Windows Server 2012: First Five Fixes
I think Windows Server 2012 will fundamentally change the way IT Pros manage their Windows environments. I expect many of you are already kicking the tires on Windows Server 2012 and perhaps are even running it in a limited, testing environment.
When you first build a new system, and there are a number of ways to do it, I expect you will have a checklist of standard steps. Eventually, you will be like all the cool kids and use a PowerShell workflow, but for now I’m going to assume you will be employing a manual process.
I assume you will do the following tasks by default when setting up a new Windows Server 2012 system:
- Configure computer name
- Configure networking
- Install features and roles
- Run Windows Update
I’m not going to cover those as I think they are pretty self-evident in the Server Manager GUI, but I do have 5 additional “fixes” that I’ve been using. These are things that you may not think of immediately, but they will pay off down the road. My “First Five Fixes” aren’t in any order, but I’m assuming you’ve completed at least the default steps above before moving on to these.
Note: This article is based on a pre-release version of Windows Server 2012 and is naturally subject to change.
5. Enable PowerShell Remoting
Windows Server 2012 relies on PowerShell remoting, and for the most part, it is now turned on and enabled by default. I may eventually change my mind on this one, but for now I like seeing for myself that remoting is enabled. Open an elevated PowerShell session and run the following command:
PS C:\> enable-psremoting
You will be prompted for a number of settings. You should be able to accept the defaults as I did in Figure 1.
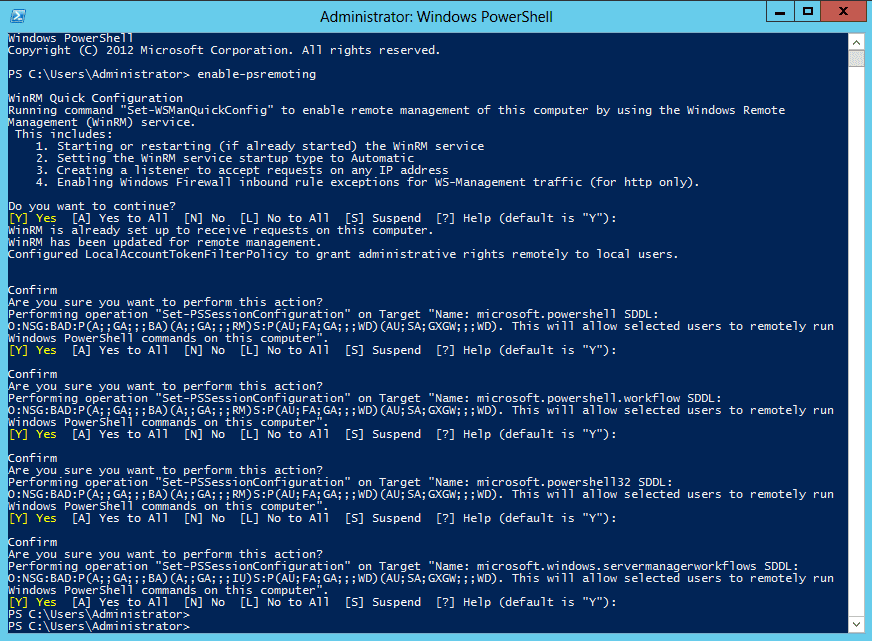
But now I have visual confirmation that remoting is enabled and I know what was set. If you want to skip all the prompts, simply run:
PS C:\> enable-psremoting -force
4. Set PowerShell Execution Policy
Next, at least for the servers I’m setting up, I will likely need to run PowerShell scripts. I need to set my execution policy accordingly. I prefer a setting of RemoteSigned at a minimum.
PS C:\Users\Administrator> Set-ExecutionPolicy remotesigned Execution Policy Change The execution policy helps protect you from scripts that you do not trust. Changing the execution policy might expose you to the security risks described in the about_Execution_Policies help topic at http://go.microsoft.com/fwlink/?LinkID=135170. Do you want to change the execution policy? [Y] Yes [N] No [S] Suspend [?] Help (default is "Y"):
As with Enable-PSRemoting, if you want to suppress the prompts, use the –Force parameter.
3. Update PowerShell Help Files
Because I’m going to spend a lot of time in Powershell, and I assume you will as well, we’ll need to update the help files. PowerShell 3.0 doesn’t ship with help content, so the first time you ask for help you’ll be prompted to update it if you haven’t already. Now is as good a time as any. In the same elevated PowerShell session, run this command:
PS C:\> update-help
You might get an error depending on what modules PowerShell finds on your server, because some of them haven’t been configured yet to support updateable help, or the files aren’t available yet. But you should be able to run this command:
PS C:\> help show-command –full
This should be a good indication that at least the core files have been updated.
2. Export Feature Configuration
Once the initial server configuration is complete, I recommend exporting it to an XML file. This allows you to re-use the XML file later to either rebuild the server, or duplicate the feature set on another server. When you go through the GUI to add a feature, there is an option at the bottom of the screen to export the file. I’ve highlighted it in Figure 2.
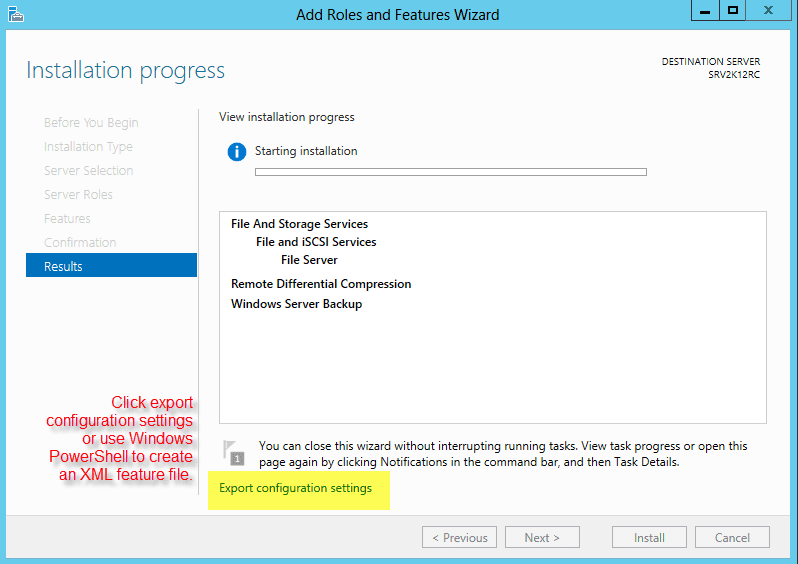
Figure 2 Export Features
PS C:\> Install-WindowsFeature –configurationfilepath \\file02\configs\Documents\2012Baseline.xml
1. Run Best Practices Analyzers
Finally, on a fresh install, you’ll see warnings until you run the Best Practices analyzer for each installed role. Instead of going through the GUI and manually launching each one, we can use PowerShell. It is actually quite easy to find the best practices scan for each installed feature.
PS C:\Users\Administrator> get-windowsfeature | where installed | get-bpamodel -erroraction silentlycontinue
Id : Microsoft/Windows/DNSServer
Company : Microsoft Corporation
Name : Microsoft DNS Server Configuration Analysis Model
Version : 1.0.0.0
LastScanTime : Never
LastScanTimeUtcOffset :
SubModels :
Parameters :
ModelType : SingleMachine
SupportedConfiguration :
Id : Microsoft/Windows/FileServices
Company : Microsoft Corporation
Name : File Services
Version : 1.0
LastScanTime : Never
LastScanTimeUtcOffset :
SubModels : {Dedup, DFSN, DFSR, FSRM...}
Parameters :
ModelType : SingleMachine
SupportedConfiguration :
I’m turning off the error pipeline because not everything you get from Get-WindowsFeature has a BPA. But now, it is very easy to revise this command and run the scan for each.
PS C:\Users\Administrator> get-windowsfeature | where installed | get-bpamodel -ea silentlycontinue | Invoke-BpaModel
ModelId : Microsoft/Windows/DNSServer
SubModelId :
Success : True
ScanTime : 6/25/2012 9:53:07 PM
ScanTimeUtcOffset : -04:00:00
Detail : {SRV2K12RC, SRV2K12RC}
ModelId : Microsoft/Windows/FileServices
SubModelId :
Success : True
ScanTime : 6/25/2012 9:53:13 PM
ScanTimeUtcOffset : -04:00:00
Detail : {SRV2K12RC, SRV2K12RC}
When everything is finished, I can view the results in Server Manager.
Summary
As we gain experience with Windows Server 2012 I expect this list will change slightly and certainly grow. I’ll be adding more content on Server 2012, especially once it is finally released.



