Windows Server 2016: Apply Filters on DNS Queries
In today’s Ask the Admin, I’ll show you how to use DNS Policy in Windows Server 2016 to apply filters to DNS queries.
DNS Policies are a new feature in Windows Server 2016 that allow administrators to determine how DNS servers respond to client queries, based on several factors, including the client’s location, the time of day, transport protocol, etc. In Network Traffic Management Using DNS Policies in Windows Server 2016 on the Petri IT Knowledgebase, I introduced the concept of DNS Policy and how to use policies to manage network traffic.
In this article, I’ll show you how to create a DNS Policy that applies filters to DNS queries, creating blackholes for malicious domains, or whitelists that restrict clients to resolving a predefined list of domain names.
Server and Zone-Level Filters
Before we start, it’s worth mentioning that policies can be set at the DNS server or zone level. For the purposes of this article, I’ll set all the policies at server level, but if you need more granular control, you can modify the command lines below to apply zone-level filters. Just add the -ZoneName parameter to specify the DNS zone name to which the policy should apply.
Create a Policy to Block a Malicious DNS Zone
Log in to Windows Server 2016 with an account that has DNS administrator permissions and open a PowerShell prompt. The policy below will create a filter that blocks resolution of the malware.com domain. Note the use of IGNORE for the -Action parameter, and EQ is a logical operator that means equals.
Other operators, such as NE (Not Equals) and OR, can also be used with Add-DnsServerQueryResolutionPolicy, but each parameter has different rules about which logical operators can be used. To get more information, run Get-Help Add-DnsServerQueryResolutionPolicy -Full.
Add-DnsServerQueryResolutionPolicy -Name 'BlockListPolicy' -Action IGNORE -FQDN "EQ,*.malware.com"
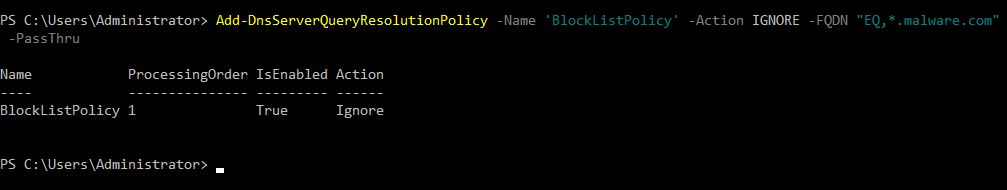
Once the command has run, DNS clients will no longer be able to resolve domain names in the malware.com domain and its subdomains. Don’t forget that if your DNS clients have cached previous queries for malware.com, you’ll need to run ipconfig /flushdns to clear the local cache.
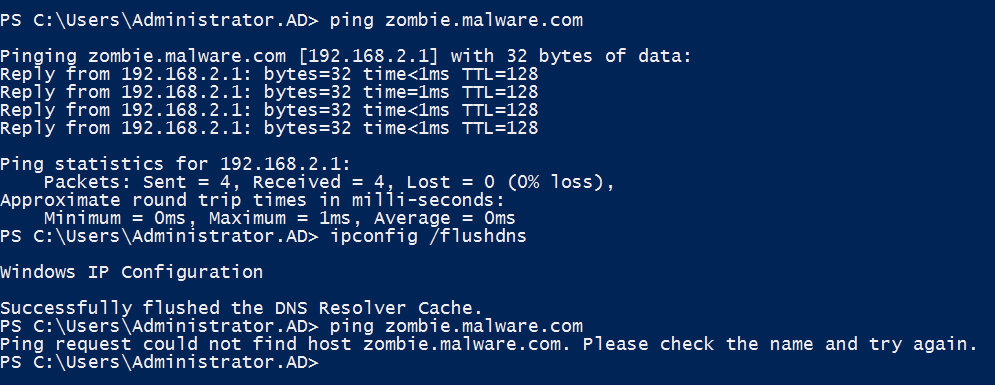
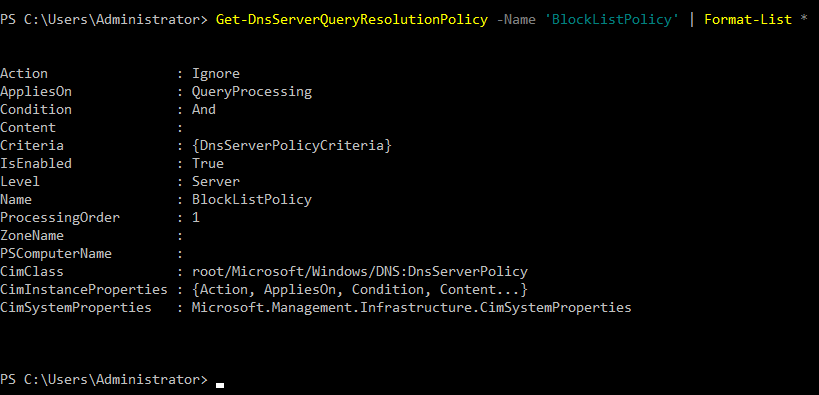
To get information about a policy, use the Get-DnsServerQueryResolutionPolicy cmdlet, as shown below:
Get-DnsServerQueryResolutionPolicy -Name 'BlockListPolicy' | Format-List *
Similarly, the Remove-DnsServerQueryResolutionPolicy cmdlet can be used to delete a policy completely:
Remove-DnsServerQueryResolutionPolicy -Name 'BlockListPolicy'
It’s also possible to create allow policies, that permit name resolution for one or more domains but block all others. To create an allow filter, just change the -Action parameter to ALLOW.
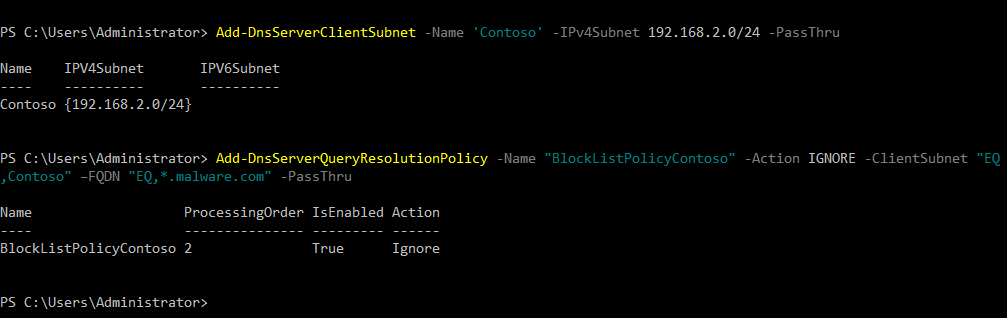
Now let’s create a more complex policy that blocks queries for malware.com from clients located in the contoso subnet. This requires two commands. The first, Add-DnsServerClientSubnet, defines a subnet on the DNS server. Then we use the Add-DnsServerQueryResolutionPolicy cmdlet as before, but add the -ClientSubnet parameter to specify that we’d like to block queries from a specific subnet.
Add-DnsServerClientSubnet -Name 'Contoso' -IPv4Subnet 192.168.2.0/24 Add-DnsServerQueryResolutionPolicy -Name ‘BlockListPolicyContoso’ -Action IGNORE -ClientSubnet "EQ,Contoso" –FQDN "EQ,*.malware.com"
In this article, I showed you how to apply filters to control name queries to DNS servers using DNS Policies in Windows Server 2016.




