Microsoft Delivers Another Fix to Patch Outlook Privilege Escalation Vulnerability

Microsoft has released a security update to address a critical Outlook vulnerability that affects all versions of Windows. The new security flaw (CVE-2023-29324) allowed threat actors to bypass patches for the original Outlook bug that was already patched in March 2023.
Microsoft disclosed the privilege escalation flaw (CVE-2023-23397) in Outlook for Windows back in March. It enables attackers to send a malicious email to a vulnerable Outlook version to steal the NTLM password hash. The threat actors could use the hash to authenticate as the user and launch NTLM relay attacks.
Microsoft has confirmed that Russian APT28 state hackers exploited CVE-2023-23397 to target around 14 organizations from mid-April to December 2022. The hackers specifically launched attacks on the government, military, energy, and transportation sectors.
On March 14, Microsoft released a bunch of security patches to address the vulnerability in Outlook 2016 and Outlook 2013. The company also released a PowerShell script to help IT admins track and fix suspicious items in on-premises and cloud environments.
Researchers bypass Outlook privilege escalation flaw mitigation
Interestingly, Akamai security researcher Ben Barnea has found another issue in a related Internet Explorer component. It allowed the researcher to bypass the March 2023 patch and trigger the Outlook for Windows client to connect to the attacker-controlled server.
“Our research indicates that the new vulnerability allows exploitation of a critical vulnerability that has been observed in the wild and exploited by APT (Advanced Persistent Threat) operators. We continue to believe that our discovery is of great consequence. In the hands of a malicious actor, it could have the same consequences as the critical original Outlook bug,” Microsoft explained.
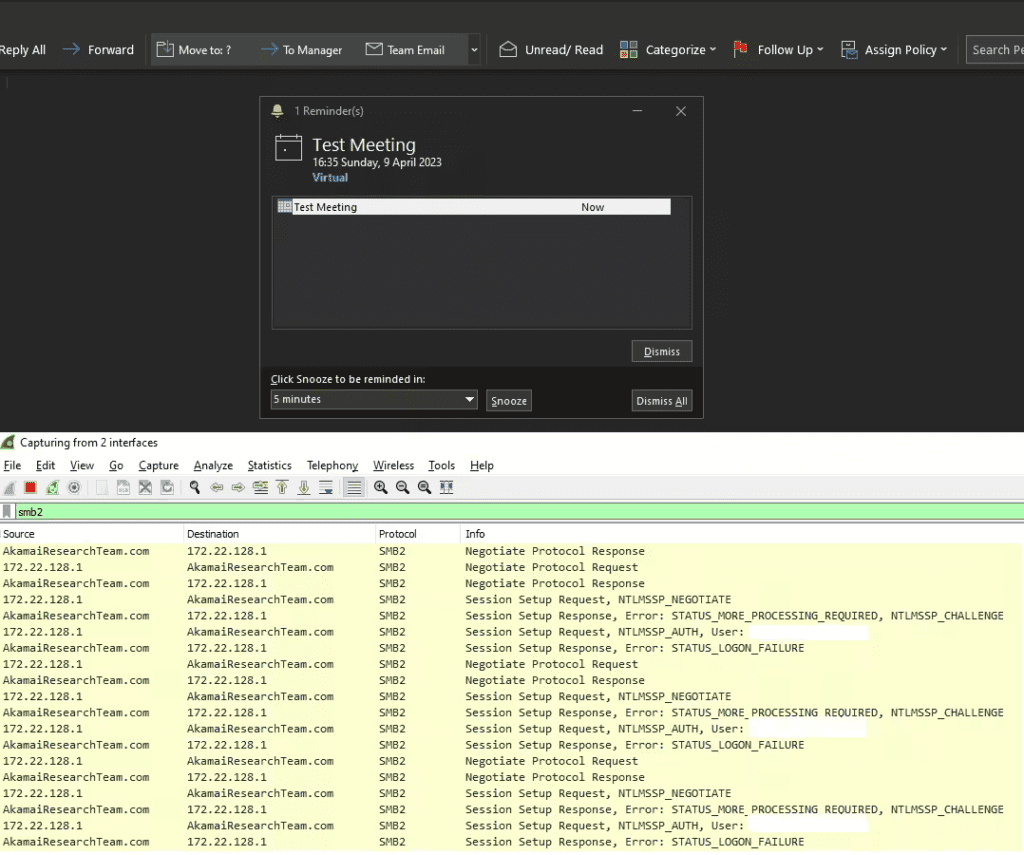
Microsoft recommends customers to install the May 2023 Patch Tuesday updates available for Windows Server 2012, Windows Server 2012 R2, Windows Server 2008, and Windows Server 2008 R2. Moreover, Outlook users will also need to install the latest cumulative updates released for Internet Explorer 11 to block cyberattacks.


