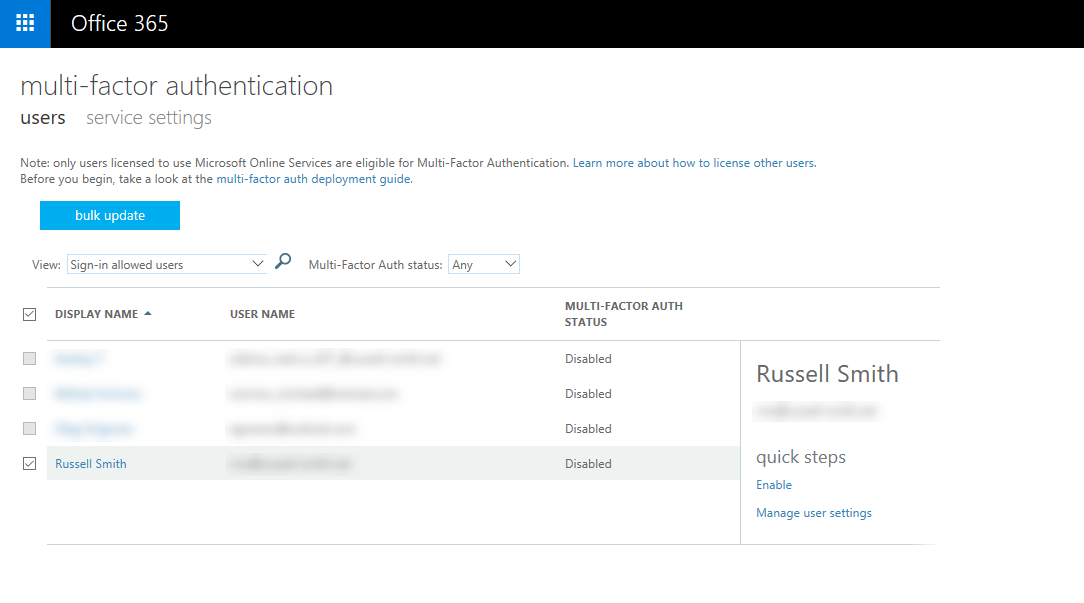
The MULTI-FACTOR AUTH STATUS column for the user will change to Enabled. Close the browser window and sign out of the admin portal.
Enroll Account for 2FA
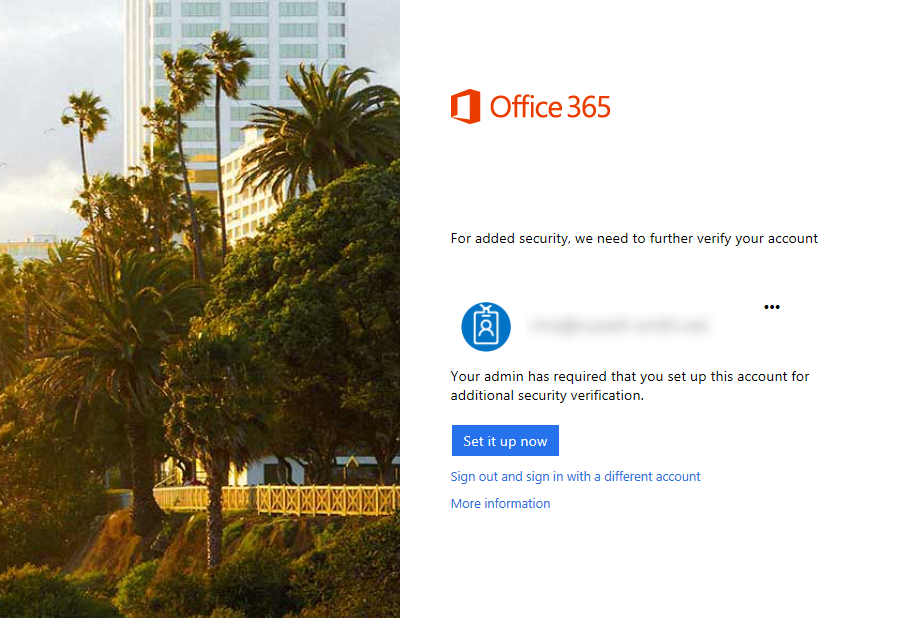
The user is then required to enroll for 2FA once the feature has been enabled for their account by an administrator. The user should sign in to Office 365 as usual with their username and password, and then click Set it up now on the sign in screen and follow the instructions below:
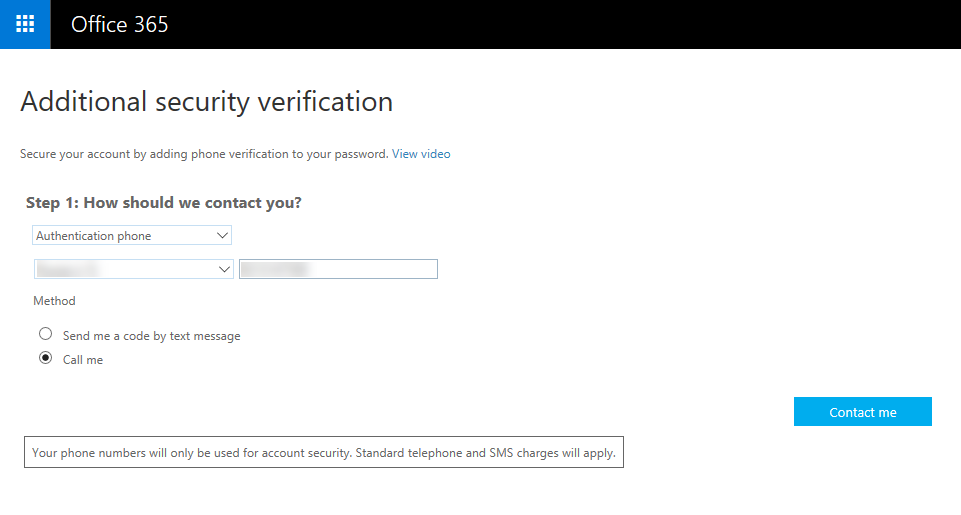
- On the Additional security verification screen, select Mobile app from the menu below Step 1: How should we contact you?
- Select Receive notifications for verification
- Click Set up
- Open the Microsoft Authenticator app on your phone and click Scan Barcode.
- Use the camera on your phone to scan the barcode in the Configure mobile app dialog. You’ll then need to wait a couple of seconds while the app activates the new account.
- Click Finished in the browser window.
- Back on the Additional security verification screen, click Contact me.
- You’ll receive a notification on your phone. Open it and you’ll be taken to the Microsoft Authenticator app. Click Verify to complete the sign-in process.
- Click Close in the Microsoft Authentication app.
- In the browser window, enter a number to which you will receive verification codes in case you lose access to the Microsoft Authenticator app, and click Next.
Web-based and mobile apps can use Microsoft Authenticator app verifications for 2FA logins, but Office desktop apps require an app password. The final step provides you with an app password for these apps.
- Finally, copy the app password by clicking the copy icon to the right of the password, and paste it somewhere safe. Click Finished.
You’ll be prompted to sign in again, this time by verifying the login using the Microsoft Authenticator app.
In this article, I showed you how to enable 2FA for Office 365 user accounts and how users should enroll once 2FA has been enabled for their accounts, using the Microsoft Authenticator app for verification.




