In this Ask the Admin, I’ll show you how to connect to Windows 8 remotely using PowerShell Remoting.
In my previous Ask the Admin post, I showed you how to configure PowerShell Remoting in Windows 8 using the command line, or Group Policy for PCs joined to an Active Directory (AD) domain. If you missed it, see How to Enable PowerShell Remoting in Windows 8. The steps in this article can also be used to remote to Windows Server 2012.
This article discusses the use of PowerShell Remoting without any special configuration. I.e. there are no constrained endpoints, or use of WinRM over HTTPS. As such, you should remember that the default WinRM configuration is intended for use on secure private networks. PowerShell Remoting using WinRM over HTTPS is more complicated to set up as it requires the use of certificates.
Establishing trust with the WinRM client
Before you can connect to a remote computer using PowerShell Remoting, that computer must be trusted by the WinRM client, i.e. the computer from which you are making the remote connection. In an Active Directory domain, or when PowerShell Remoting is configured to use HTTPS, Kerberos authentication and certificates respectively provide a means to determine if the remote computer is trusted, as long as the remote computer is specified by name and not IP address.
If both the remote computer and WinRM client are not members of the same domain, or not members of a trusted domain, then you will need to make an exception on the WinRM client computer to allow a connection to the ‘untrusted’ remote computer by making an entry for the remote computer in the TrustedHosts list on the WinRM client.
Adding a remote PC to a WinRM client’s TrustedHosts List
If you need to add a remote computer to the WinRM client’s TrustedHosts list, run the following PowerShell command from an elevated prompt, replacing mycomputername with the name of the remote computer you want to add to the list.
set-item wsman:localhostclienttrustedhosts mycomputername -concatenate –force
To open a PowerShell command prompt with administrative privileges:
- Log in to Windows 8.
- Switch to the Start screen, type powershell and make sure that Windows PowerShell is selected in the search results.
- Press CTRL+SHIFT+ENTER to start PowerShell with administrative privileges. If prompted, give consent or enter administrator credentials to continue.
Trusted Hosts can also be managed using Group Policy under Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Remote Management (WinRM).
Making a PowerShell connection to a remote Windows 8 PC
Now we understand that one way or another the remote computer must be trusted by the WinRM client, we can make a connection.
- Close the PowerShell prompt used in the previous steps. We don’t need administrative privileges on the local computer.
- Switch to the Start screen, type powershell and make sure that Windows PowerShell is selected in the search results. Press ENTER to open a new PowerShell prompt.
- In the PowerShell prompt type the command below, replacing username with the name of a user account that has administrative privileges on the remote computer, as required by the default PowerShell endpoints; and computername with the name of the remote computer.
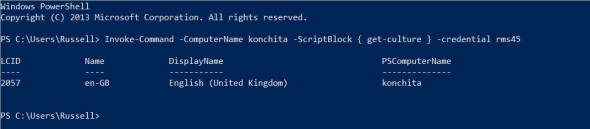
Invoke-Command -ComputerName computername -ScriptBlock { get-culture } -credential username
- In the security dialog, enter the password for the user account specified in the command and click OK.
The above command runs the get-culture cmdlet on the remote computer. You can see the output in the figure below.
Use the Invoke-Command cmdlet to run commands on a remote PC. (Image: Russell Smith)
You can use the invoke-command cmdlet to run a command simultaneously on many computers:
Invoke-Command -ComputerName computer1, computer2, computer3 -ScriptBlock { get-culture } -credential username
Or to run a script as shown here:
Invoke-Command -ComputerName computer1, computer2, computer3 -filepath “c:myscript.ps1” -credential username
Interactive sessions
If you want to type a series of commands, as if you were sitting at the local terminal, open a session on the remote computer.
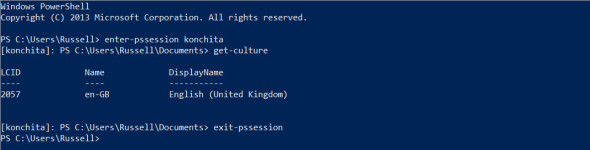
- Type enter-pssession computername in the PowerShell prompt and press ENTER, replacing computername with the name of the remote computer.
- Enter an administrator username and password in the security dialog if prompted and click OK.
- The prompt in the PowerShell window will now change to indicate that you are running commands on the remote computer.
- To exit the session, type exit-pssession and press ENTER.
Start an interactive session on a remote PC. (Image: Russell Smith)
Persistent sessions
Finally, persistent sessions are useful if you need to share data between commands. To open a new persistent session type:
$session = new-pssession -computername computername
And then run some commands that pass data using a variable, $culture in this example:
invoke-command -session $session {$culture = get-culture}
invoke-command -session $session {write-host $culture.Name}
The write-host cmdlet displays the name property of the culture of the remote computer in the PowerShell prompt, which in my case is en-GB.